Virtual computer system, virtual computer control method, virtual computer control program, and semiconductor integrated circuit
A virtual computer and program technology, applied in program control design, computer security device, computing, etc., can solve problems such as authenticated application program attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0042]
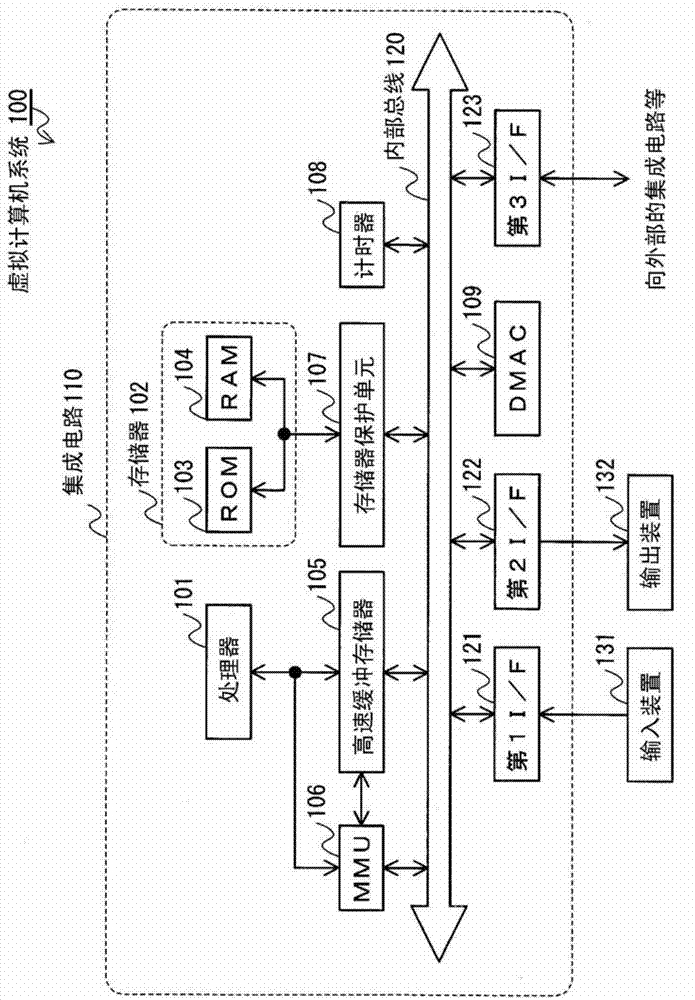
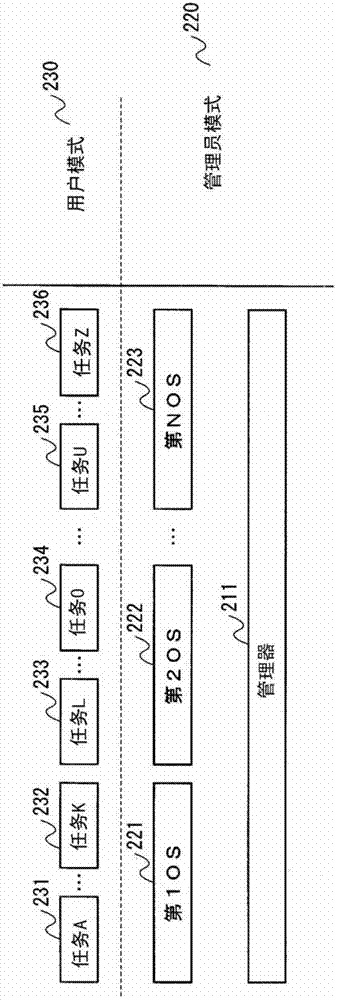
[0043] Hereinafter, as an embodiment of the virtual computer system of the present invention, a virtual computer system including a processor having a user mode for executing an application program and a supervisor higher than the user mode will be described. In the two program execution modes, the manager executed in the supervisor mode of the processor performs time-sharing execution control on a plurality of operating systems executed in the supervisor mode of the processor.
