Method for realizing information interaction as non-contact mode, correlation equipment and system
An information interaction and non-contact technology, applied in transmission systems, near-field transmission systems, electrical components, etc., can solve problems affecting the security of NFC mobile terminals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
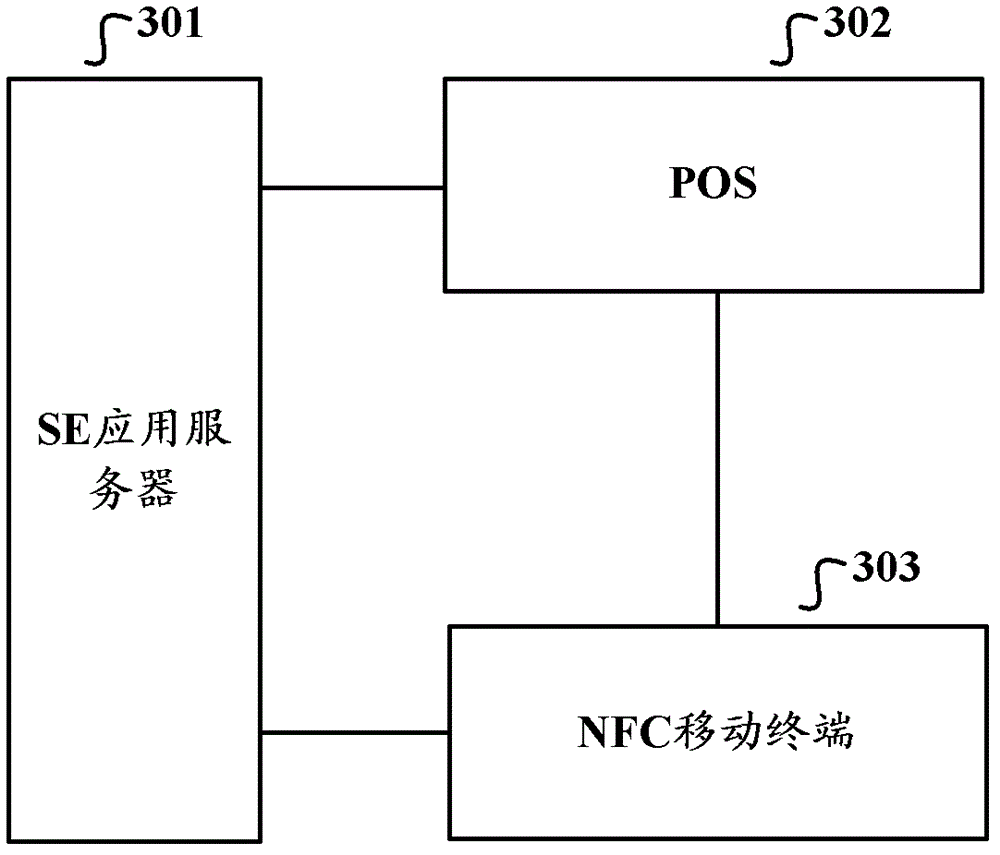
[0053] Such as Figure 4 As shown, it is a schematic diagram of the implementation flow of the method for implementing information interaction in a non-contact manner in the embodiment of the present invention, including the following steps:
[0054] S401. When using the SE application included in the SE built in the NFC mobile terminal, the NFC mobile terminal receives a confirmation request for using the SE application;
[0055] S402. The NFC mobile terminal instructs the NFC mobile terminal user to confirm according to the received confirmation request;
[0056] S403. After receiving the confirmation information returned by the NFC mobile terminal user, the NFC mobile terminal carries the confirmation information in the authentication request and sends it to the SE application server, requesting the SE application server to verify the confirmation information.
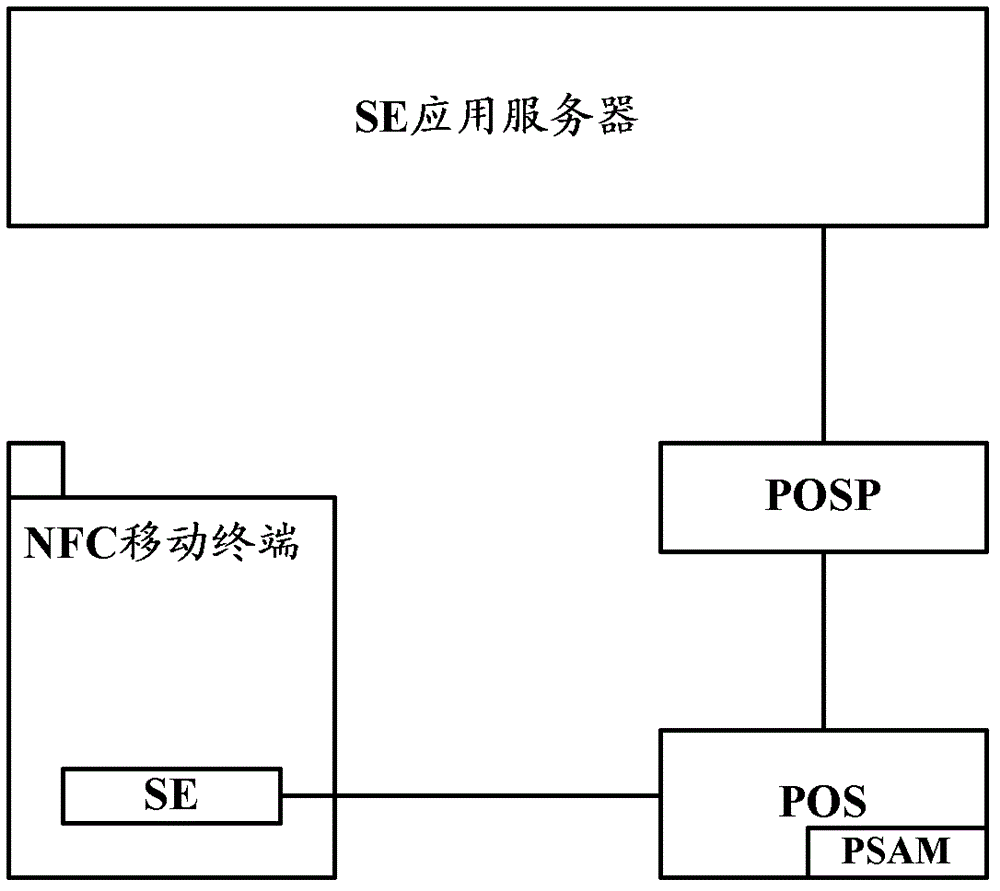
[0057] Such as Figure 5 As shown, in the embodiment of the present invention, when both POS and NFC mobile ter...
