Hardware Trojan horse detection system based on puf
A technology for hardware Trojan detection and design files, which is applied in the fields of instruments, calculations, electrical digital data processing, etc., and can solve problems such as high requirements, great difficulty, and insufficient cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
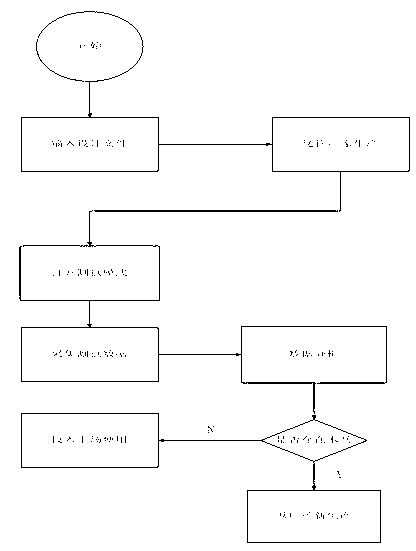
[0033] Such as figure 1 As shown, the method includes:
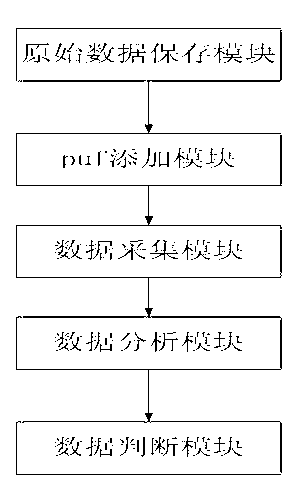
[0034] Step 1, the user inputs the original IC design file into the original data saving module and saves it;
[0035] Step 2, the user chooses to add puf to several modules of the IC in the original IC design file through the puf adding module;
[0036] Step 3, the user sends the IC design file with puf added to the manufacturer for production, and in the test mode, the IC sample produced by the manufacturer according to the IC design file with puf added by the user is collected through the data acquisition module, and the collected The data is stored in the database; the collected data is: the feature vector generated by the PUF detection module.
[0037] Step 4, the collected data stored in the database is analyzed by the data analysis module, and a judgment result is output;
[0038] Step 5, the user judges the original data according to the data judging module to determine whether the original IC design in the or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com