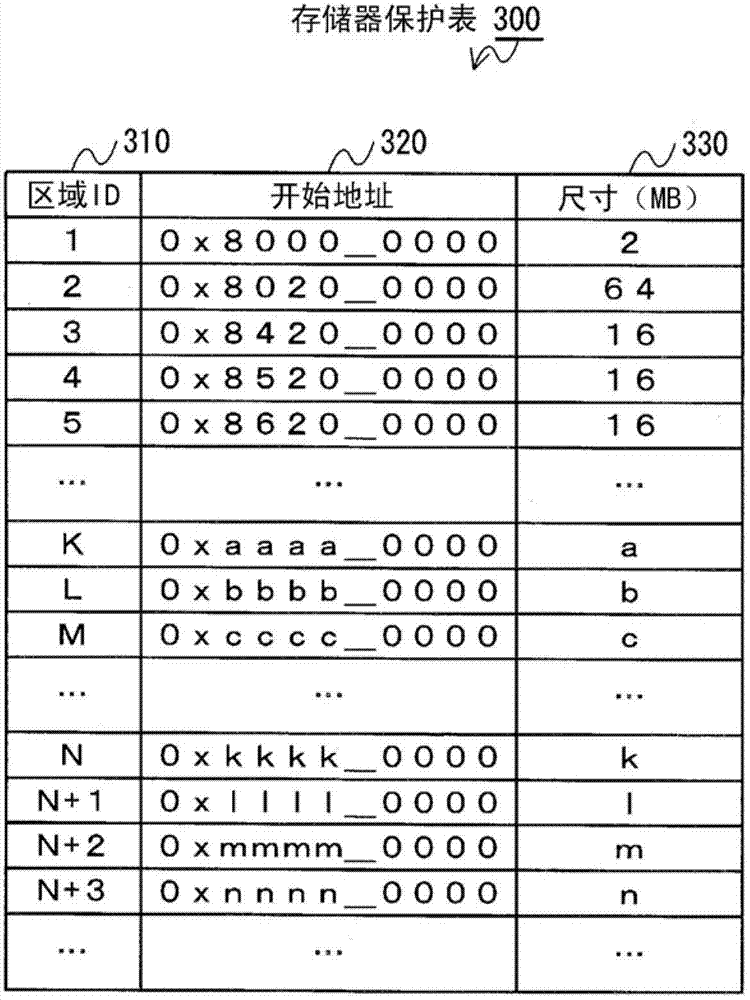
[0044] This virtual computer system includes, in addition to the processor, a memory protection unit that controls access from the virtual computer to the storage area of the memory. Furthermore, the manager executed by the processor cooperates with the memory protection unit to control access to the storage area of the memory so that access to a predetermined area is prohibited for each virtual computer.
[0045] Therefore, each virtual computer executed by the virtual computer system ...
Embodiment approach 2
[0201]
[0202] Hereinafter, as an embodiment of the virtual computer system of the present invention, a virtual computer system 1500 in which a part of the virtual computer system 100 in Embodiment 1 is modified will be described.
[0203] The hardware configuration of the virtual computer system 1500 according to the second embodiment is partially modified from the virtual computer system 100 according to the first embodiment, and part of the executed software is partially modified from the virtual computer system 100 according to the first embodiment.
[0204] The virtual computer system 100 of the first embodiment is an example of a configuration including the memory protection unit 107 for controlling access to the storage area of the memory 102, but the second embodiment is an example of a case where the virtual computer system 1500 does not have a hardware The memory protection unit, a manager executed by the processor, has a function of controlling access to the sto...
Embodiment approach 3
[0222]
[0223] Hereinafter, as an embodiment of the virtual computer system of the present invention, a modified virtual computer system in which a part of the virtual computer system 100 in Embodiment 1 is modified will be described.
[0224] The hardware configuration of the modified virtual computer system according to the third embodiment is the same as that of the virtual computer system 100 according to the first embodiment, but part of the executed software is partially modified from the virtual computer system 100 according to the first embodiment.
[0225] This modified virtual computer system is an example of a virtual computer system configured such that even when a plurality of virtual computers are executed, only one virtual computer (here, the first virtual computer) among the executed virtual computers directly controls the display. , keyboard, and other devices, and other virtual computers indirectly control the devices by delegating control of the devices to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com