System-asset-based software security requirement analysis method
A technology for demand analysis and software security, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of low efficiency, consume a lot of time and energy, and use high thresholds, and achieve the goal of improving development efficiency, reducing development costs, The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The specific implementation, structure, features and effects provided by the present invention will be described in detail below in conjunction with the accompanying drawings and preferred embodiments.
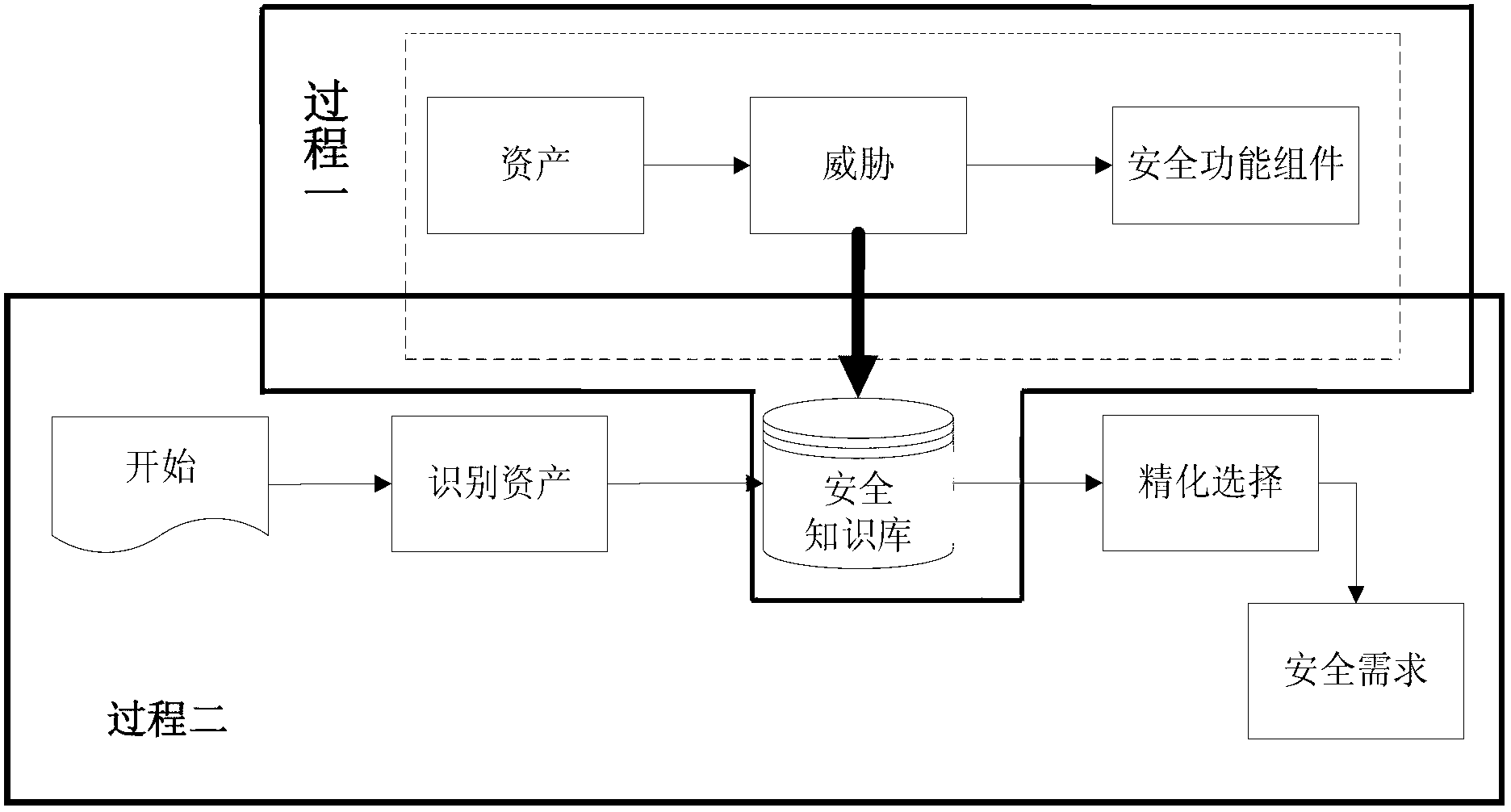
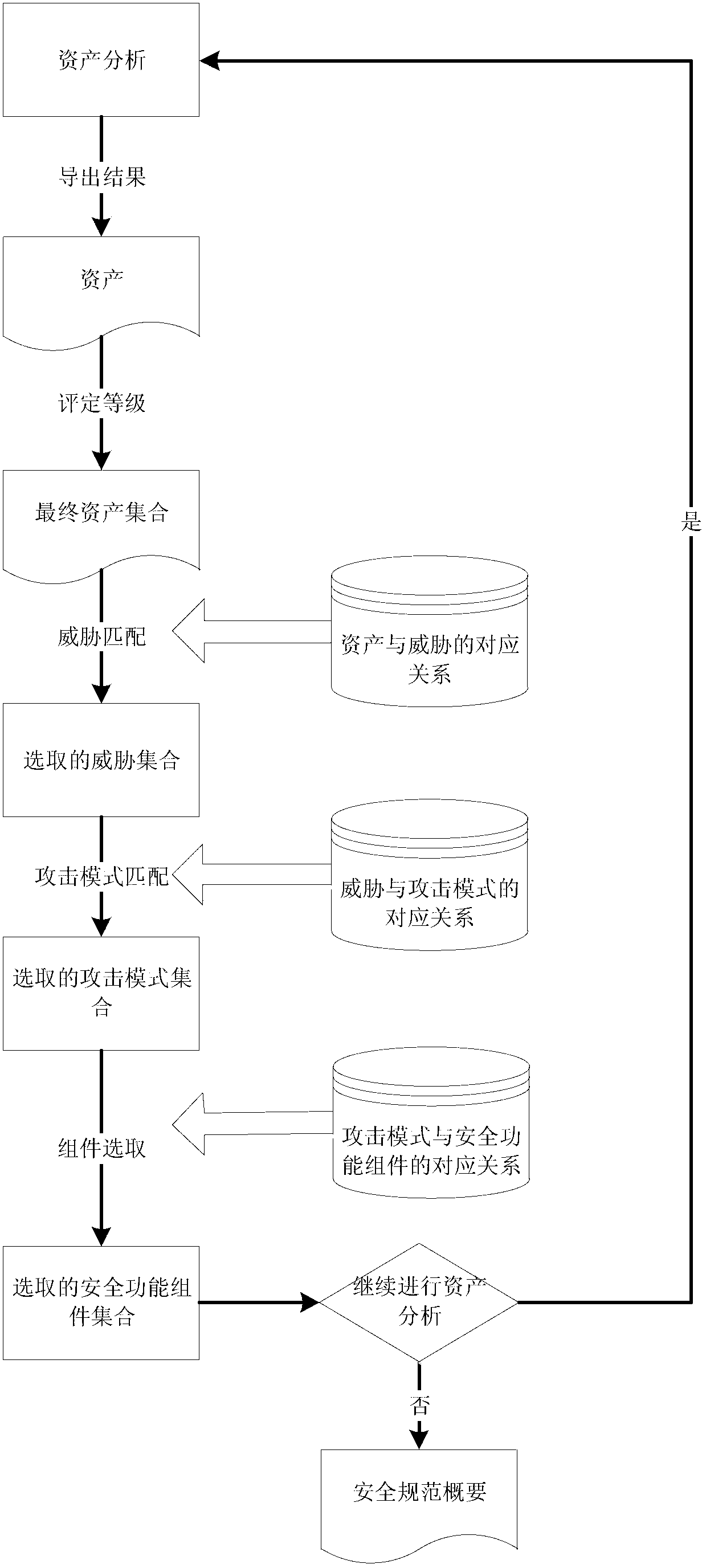
[0023] The system principle of the present invention, such as figure 1 As shown, it includes two processes. Process 1: First, the establishment of the corresponding relationship between the system asset category and the security function component, and the establishment of the corresponding relationship between the asset and the security function