Method for verifying verification code and server
A verification code and server technology, applied to electrical components, transmission systems, etc., can solve problems such as difficult to balance security and usability, and achieve the effects of improving anti-cracking ability, easy identification, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
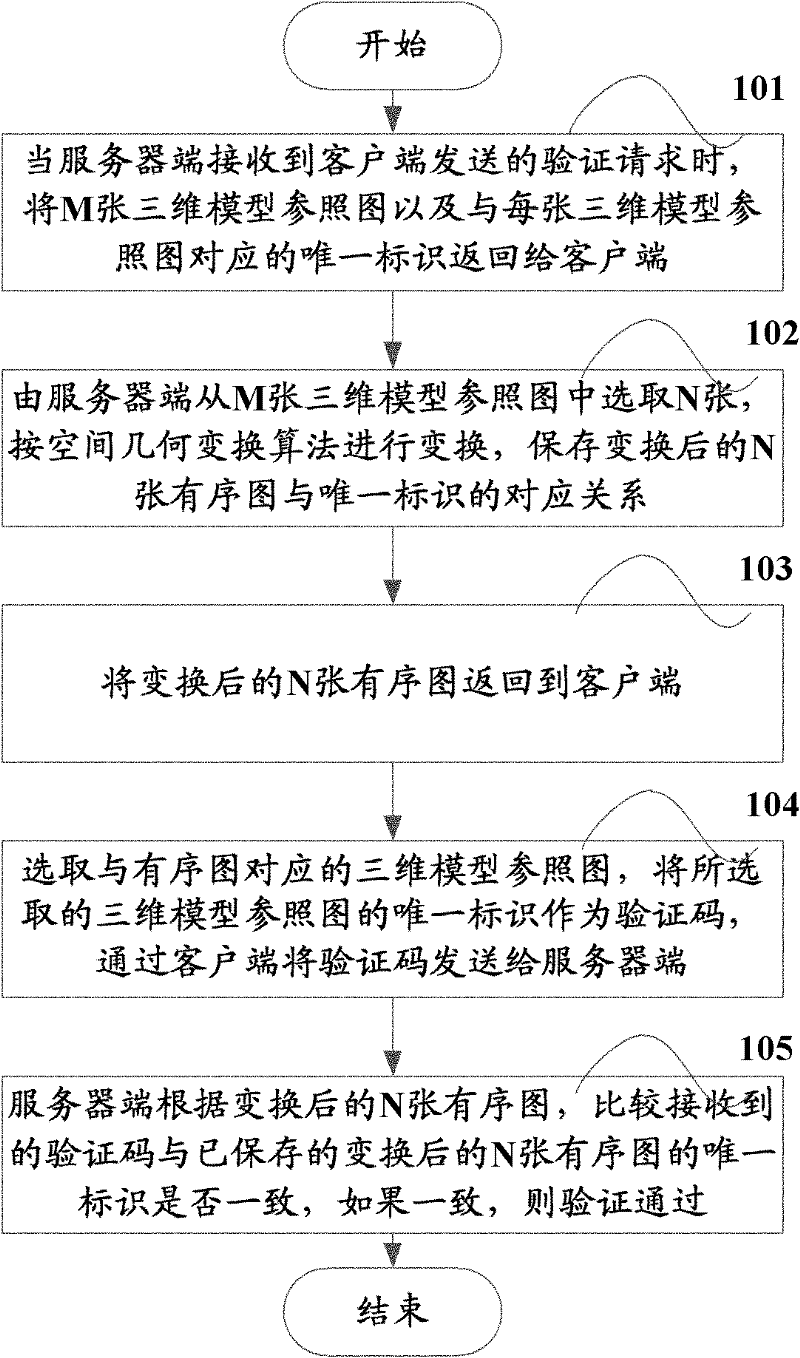
[0024] figure 1 It is a schematic flow chart of a method for verifying a verification code in the present invention, including the following steps:
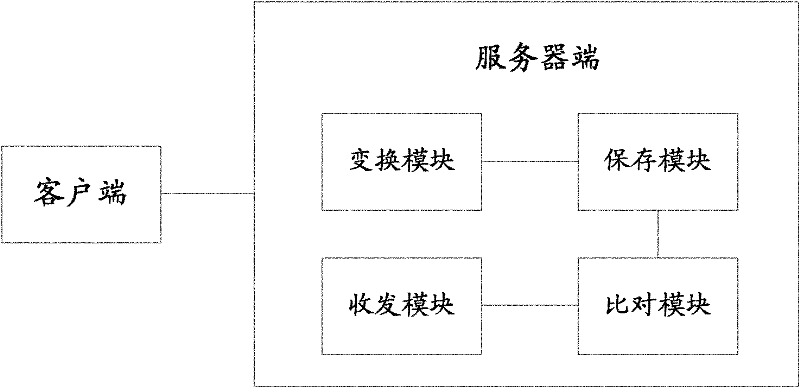
[0025] In step 101, when the server receives the verification request from the client, it returns M 3D model reference images and the unique identifier corresponding to each 3D model reference image to the client, where M is a positive integer greater than 0.
