Method for performing identity authentication on mobile terminal
A mobile terminal and identity authentication technology, applied in electrical components, wireless communication, security devices, etc., can solve the problems of attack, tampering and forgery, single method, etc., and achieve the effect of ensuring security, improving speed and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below with reference to the accompanying drawings.
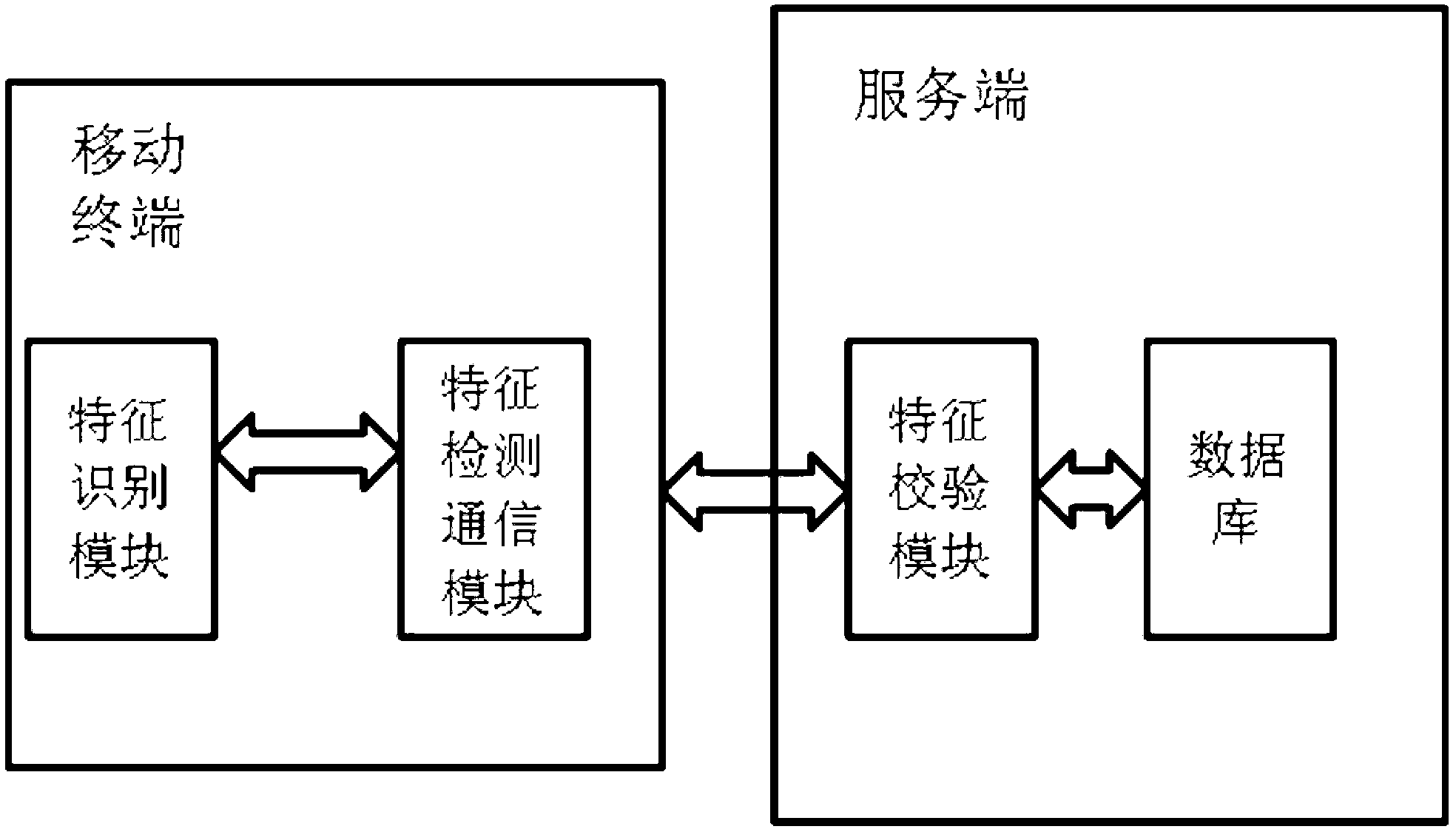