component. This process is also After the construction process of the knowledge base is completed, it can be used as empirical knowledge in each specific development;
[0024] The process includes the following steps:
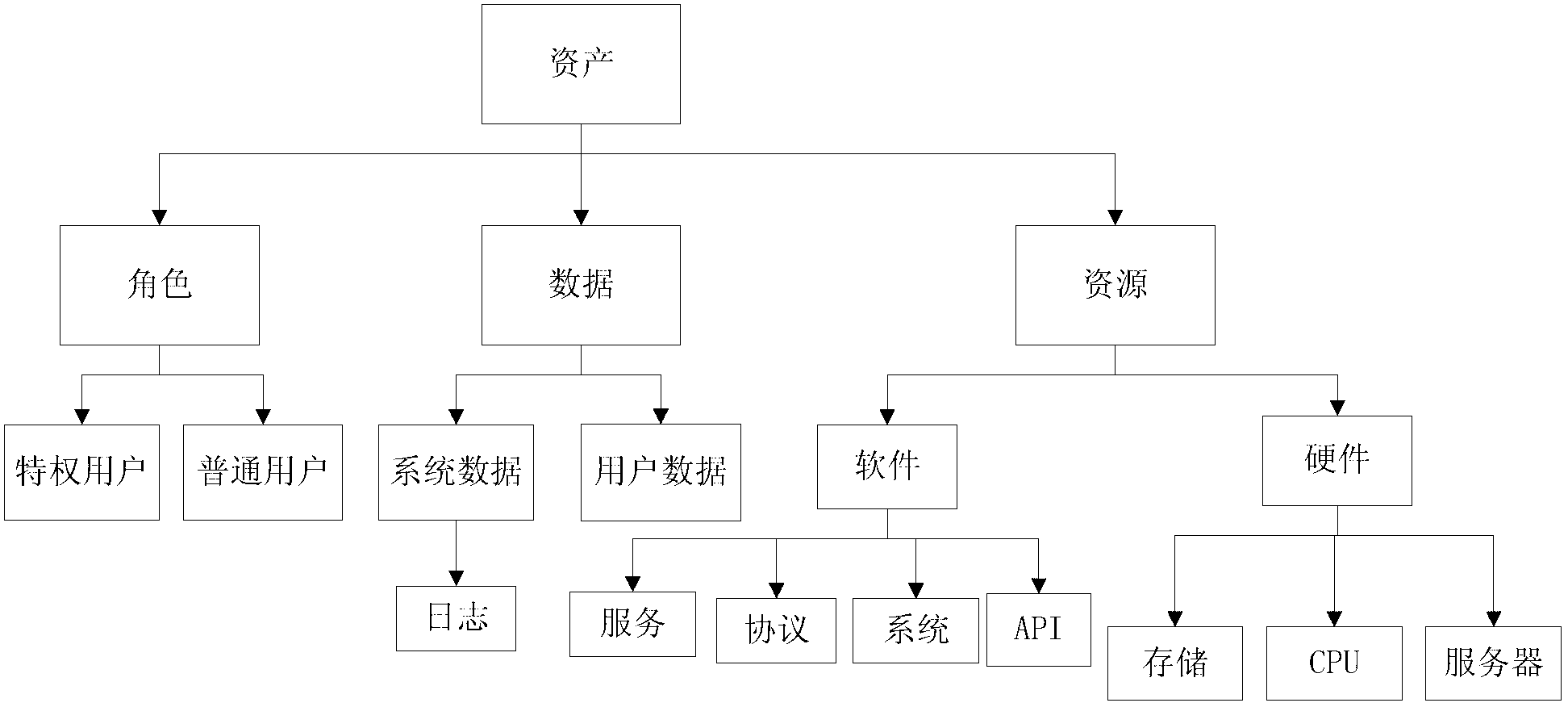
[0025] 1-1. Classification of system assets, threats, and attack modes
[0026] System assets are objects that need to be protected in the system or entities that are closely related to system functions. A th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com