Method, device and system for identity verification in DLNA (digital living network alliance) network
An identity verification and network technology, applied in the field of home network, can solve the problems of unsolved identity verification, endangering multimedia data security and user privacy security, etc., and achieve the effect of ensuring security and privacy security and avoiding transmission.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
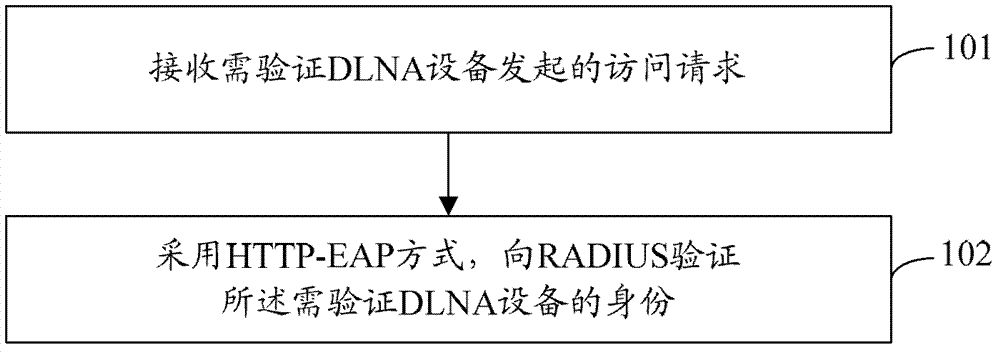
Method used
Image
Examples
Embodiment 1
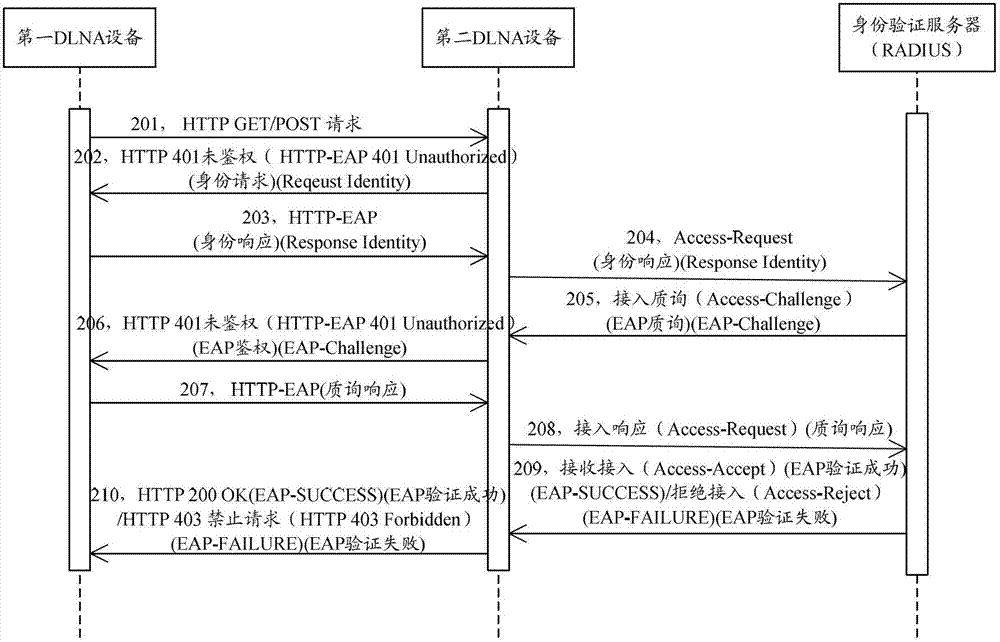
[0065] Such as figure 2 As shown, the specific implementation process of identity verification in the DLNA network of this embodiment may include the following steps:
[0066] Step 201: When the first DLNA device (eg, DLMA device with DMC / DMR) in the DLNA network needs to access certain resources on the second DLNA device (eg, DLMA device with DMR / DMS) or requests certain services , the first DLNA device initiates an HTTP GET / POST request to the second DLNA device;
[0067] Step 202: The second DLNA device receives the HTTP GET / POST request, enables the identity verification function, encodes the EAP identity request (Request Identity) message with BASE64, and encapsulates it into the WWW of the HTTP 401 Unauthenticated (HTTP 401 Unauthorized) message - in the Authenticate header field (a standard message header defined by HTTP (RFC2613), and sending the HTTP401 Unauthorized message to the first DLNA device, requesting to obtain the identity information of the first DLNA dev...
