Method and system for testing malicious Android application programs
An application detection and application technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of large manpower and material resources, unsuitable for large-scale and rapid security analysis, automatic analysis of false positives and high vulnerability rate, to ensure integrity, Effects of Simplifying Analysis Complexity, Improving Efficiency and Accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
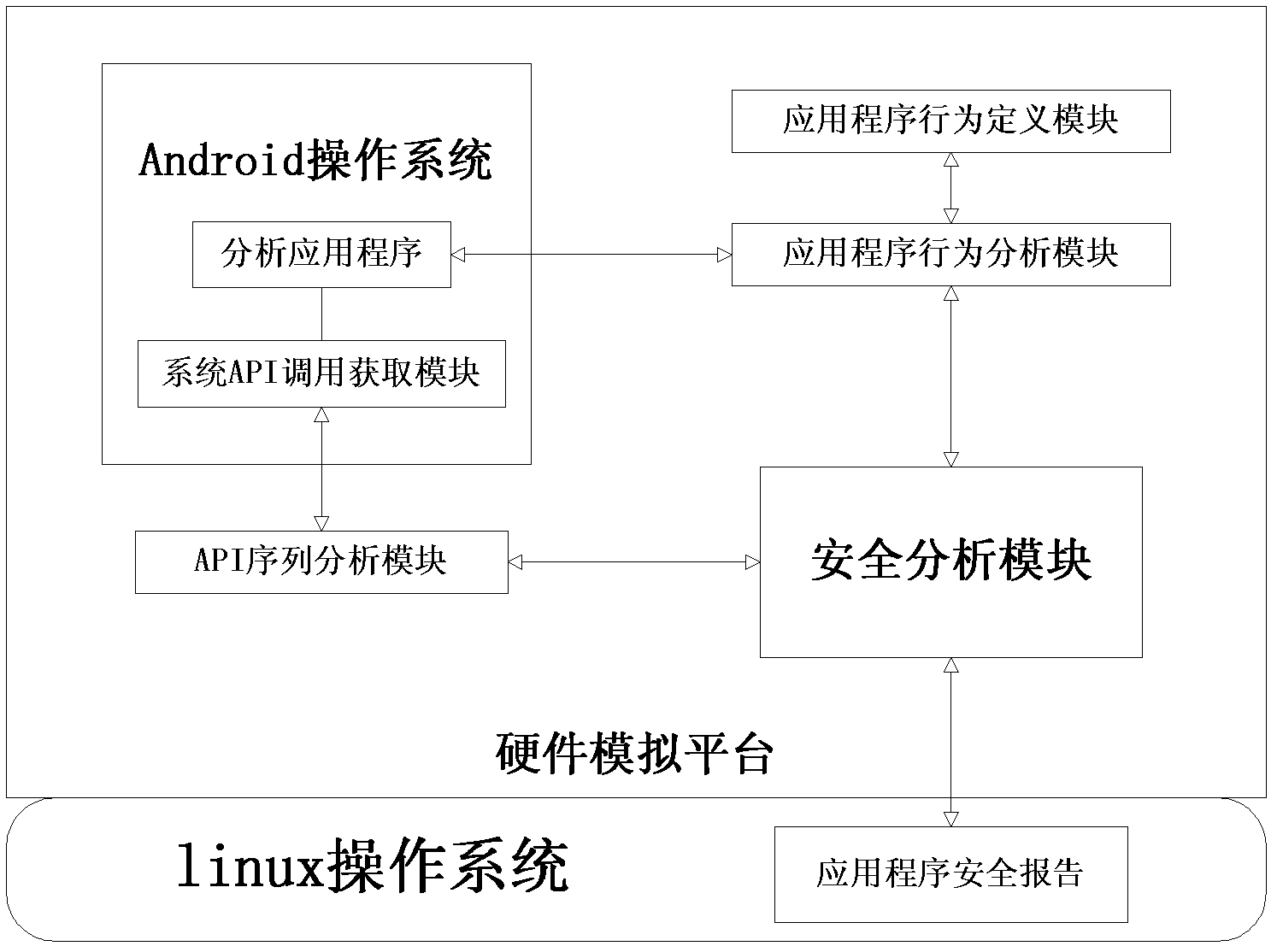
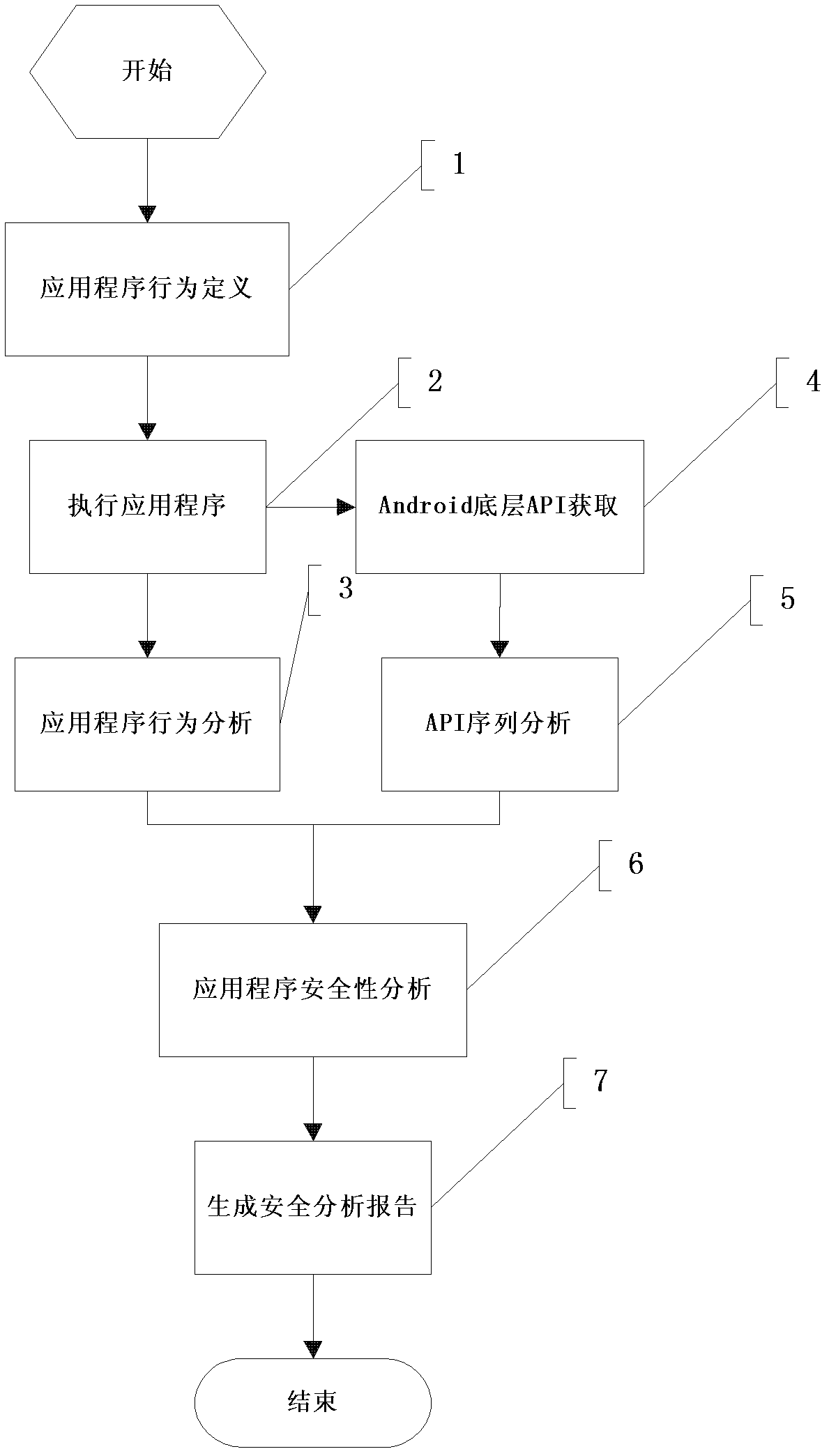
[0015] Such as figure 2 Shown is the implementation of the malicious Android application detection method in the most simplified mode. The specific implementation is as follows:
[0016] 1) Application behavior definition, the specific data uses the following format:
[0017]
[0018] Where page represents an operation interface of the application program, button represents a button on the operation interface, and function represents the function of the button on the operation interface. The specific functions are as follows:
[0019] #define 1 networking
[0020] #define 2 SMS
[0021] #define 3 access address book
[0022] #define 4 access sim card information
[0023] #define 5 access to multimedia data
[0024] #define 6 Executing the program
[0025] This part of the content is defined by the user assistance, that is, to define the functions of all buttons in an application.
[0026] 2) Execute the application.
[0027] In the controlled Android operating sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com