Method for vehicle-mounted Ad Hoc network based on improved AODV (Ad Hoc Ondemand Distance Vector) protocol
A protocol and network technology, applied in the field of vehicle-mounted Ad Hoc network based on the improved AODV protocol, which can solve the problem that the AODV protocol does not have a good solution, the selection of stable routes and delays have not been studied in depth, and the control overhead has not been considered. problem, to achieve the effect of improving routing reliability and data transmission success rate, preventing flood broadcast, and reducing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Below in conjunction with accompanying drawing the embodiment of the present invention is described in detail: present embodiment is implemented on the premise of the method of the present invention, has provided detailed embodiment and concrete operation process, but protection scope of the present invention is not limited to following the embodiment.
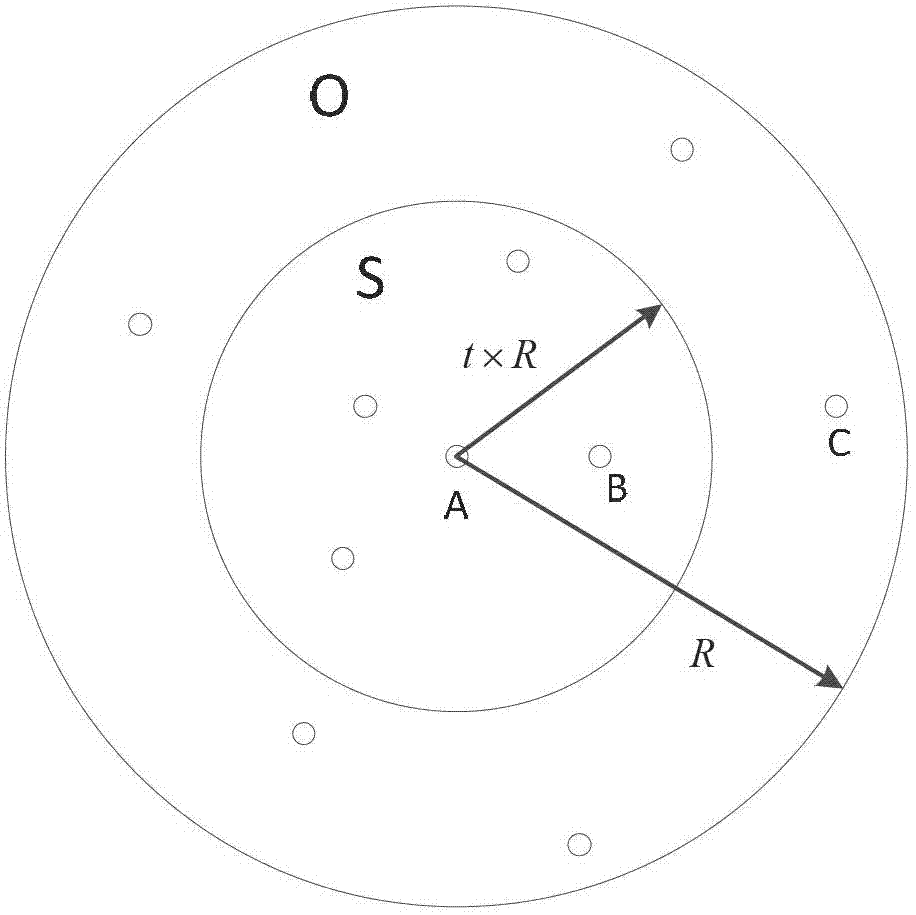
[0031] The scene setting of this embodiment takes the vehicle-mounted Ad Hoc network on a highway as an example.