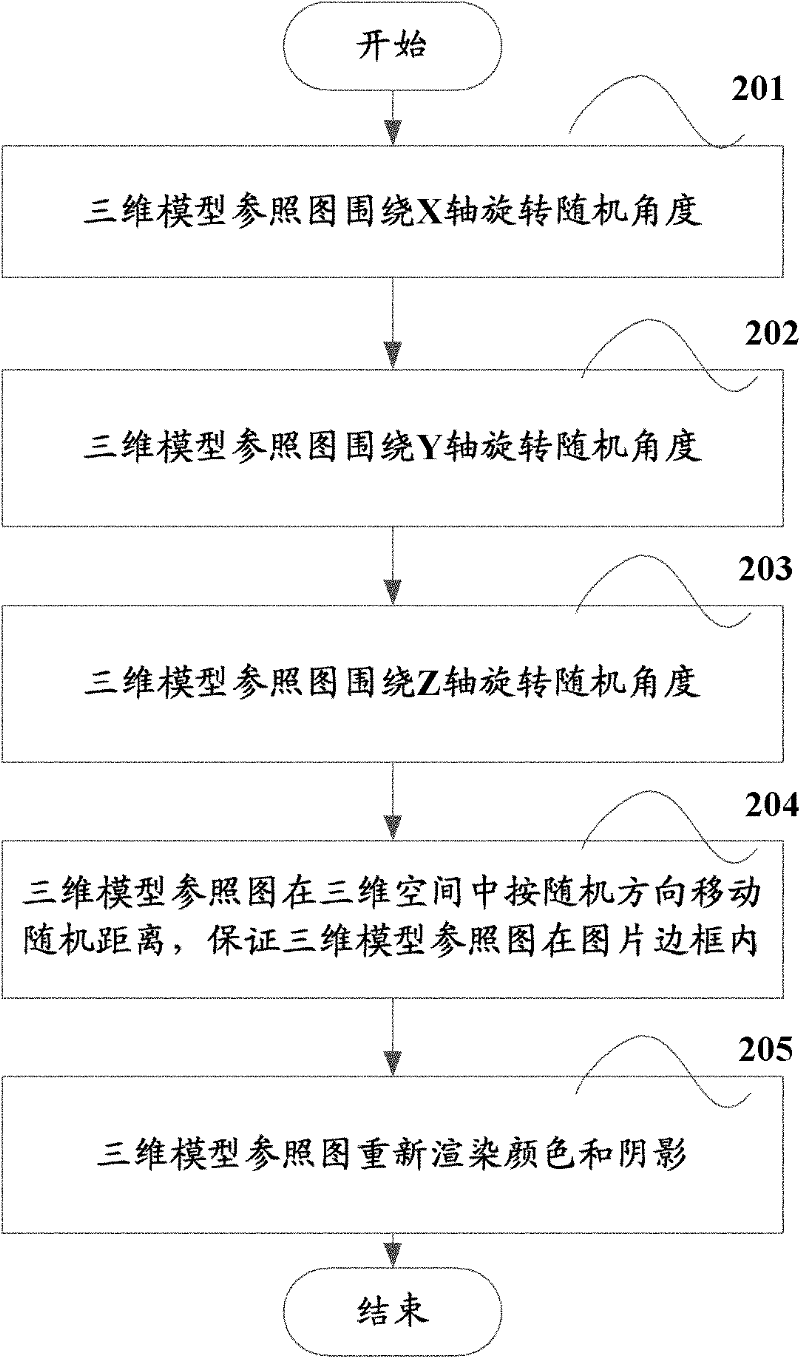
[0026] The 3D model reference graph is a graph obtained by performing 3D modeling on the item in 3D space. The items may be common items such as airplanes, vases, dogs, etc. in the real world. 3D modeling is to build models with 3D geometry and surfaces.
[0027] The unique identifier refers to the different numbers, letters, or combinations of numbers and letters assigned by the server to d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com