Embodiment 2
[0078] In order to understand the embodiment of the present invention, the SE application in the SE is used as an example below as an electronic wallet. Both POS and NFC mobile terminals can interact with SE application services in real time, and the electronic wallet included in the SE built in the NFC mobile terminal is used as an example to carry out illustrate.
[0079] Such as Figure 6 As shown, in the embodiment of the present invention, both POS and NFC mobile terminals are capable of implementing real-time interaction with SE application services, including the following steps:
[0080] S601. The POS receives the transaction information entered by the operator, and calculates the hash value of the transaction information;
[0081] Specifically, the transaction information may include: product details, for example, product price, product quantity, and product unit price.
[0082] S602. The user of the NFC mobile terminal swipes the NFC terminal on the POS, and the PO...
Embodiment 3
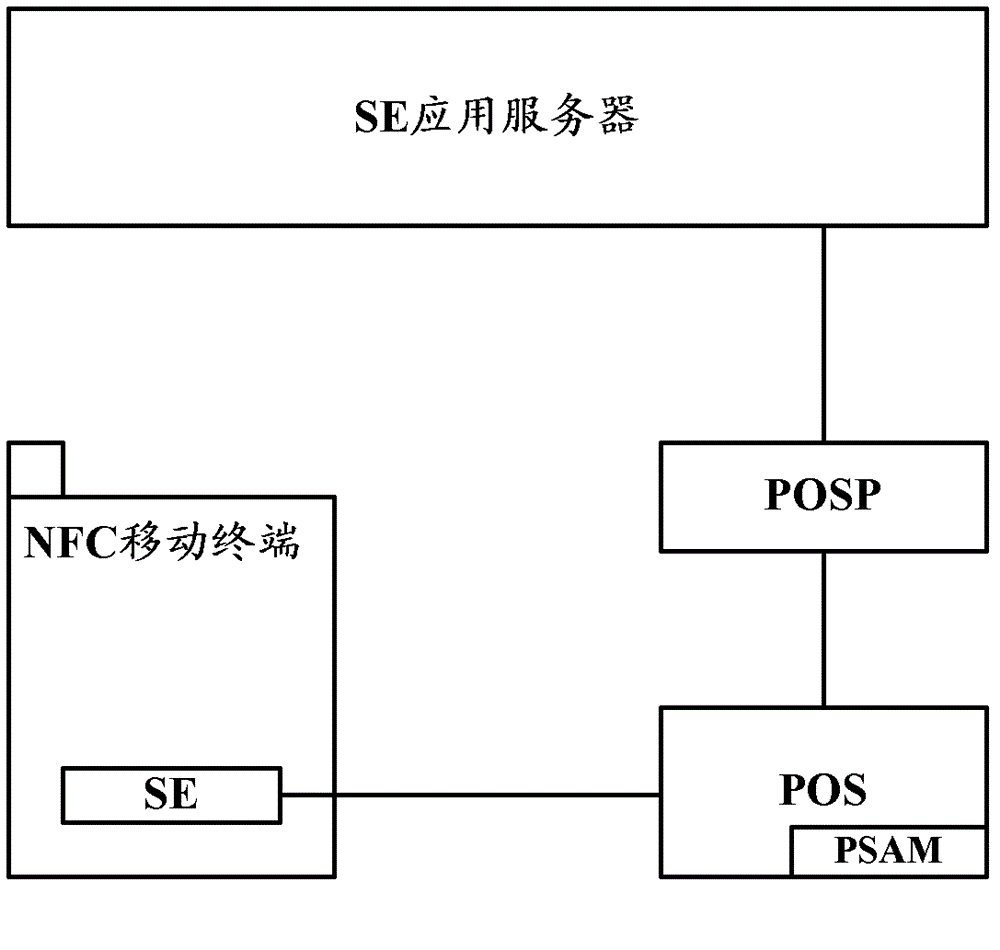
[0108] During specific implementation, the following application scenarios may also exist: the POS and the SE application server can interact in real time, and the NFC mobile terminal and the SE application server can interact in non-real time. In this case, take the SE application in SE as an electronic wallet as an example, such as Figure 7 As shown, the transaction flow diagram provided for the implementation of the present invention includes the following steps:
[0109] S701. The POS receives the transaction information entered by the operator, and calculates the hash value of the transaction information;
[0110] Specifically, the transaction information may include: product details, such as product price, product quantity, and product unit price.
[0111] S702. The NFC mobile terminal user swipes the NFC terminal on the POS, and the POS sends a confirmation request using the SE application to the NFC mobile terminal, requesting the mobile terminal user to confirm the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com