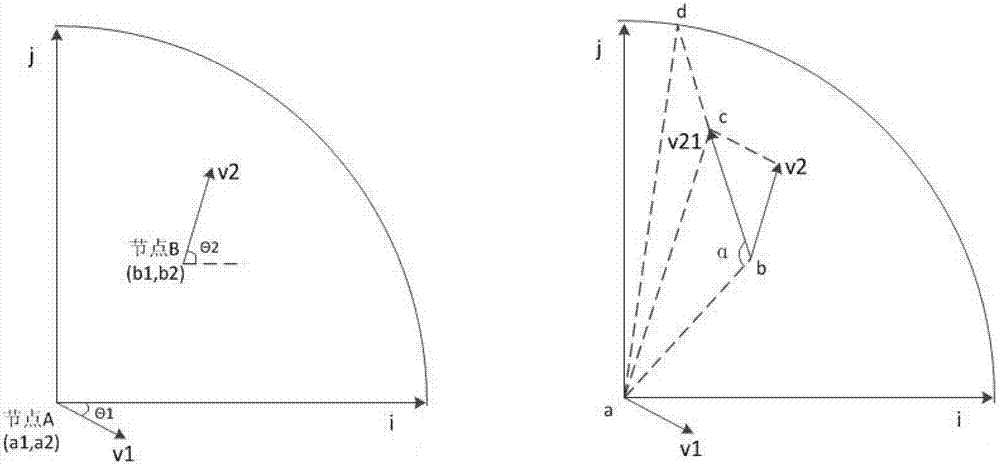
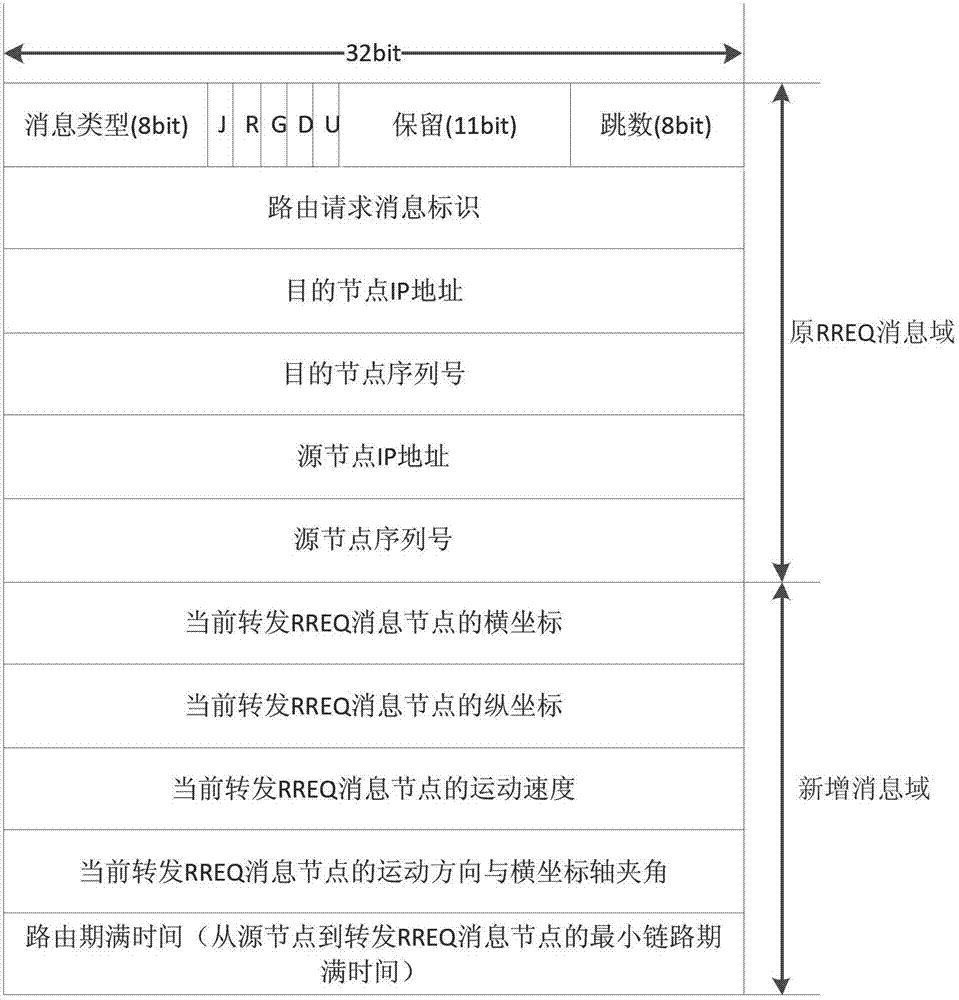
[0032] Step 1: When the source node has data to send to the destination node, a RREQ message will be generated, and the source node will add information such as its position, speed, direction, and route expiration time to the RREQ message and send it to neighboring nodes.
[0033] The source node adding information such as its own position, speed, direction, and route expiration time to the RREQ message refers to making certain modifications to the format of the RREQ message in order to meet the needs of st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com