Embodiment 2
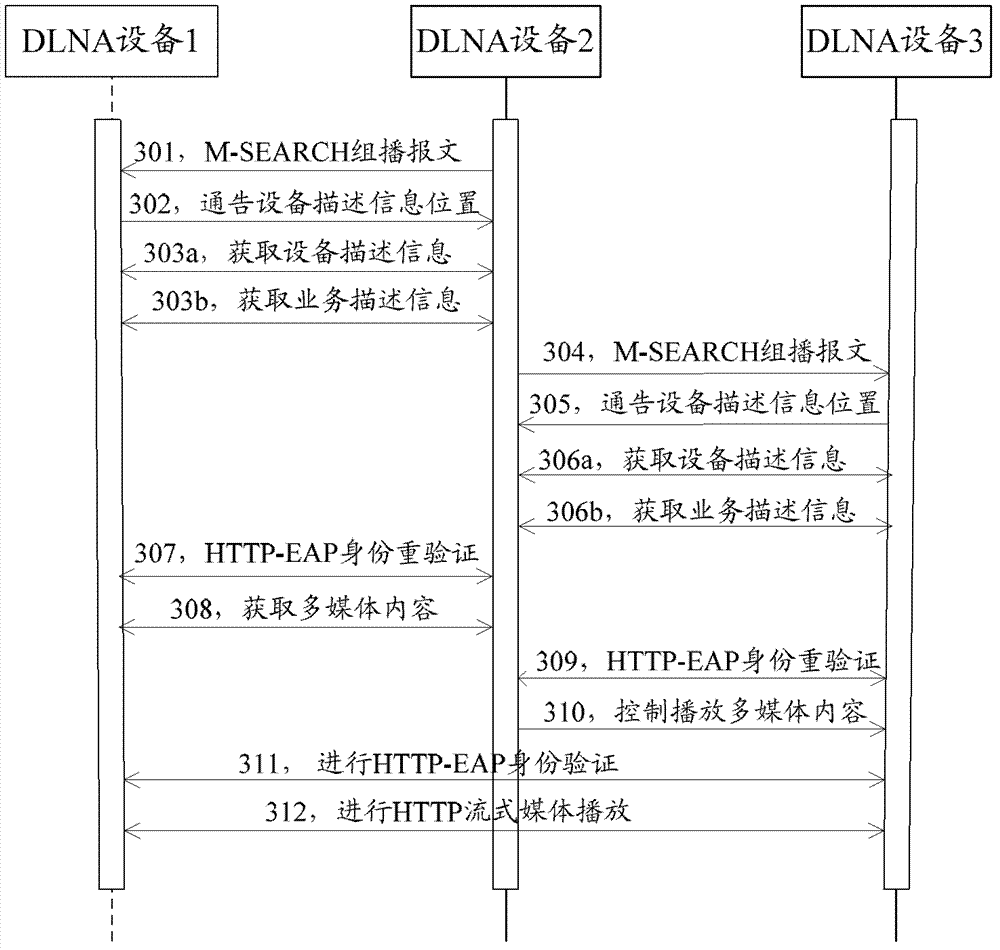
[0082] Taking the process of the DMC browsing the media content of the DMS and playing the media content on the DMR as an example, the application of the identity verification method in the DLNA network of the present invention will be described in detail below. In this embodiment, regardless of the aggregation of DLNA devices, DLNA includes DLNA device 1 with DMC, DLNA device 2 with DMS, and DLNA device 3 with DMR. DMP is used as a special DMC, that is, MSCP. Therefore, DLNA device 1 Also has DMP.
[0083] Such as image 3 As shown, the DMC browses the media content of the DMS and plays the process of the media content on the DMR, which may specifically include:
[0084] Step 301: In the device discovery phase, DLNA device 1 with DMS and DLNA device 3 with DMR in the DLNA network communicate through SSDP protocol, using IP multicast and broadcast mechanism, and DLNA device 1 sends M-SEARCH of SSDP protocol in DLNA Multicast message, actively search for DLNA devices with DMS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com