Dynamic cryptography protection for virtual machines and key management method thereof
A technology of key management and key management information, which is applied to key distribution, can solve problems such as the inability to effectively realize cloud security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Hereinafter, exemplary embodiments of the present invention will be described with reference to the accompanying drawings. However, the scope of the present invention should not be construed as being limited to the following examples. The embodiments of the present invention are intended to more fully explain the present invention for those skilled in the art.
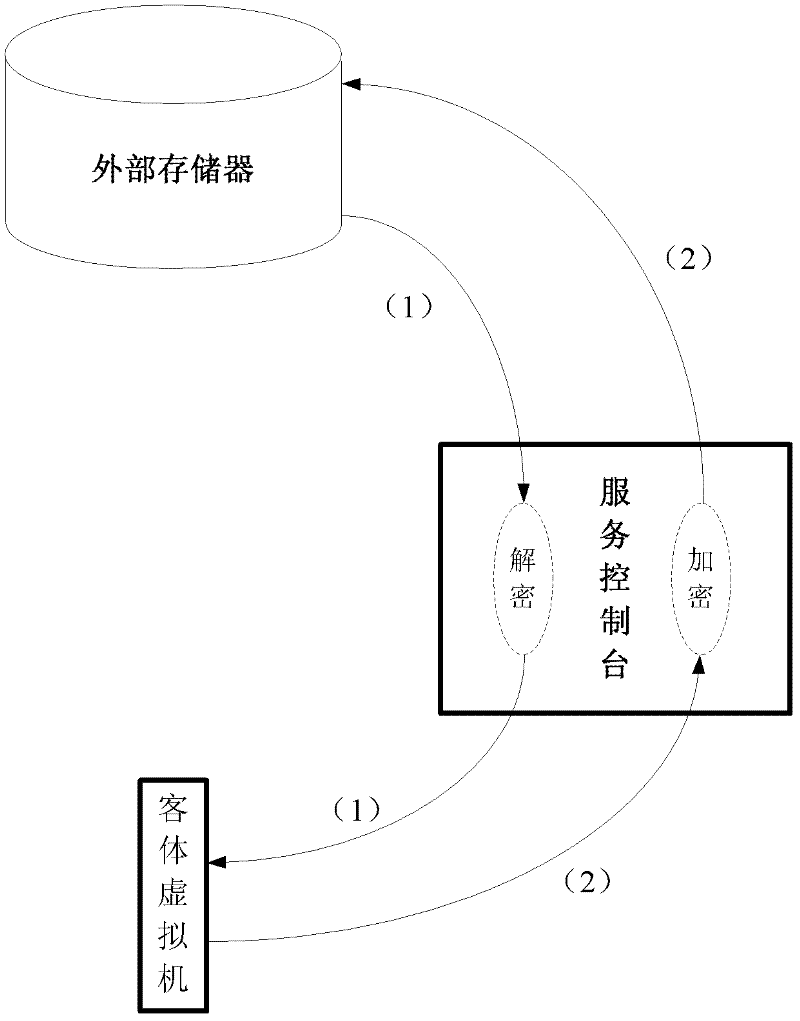
