Secret document steganography and extraction method suitable for wireless communication environment
A technology for secret files and wireless communication, applied in wireless communication, electrical components, security devices, etc., can solve problems such as poor algorithm security, information security degradation, non-independent intellectual property leakage, and potential security risks, and achieve the effect of avoiding detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The specific implementation of the present invention will be further described below in conjunction with the accompanying drawings, but the implementation and protection scope of the present invention are not limited thereto.
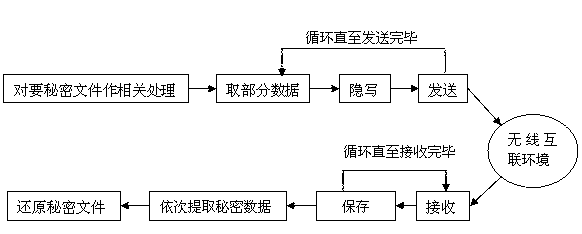
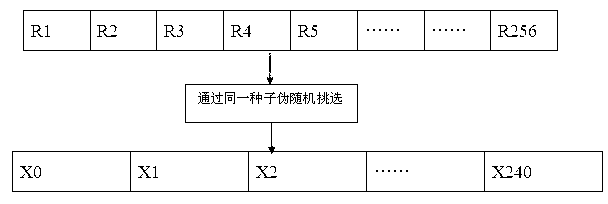
[0046] like figure 1It is the flow chart of steganography and extraction of secret files in the wireless communication environment of the embodiment. In this example, the byte size R of the voice data packet is set as 256, and the number of bytes S for steganography in each voice data packet is set as 240. . Since the improved LSB algorithm cannot directly steganographically secret files, before the sender and the receiver establish a voice call, the sender must first preprocess the secret files to be steganographically, and process the secret files into suitable ones for the improved LSB algorithm. secret data. The preprocessing steps are as follows:
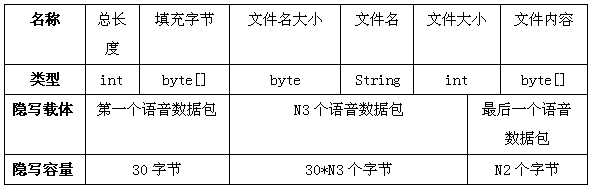
[0047] (1) Obtain relevant data from the secret file to be steganographic, including file n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com