Method and device for controlling safety access to Java applications
A security access control, java application technology, applied in the field of communication, can solve the problems of technical implementation barriers, inflexibility, inflexible JAAS deployment, etc., to meet user access needs and improve flexibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
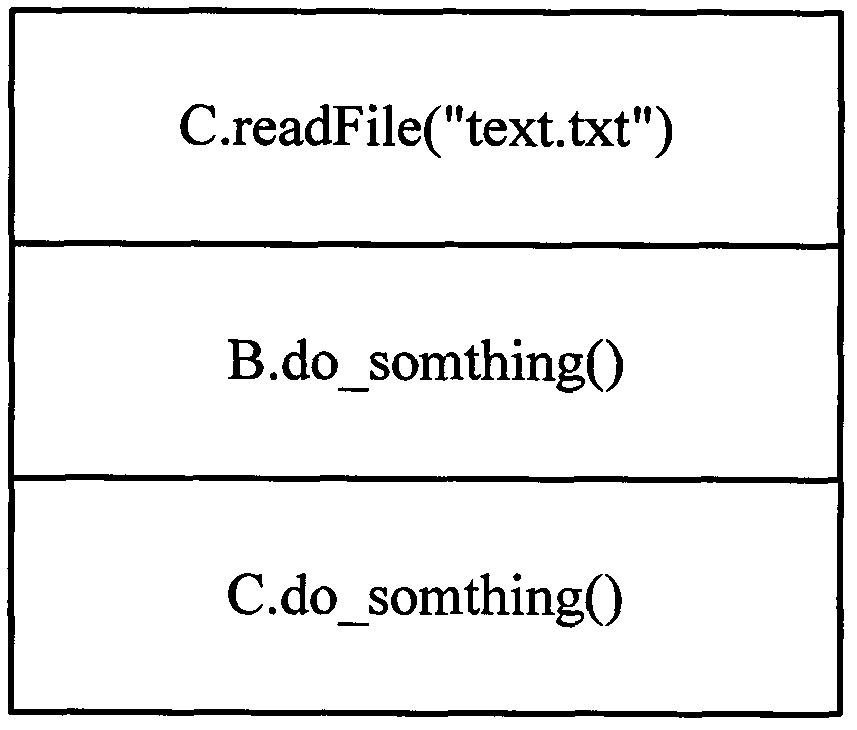
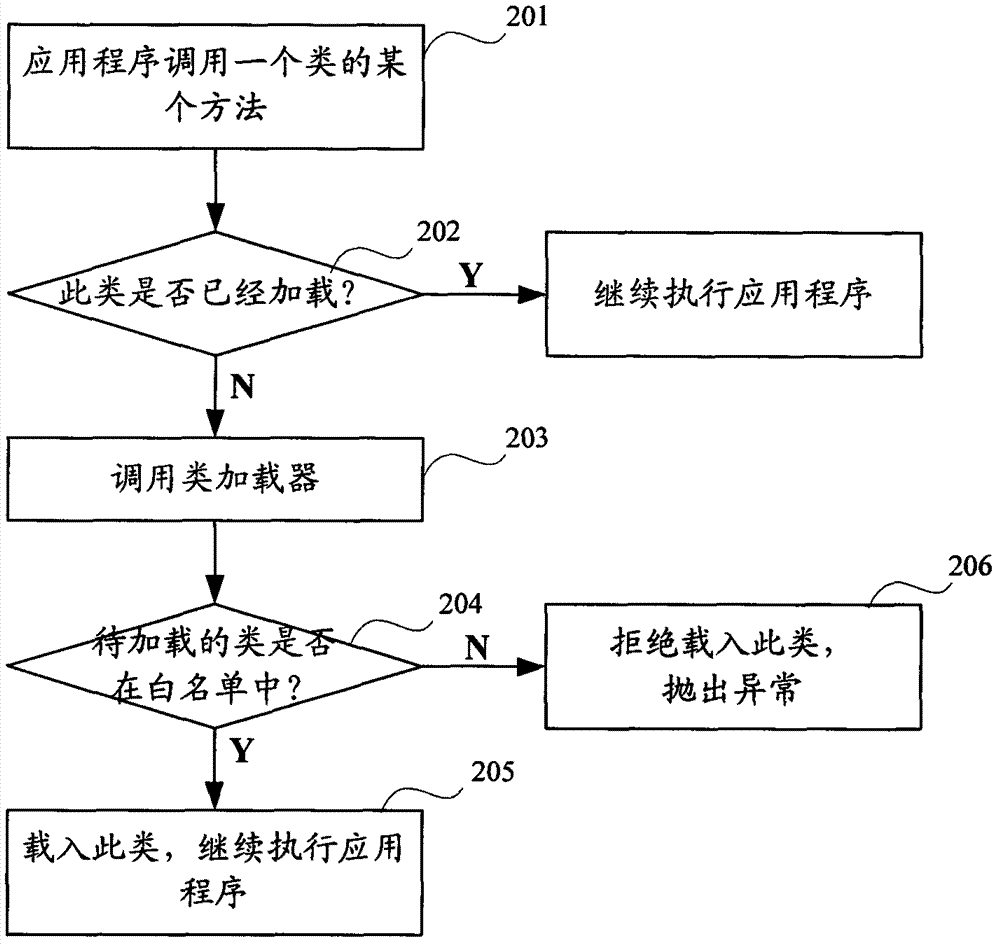
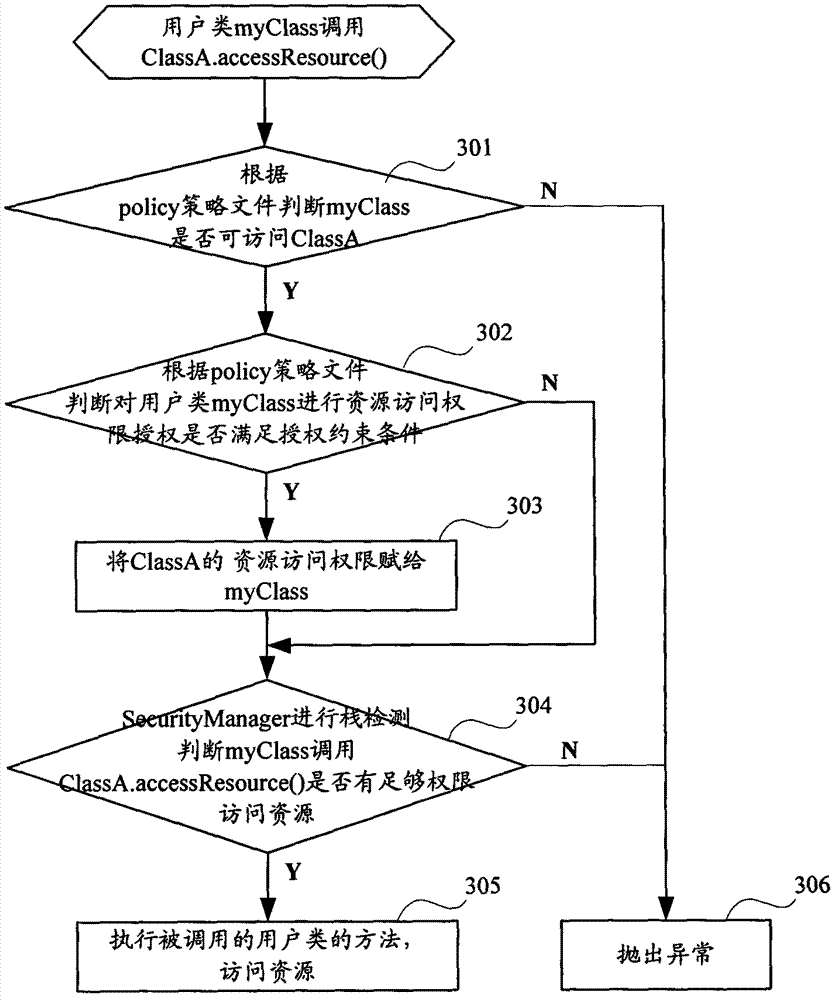
[0039] PaaS cloud platform refers to running multiple programs on a computer, and a mechanism is needed to ensure that user programs will not affect each other. The embodiment of the present invention proposes a security sandbox technology that prevents mutual influence between user programs. Within the limits of the security sandbox, users can perform any operations permitted by their permissions. When a user attempts to perform an operation outside the security sandbox restrictions, a security exception will be thrown.
[0040] Generally, the security sandbox mechanism includes many functions, such as restricting user programs to write to the file system, creating sockets, creating child processes or threads, executing some system calls, and so on.
[0041] The embodiment of the present invention implements a brand-new Java access control mechanism by extending the description capability of the traditional policy. The security sandbox technology provided by the embodiment of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com