Structured query language (SQL) injection attacking protection method based on internal storage
A technology of injecting attacks and memory, applied in the field of network security, can solve problems such as firewalls not detecting SQL injection, client or server-side authentication is not strict, etc., to avoid SQL injection and improve operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] Below in conjunction with accompanying drawing and specific embodiment the present invention will be described in further detail
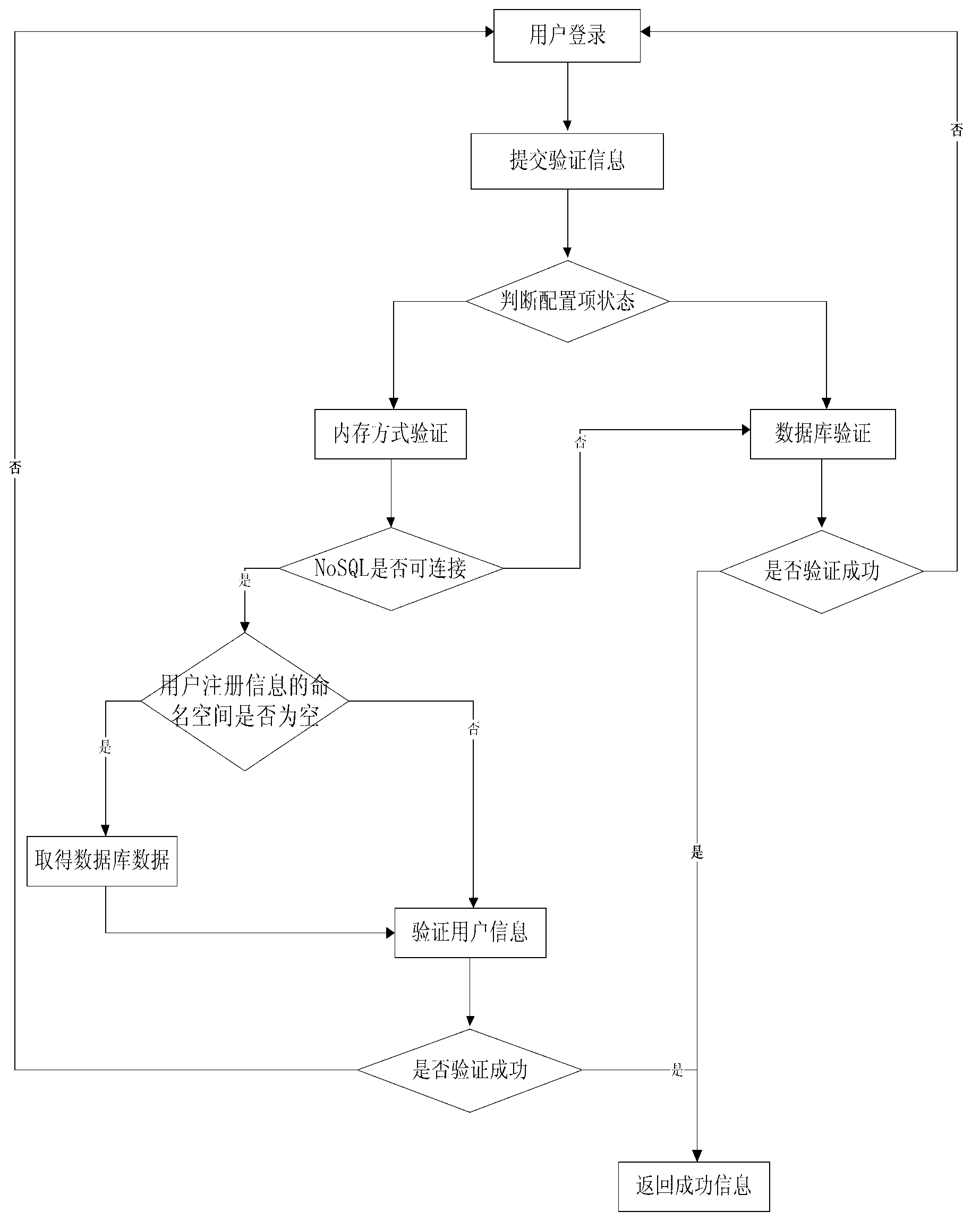
[0036] The invention provides a method for protecting against SQL injection attacks based on memory, comprising the following steps: user registration: put user information into a database, and put it into the memory database; user modification: modify the user information of the database, and synchronously modify the user of the memory database Information; User Verification: Select the memory database mode or database mode to verify user information according to the status of the configuration item. The following is a detailed description of the memory-based SQL injection attack protection method.
