Automatic malicious code analysis method and system
A malicious code and automatic analysis technology, applied in the field of malicious code automatic analysis systems, can solve the problems of inability to analyze malicious code, prevent unknown malicious code attacks, and lag in signature extraction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described below in conjunction with the accompanying drawings.
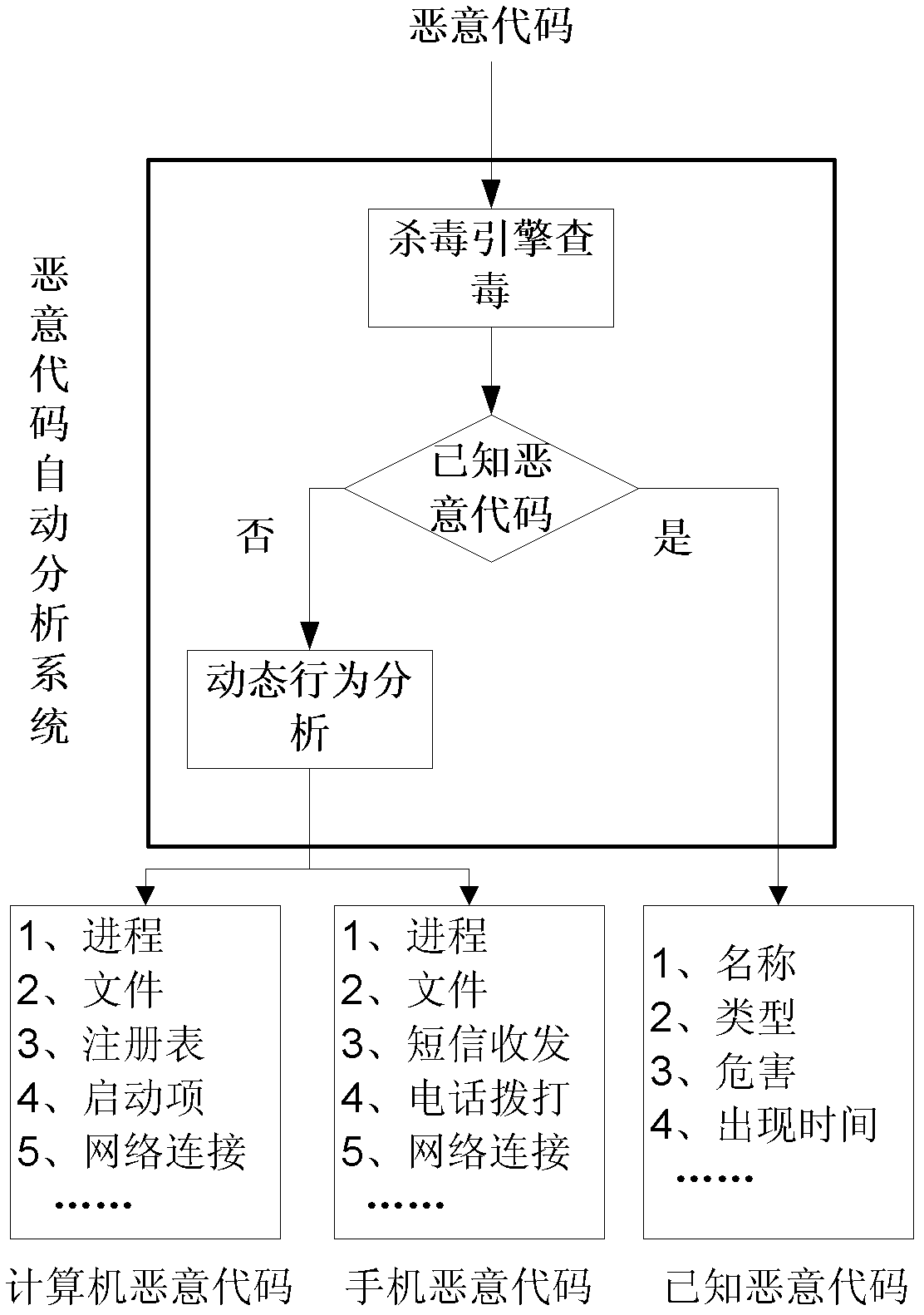
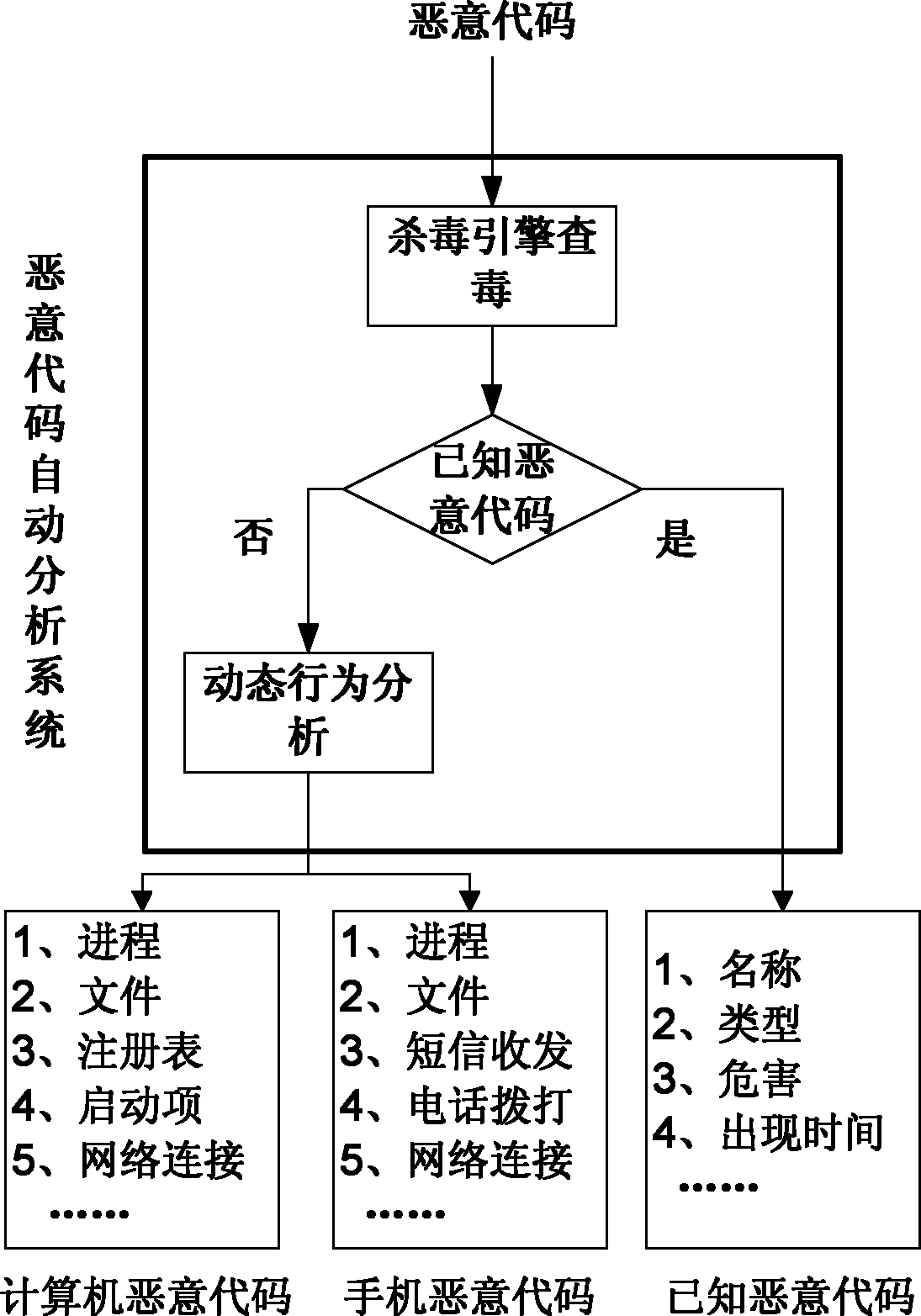
[0017] The malware analysis process goes through three steps:
[0018] First, perform sample matching, calculate the HASH value of the sample file, and compare it with the previously analyzed samples to determine whether it has been analyzed. If it has been analyzed, it will directly return to the previous analysis results to shorten the analysis time.
[0019] Then, for unanalyzed samples, the antivirus engine is called to perform virus scanning to determine whether the malicious code is known malicious code. For known malicious code, information such as its malicious code name, type, harm level, etc. can be obtained.
[0020] Finally, for unknown malicious code samples, a more comprehensive dynamic analysis is carried out, and malicious codes are divided into computer malicious codes and mobile phone malicious codes according to the different platforms on which the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com