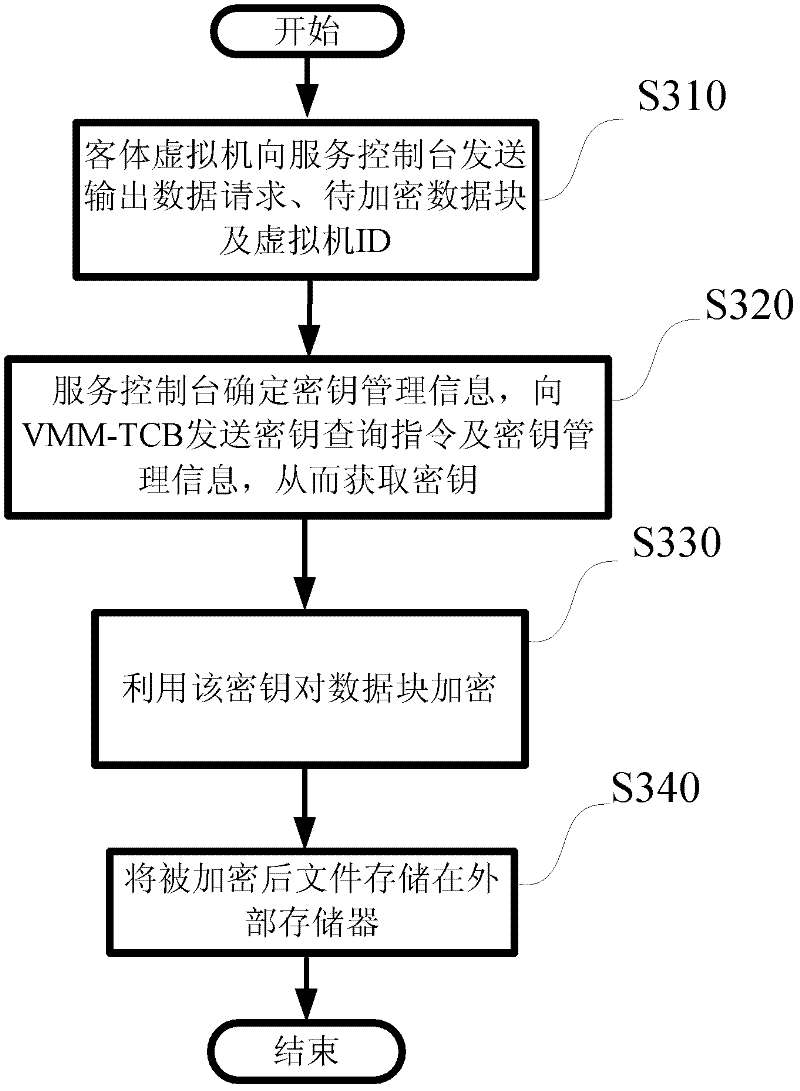
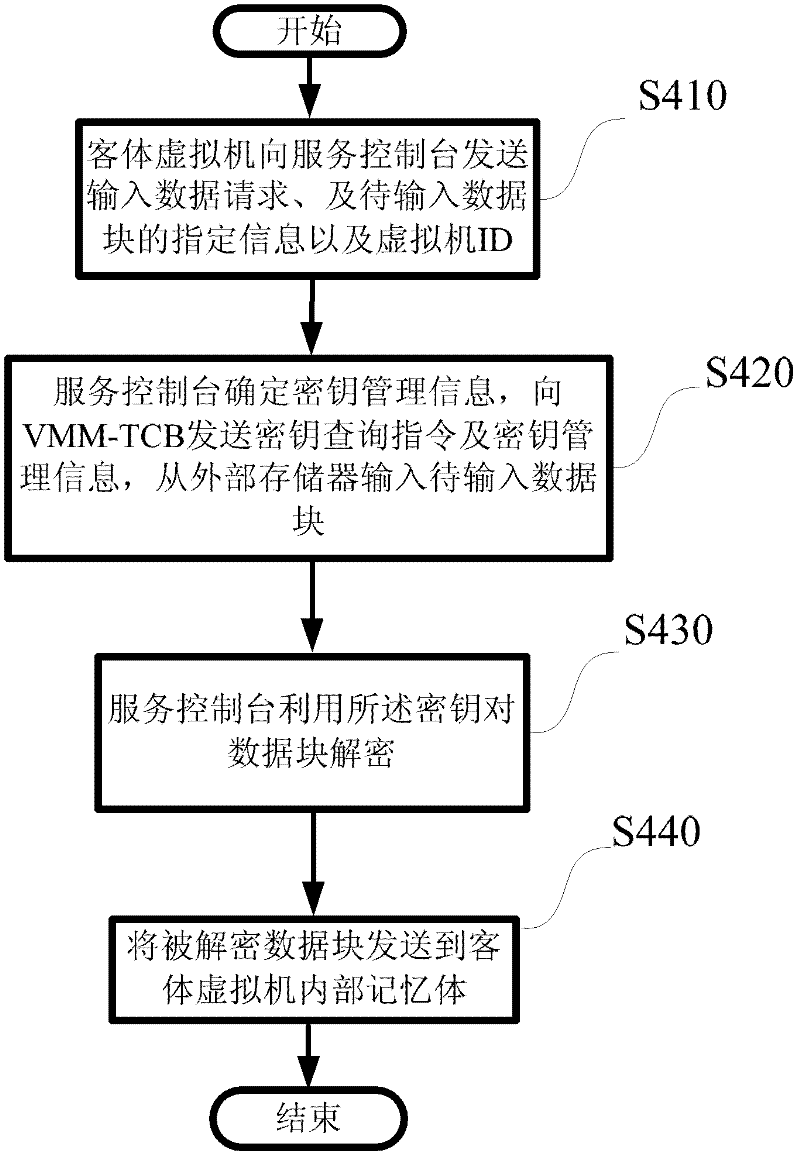
[0035] One embodiment of the invention relates to the generation of guest virtual machines. In this embodiment, first, the service console generates a key in its internal memory, and sends the key to the virtual machine monitor secondary trusted computing base, and the virtual machine monitor secondary trusted computing base (VMM-TCB) protects this key. Next, the service console generates the first data block of a guest virtual machine, the service console encrypts the data block, and then outputs or stores the encrypted data block to an external storage. The service console then generates a second block of d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com