Method and system for realizing source looped network protection
A ring network and link protection technology, applied in the field of data communication, can solve problems such as unfavorable topology changes and heavy configuration workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
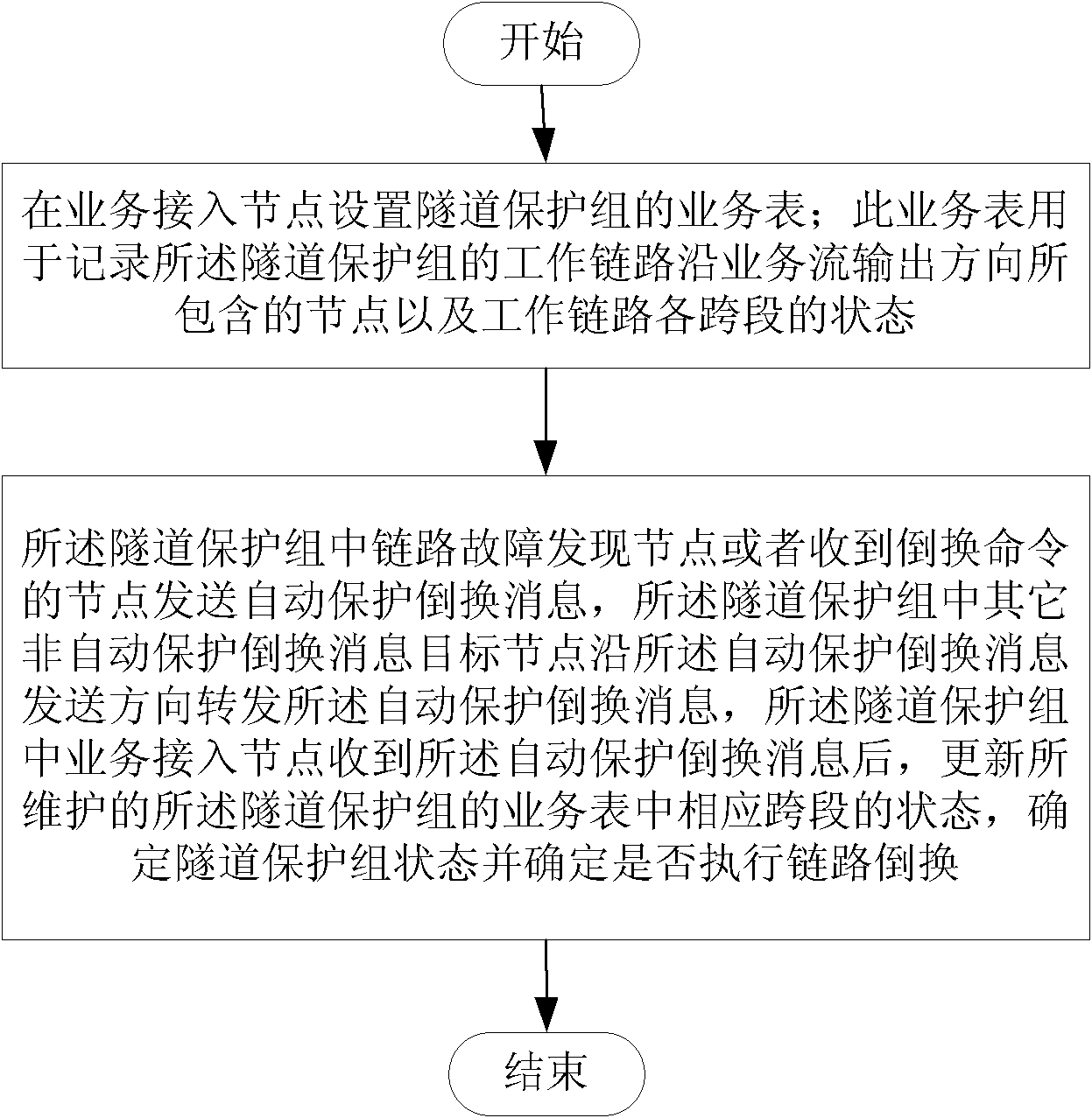
[0049] Link failure recovery discovery node detects that the link failure is restored, and periodically sends automatic protection switching messages to adjacent nodes along the east and west ports to match the service table. If the service table is not matched, it means that the node is non-service access node, no other operations are performed. If the service table is matched and the source node and destination node identifiers of the automatic protection switching message are matched, it means that this node is a service access node, and the service table is updated and the wait is started. A recovery (Wait to Restore, WTR for short) timer.
