Method for building desktop cloud virtual trust safety wall
A security wall and desktop cloud technology, applied in the field of building a desktop cloud virtual trusted security wall, can solve the problems of low degree of automation, extensive security granularity of user desktops, and difficulty in following up with different organizations, and achieve the effect of enhancing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
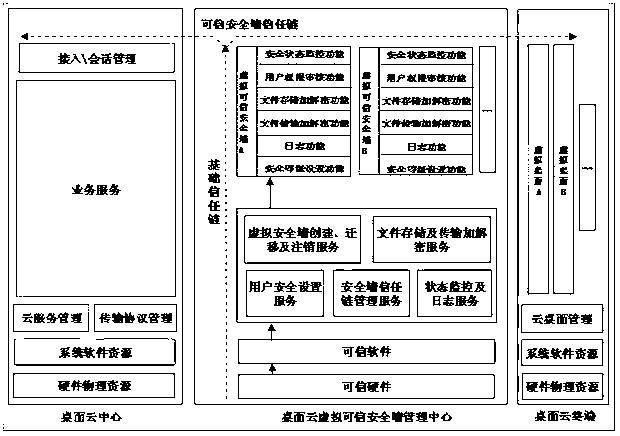
[0022] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
[0023] A method for constructing a desktop cloud virtual trusted security wall. In the present invention, TCM is used as the root of trust, and the security wall trust chain and the basic trust chain are formed together to form a two-dimensional trust chain, and the virtual trusted security wall is implemented along with the virtual desktop. Simultaneously migrate, build a two-dimensional trust chain, and extend the trust relationship from the trust root to the entire desktop cloud system through the two-dimensional trust chain.
[0024] In the present invention, the basic trust chain includes: TCM root of trust, BIOS, MBR, OS Loader, OS Kernel, Service / Application, virtual security wall management center.
[0025] In the present invention, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com