Web system malicious polyphonic ringtone ordering preventing method and server
A server and ring tone technology, applied in the communication field, can solve problems such as weak control ability, inability to meet the quality and security requirements of CRBT web services, and achieve the effect of improving security and preventing repeated sending
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
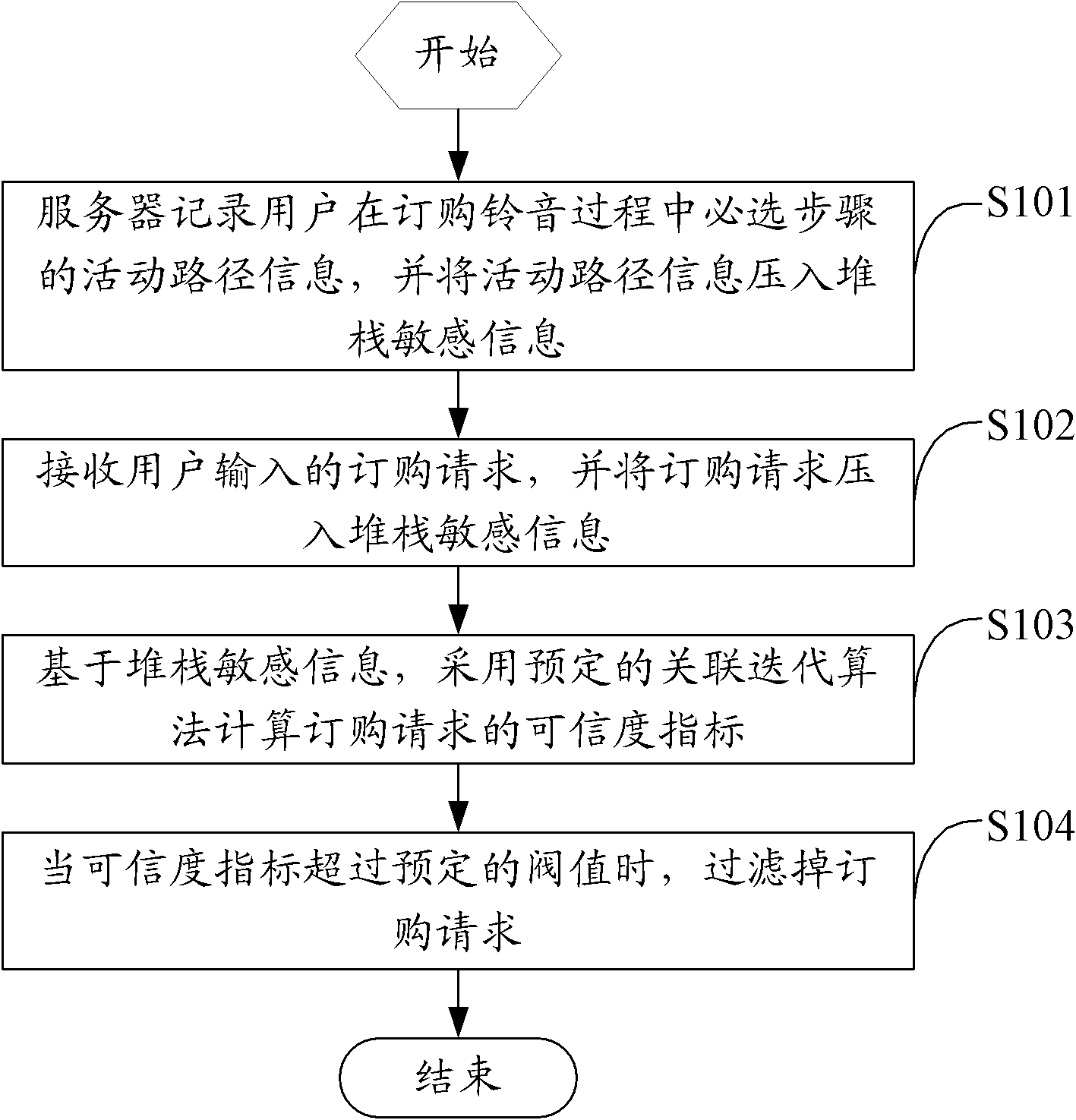
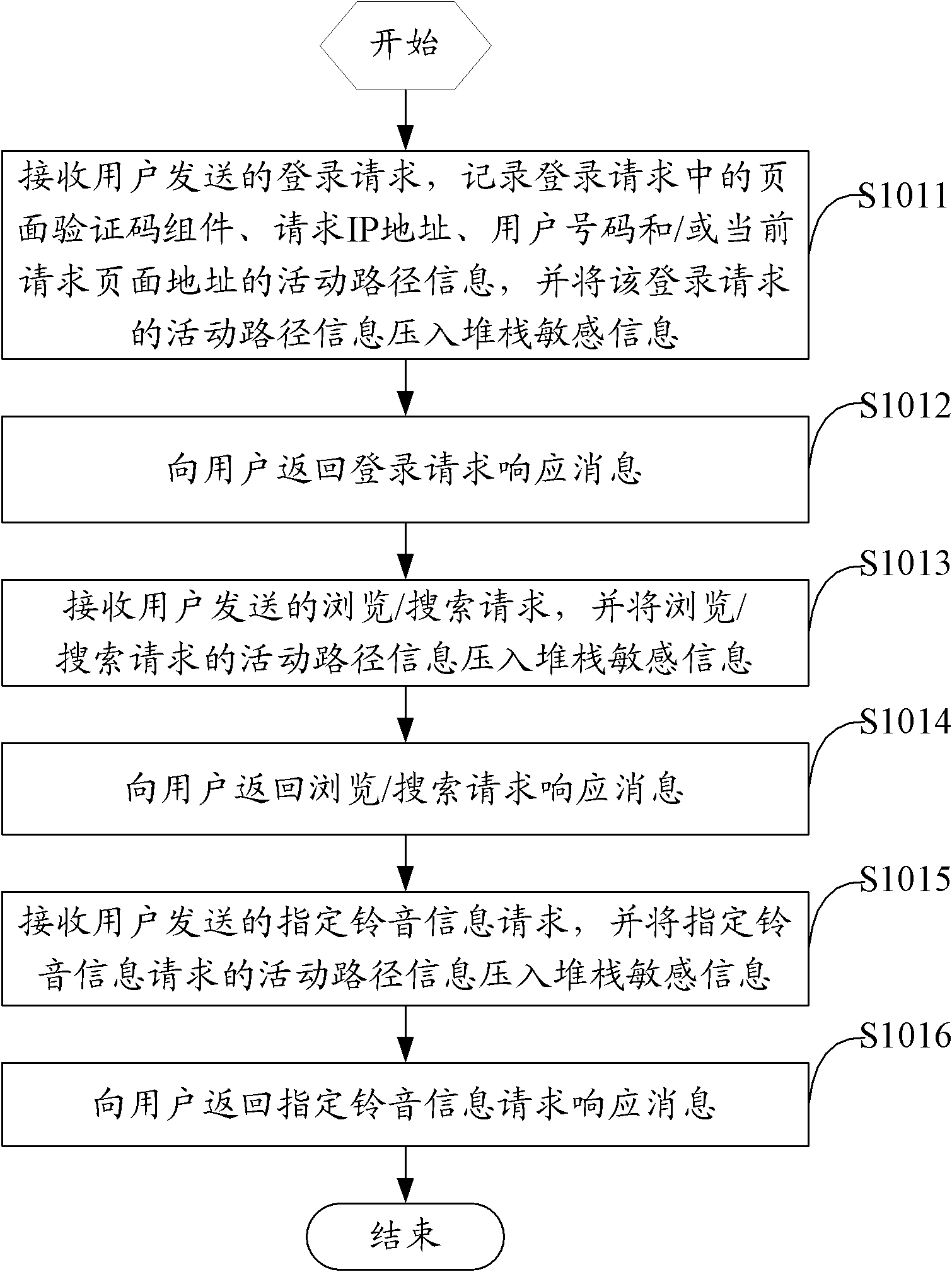
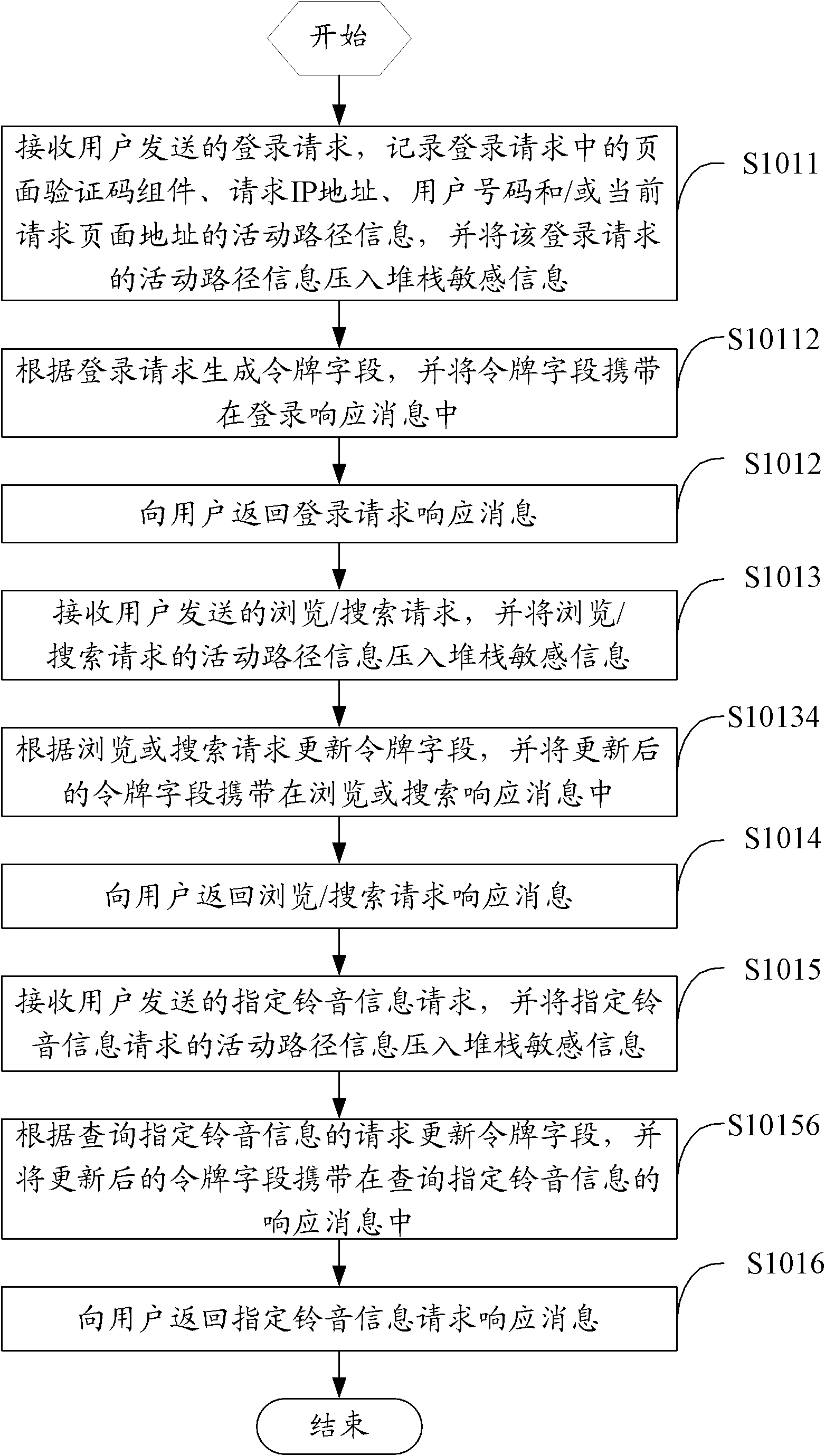
[0036] The main idea of the solution in the embodiment of the present invention is: because the malicious ordering behavior of ringtones mostly presents the following main features: abnormality in behavior, such as behavior that ordinary users rarely or almost impossible to do; regularity in behavior, such as the same Or be the operating time cycle of a certain sequence; The regularity on the data, such as the natural sequence relationship of all ordered ring tone numbers, etc., therefore, the present embodiment aims at the above situation, and the program simulation robot pretends to be a legitimate user to log in and cause In order to solve the problem of ordering malicious ring tones, the path tracking technology of the stack mechanism is introduced; for malicious ring tones ordered by browser address access and legitimate login users through multiple submissions, a request filter similar to the token ring mechanism is introduced to prevent ring tones Effectively control t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com