Protection method for fusion integrity of sensor network data
A technology of integrity protection and sensor network, applied in electrical components, wireless communication, safety devices, etc., can solve problems such as large communication volume, achieve enhanced security, realize data fusion integrity detection, and implement simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
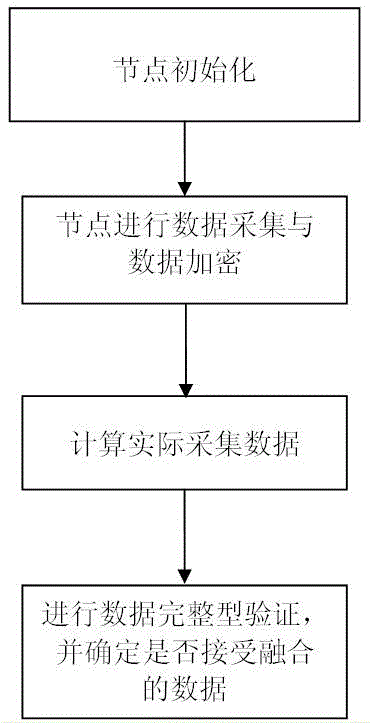
[0024] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
[0025] For a sensor network with a total number of nodes of N, there are three types of nodes, which are final sink nodes, intermediate fusion nodes and leaf nodes. The intermediate fusion node is responsible for fusing the data received from the leaf nodes and the data collected by itself, and then passing it up to its parent node, and at the same time passing down the query request of its parent node. Leaf nodes are only responsible for collecting data and passing it to their parent nodes.
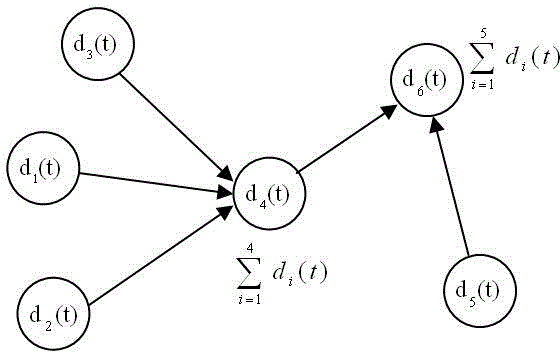
[0026] figure 1 It is a schematic diagram of data collection and fusion for intermediate fusion nodes. The data collected by the nodes at time t in the figure are respectively d 1 (t), d 2 (t), d 3 (t), d 4 (t), d 5 (t) and d 6 (t), we define the data fusion function as the summation function (sum), record Many other typical data fusion functions, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com