Binary anti-counterfeit printing method based on transposition order-change
A technique of binary and binary information, applied to record carriers, instruments, electrical components, etc. used by machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
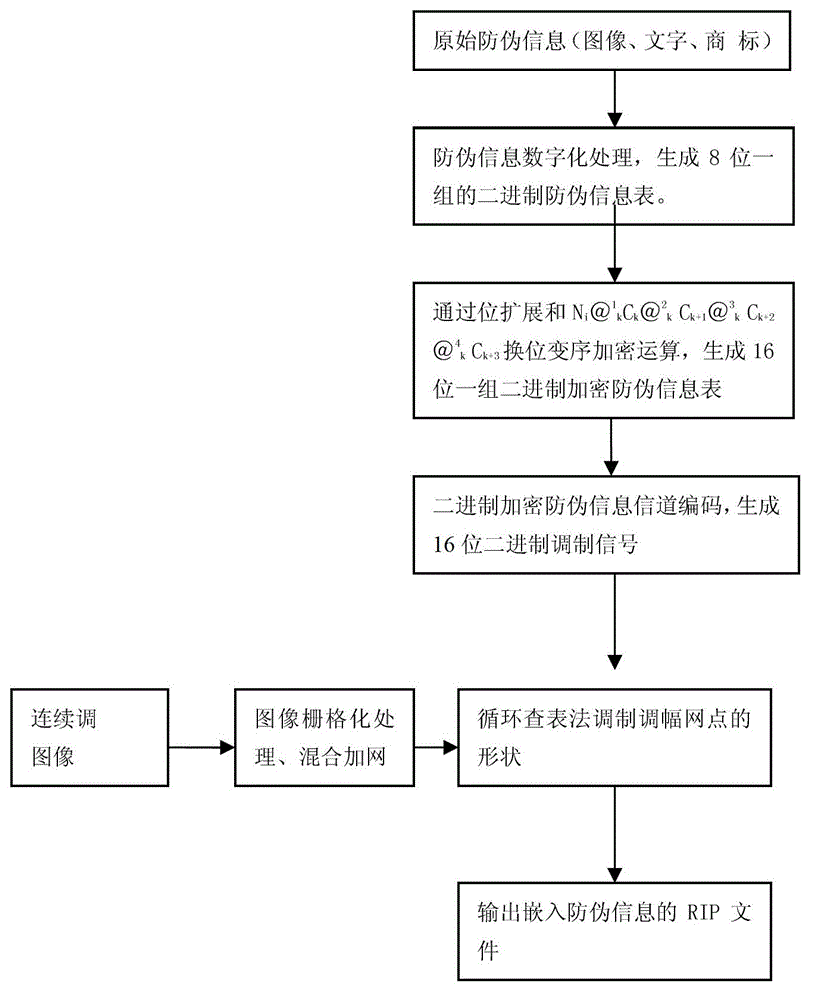
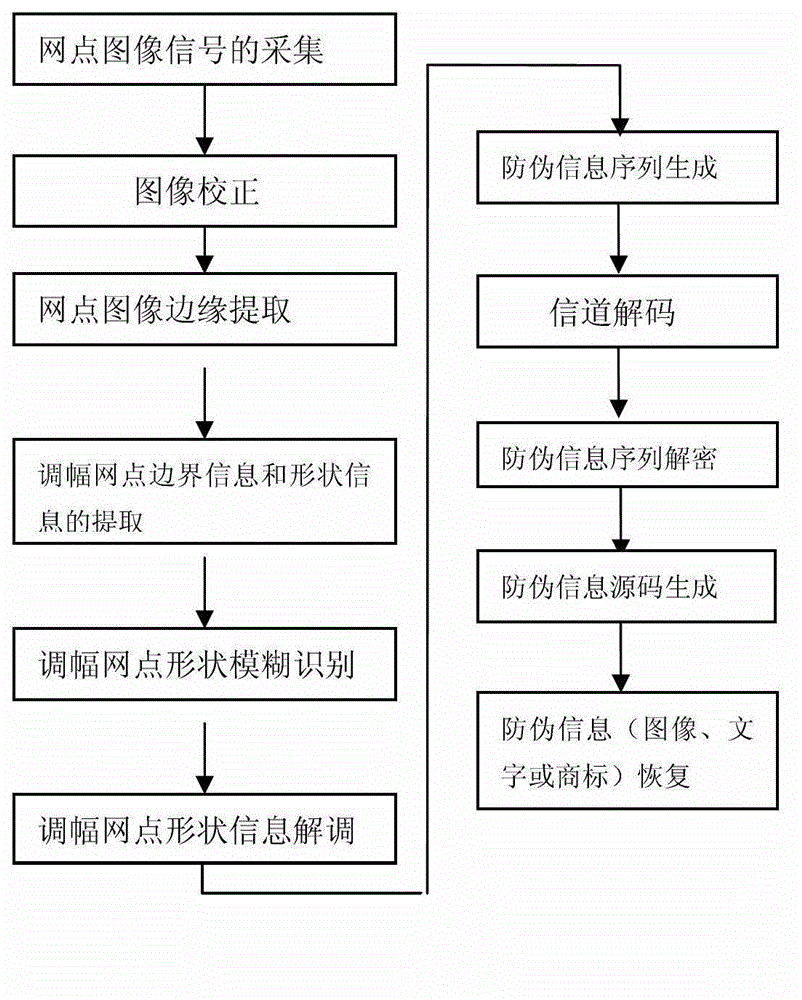
[0014] In the process of loading anti-counterfeiting information figure 1 Among them, the original anti-counterfeiting information (image, text, trademark) is digitized to generate an 8-bit binary anti-counterfeiting information table, and the 8-bit binary information in the binary anti-counterfeiting information table is expanded into a 16-bit binary information to generate A 16-bit binary anti-counterfeiting information table whose upper 8 bits are all 0, and the i-th group of 16-bit binary information in the 16-bit binary anti-counterfeiting information table is denoted as N i , i is a positive integer greater than 0, the binary control variable is denoted as k, the control variable k is a positive integer of 0≦k≦3, and the eight-digit binary encryption parameter is denoted as , the eight-bit binary encrypted parameter variable is denoted as , encryption parameter It is a positive integer from 0 to 256, the operator Four types of +, -, ×, ÷ are used, and when the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com