[0050] After the non-link fault recovery discovery node receives the automatic protection switching message sent by other nodes, it judges whether the node is the destination node of the automatic protection switching message. If it is, it does not forward the message; direction forward this message. Further, match the service table. ...
Embodiment 3
[0055] When the link switching is triggered by the protocol switching command, after receiving the protocol switching command, the receiving node of the protocol switching command will periodically send the automatic protection switching message to the adjacent node along the east and west ports to match the service table. The service table indicates that this node is a non-service access node, and no other operations are performed. If the service table is matched and the identification of the source node and the destination node of the automatic protection switching message is matched, it indicates that this node is a service access node. Then update the business table and decide to switch the protection group.
[0056] After receiving the automatic protection switching message sent by other nodes, the receiving node of the non-protocol switching command judges whether the node is the destination node of the automatic protection switching message. Forward this message. Furth...
specific Embodiment 1
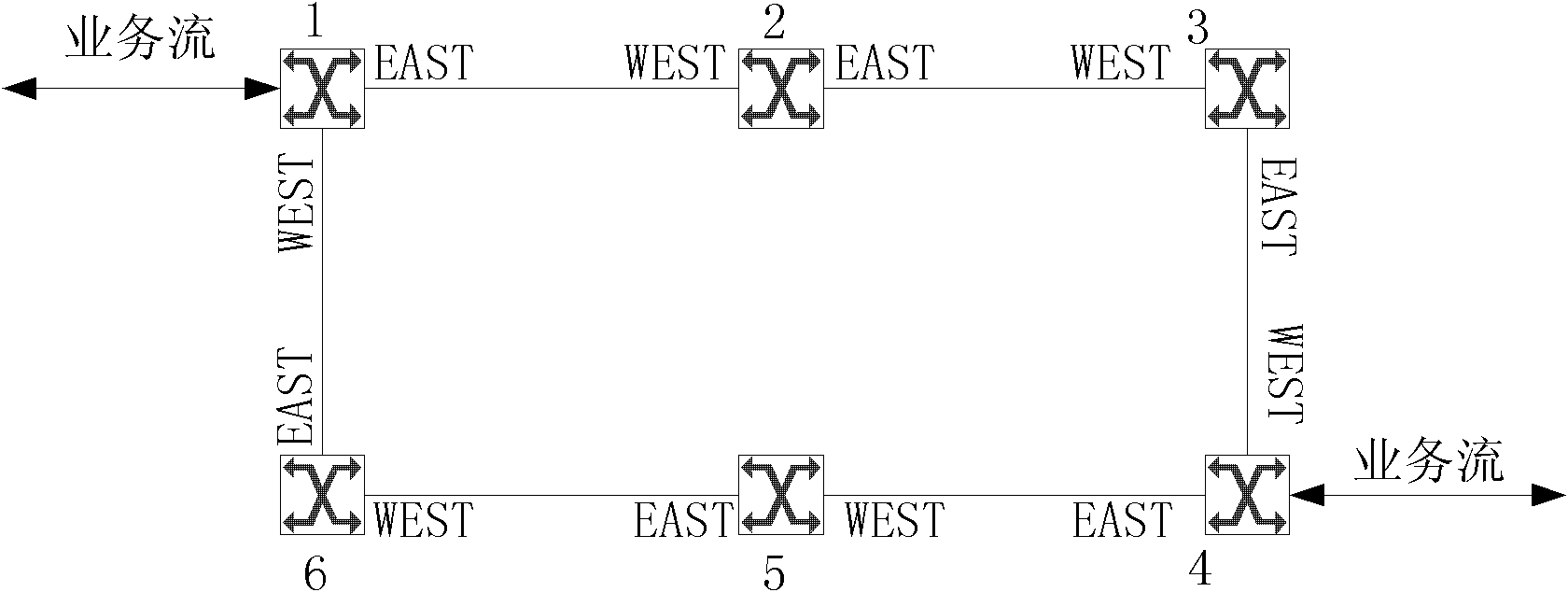
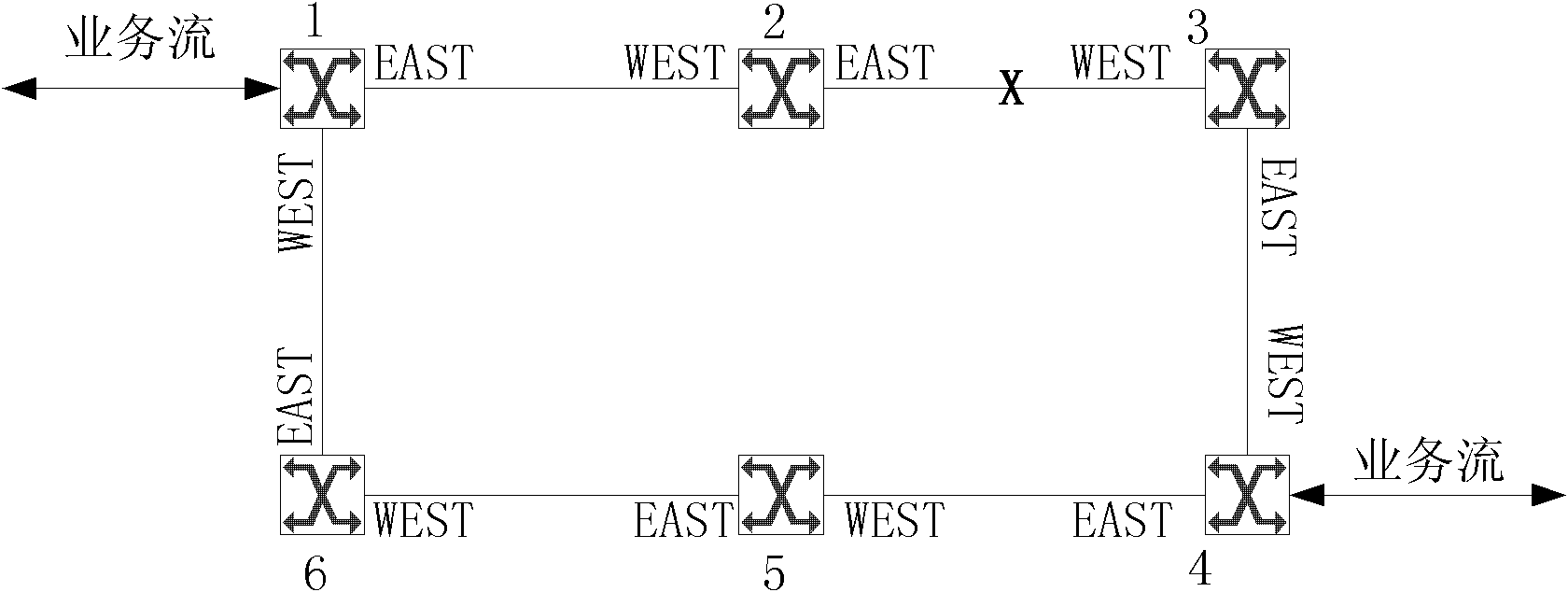
[0064] Such as Figure 3b As shown, a fault occurs between the working link node 2 and node 3.
[0065] The processing methods for nodes along the WEST direction of the automatic protection switching message include:
[0066]Link fault discovery After node 2 detects a link fault, it periodically sends APS messages to adjacent nodes along the WEST direction port on the ring. The APS message indicates that the destination node is node 3, and the source node is node 2, node 2, and node 3. The state of the cross-segment between is the failure state (SF), and the source node and the destination node are matched according to the business table, and no other processing is performed if the match is unsuccessful.
[0067] After the non-link fault detection node 1 receives the APS message sent by node 2, it judges whether this node is the destination node of the automatic protection switching message. For node matching, both the source node and the destination node are in the service ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com