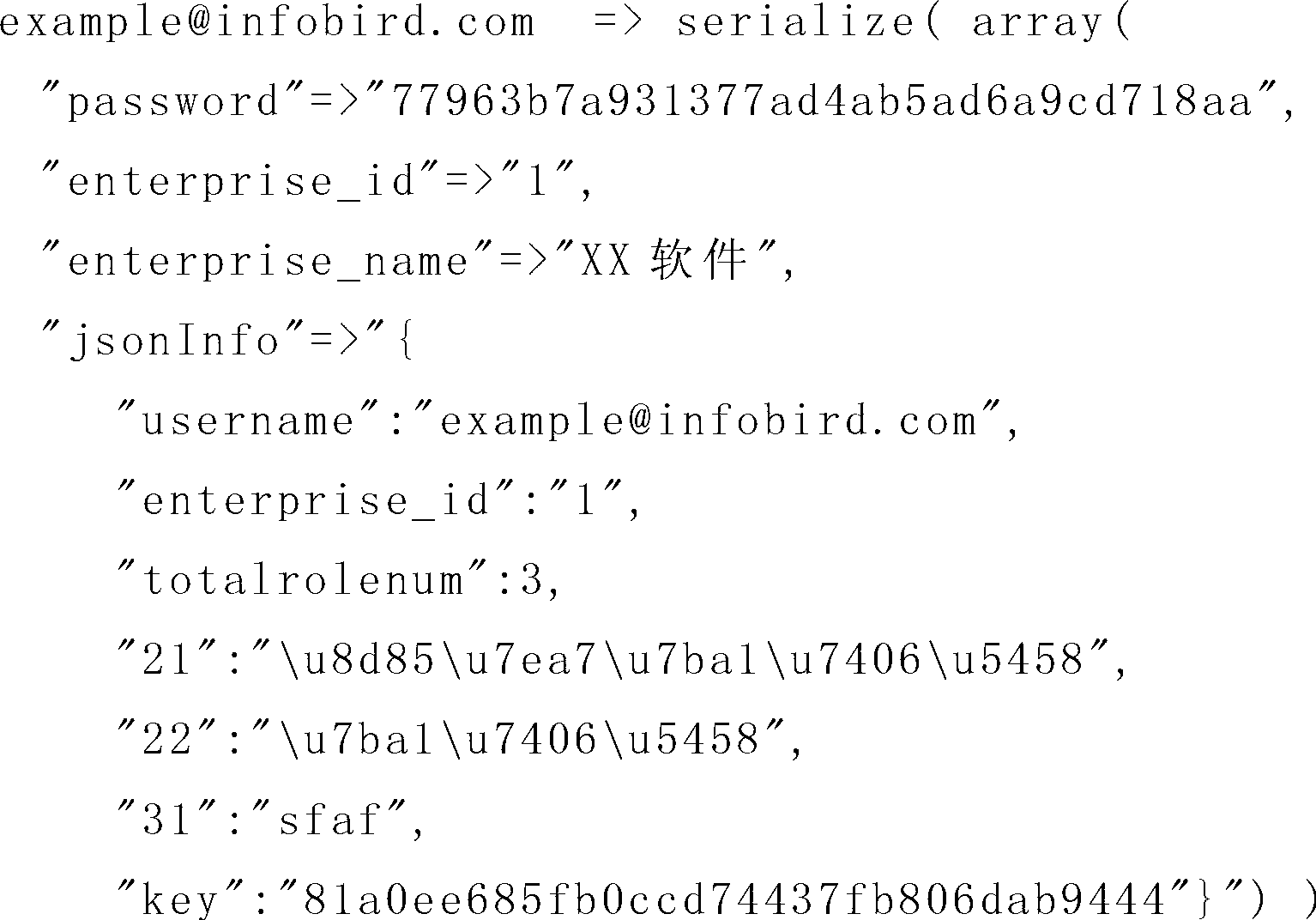
[0037] First, the user registration stage is introduced: when a user submits a registration application to the server, user information needs to be provided to the server. The user information includes registration information and necessary ver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com