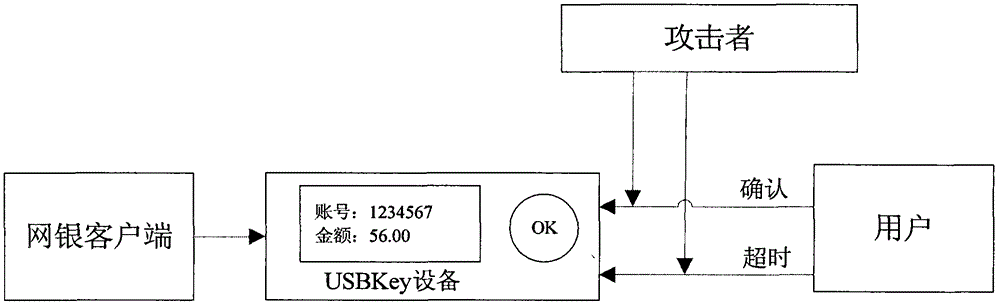
Method for realizing follow attack prevention in device with data sign determining function
A data signature and function technology, applied in digital data authentication, electrical components, transmission systems, etc., can solve problems such as follower attacks, and achieve the effect of ensuring transaction security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in detail below in conjunction with the accompanying drawings and specific examples.
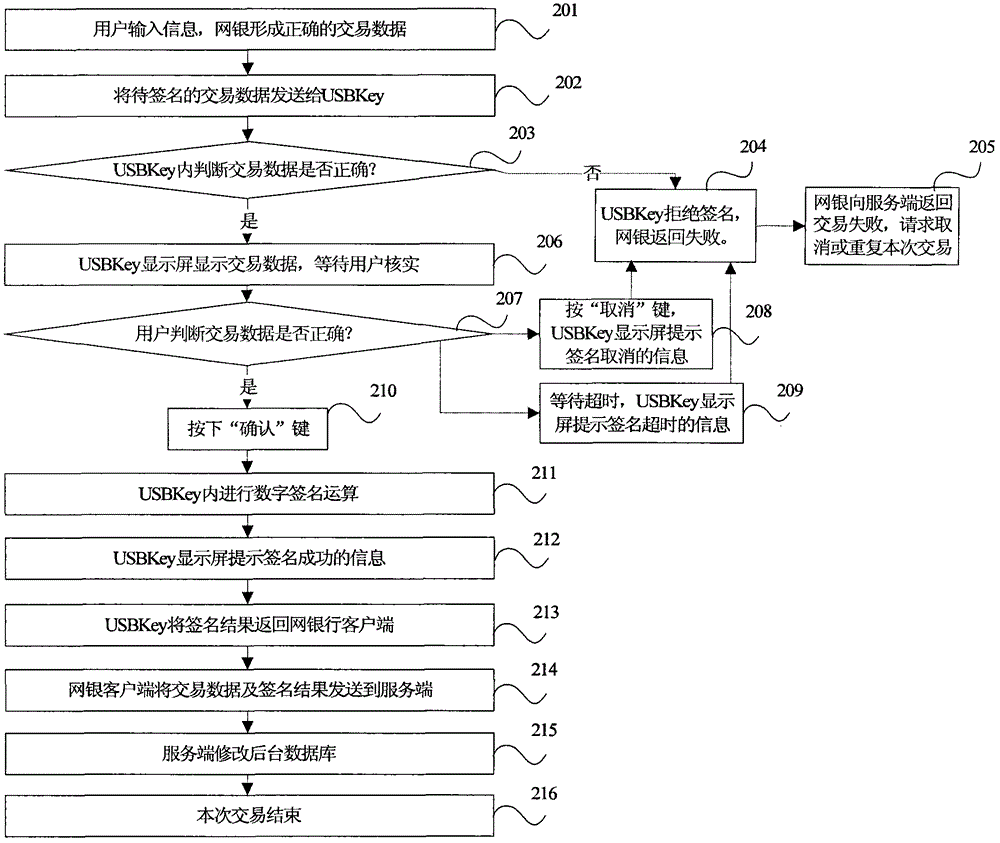
[0027] figure 2 A flow chart of a method for preventing follower attacks for a device with the function of confirming data signatures for online banking transactions. like figure 2 As shown in , combined with the transaction process, describe in detail where the attacker is attacked in this process, and how the security of the transaction process is reflected after the anti-following attack measures are adopted.
[0028] When anti-following attack measures are not adopted, the online banking transaction process is as follows.
[0029] Step 201): The user inputs information, and the online banking client forms correct transaction data template information.
[0030] Step 202): The online banking client sends the transaction data template information to be signed to the USBKey.
[0031] Step 203): It is judged in the USBKey whether the transa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com