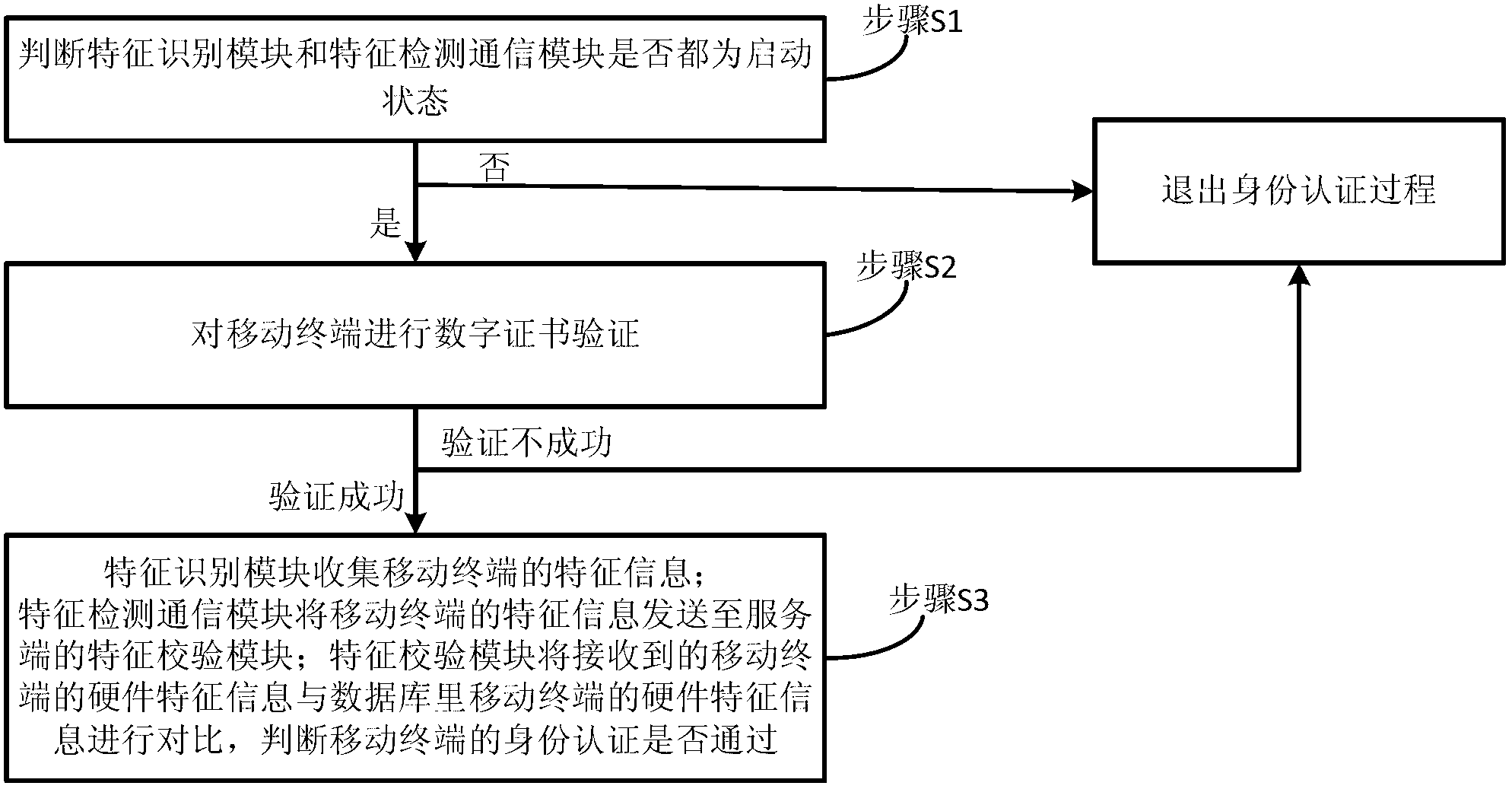
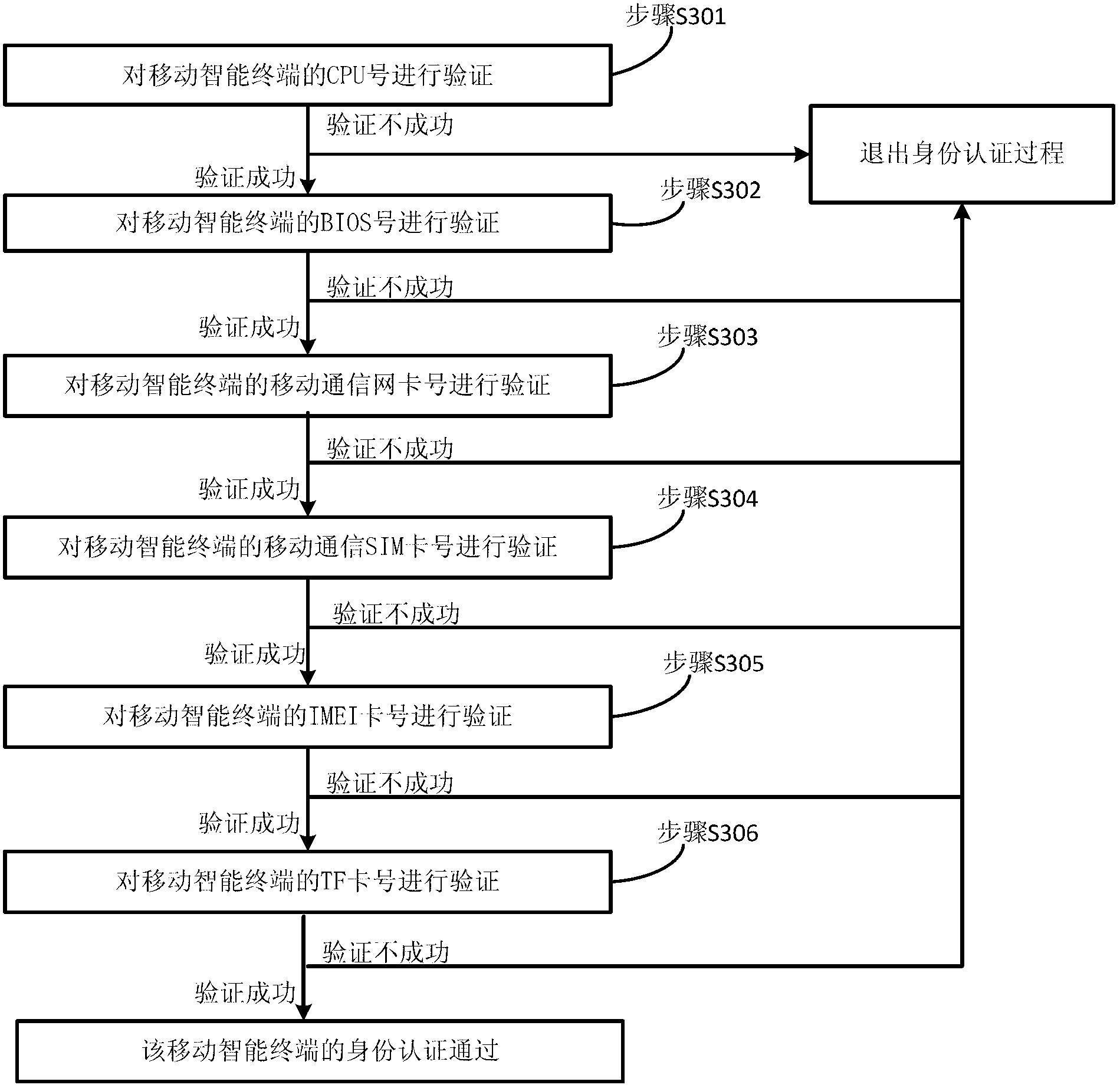
[0040] A method for identity authentication of a mobile terminal provided by the present invention is applied to a mobile terminal and a server. The schematic diagram of the internal structure of the embodiment of the mobile terminal and the server is as follows: figure 1 As shown, the flow chart of the mobile terminal identity authentication method is as follows figure 2 shown, by figure 1 and figure 2 It can be seen that the mobile terminal includes a feature identification module and a feature detection communication module, the server includes a feature verification module and a database, and the method for identity authentication of the mobile terminal includes the following steps:
[0041] In step S1, it is judged whether the feature identification module and the feature detection communication module are both in the activated state, and if so, step S2 is perfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com