Method of generating bill for protecting user access privacy in network service
A technology for network services and users, which is applied in user identity/authority verification and key distribution, and can solve problems such as high communication costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
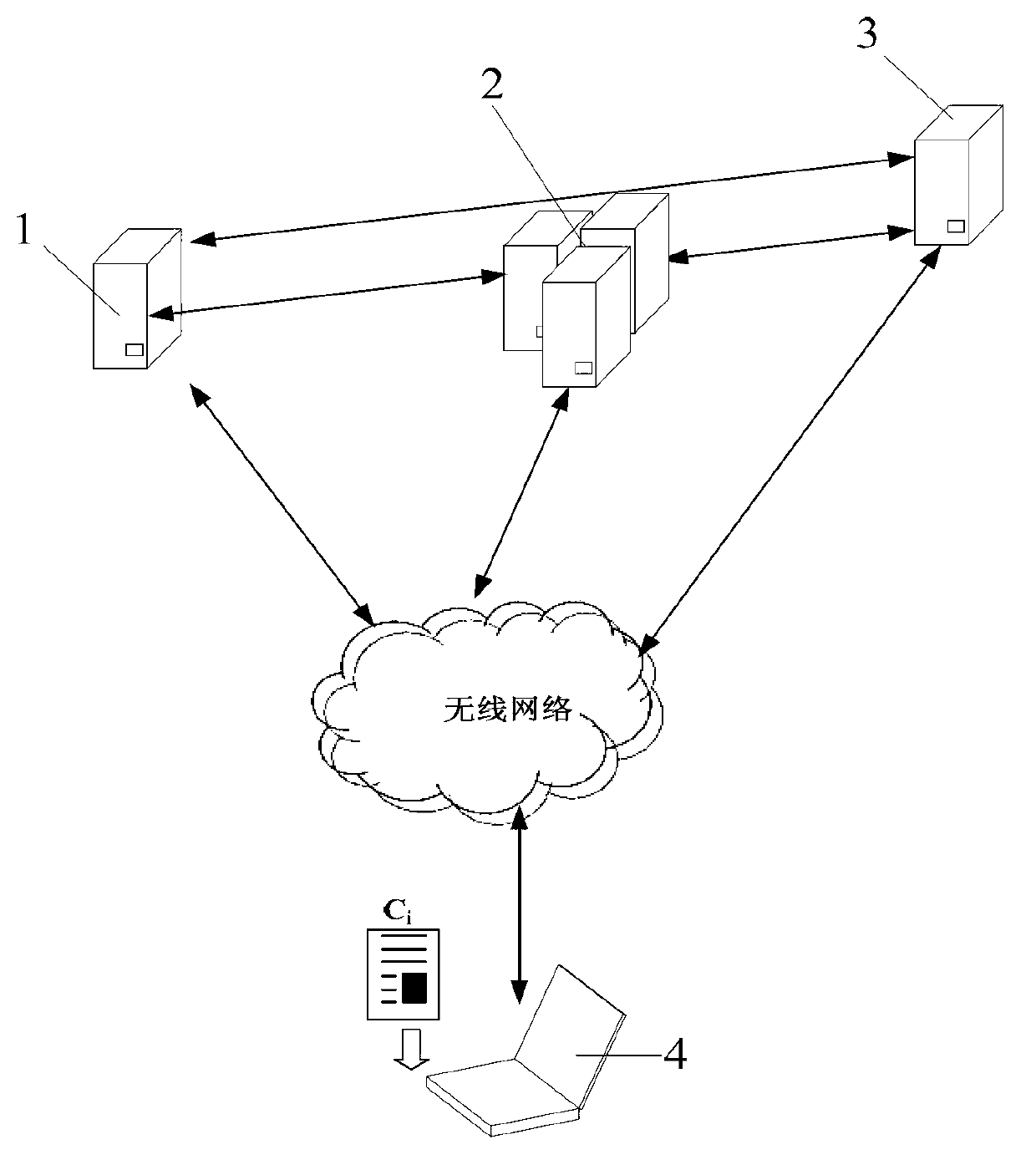
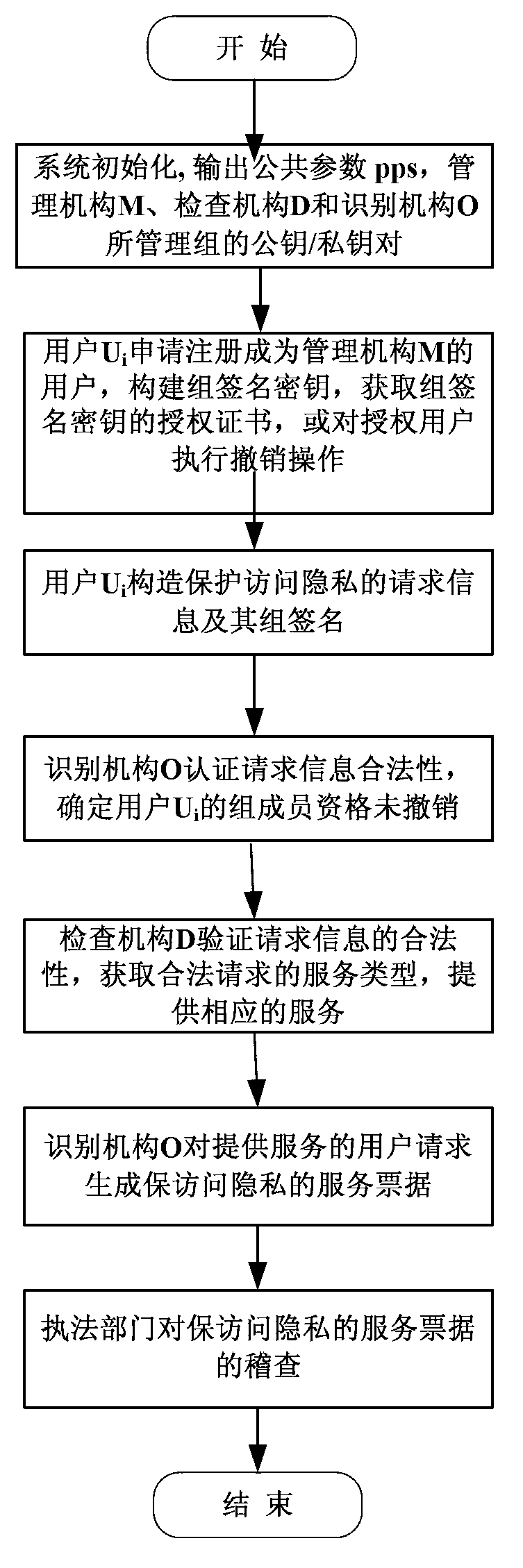
[0116] In this embodiment, a bill generation method for protecting user access privacy in network services, such as figure 1 As shown, the ticket generation system used to implement the ticket generation method of this embodiment includes a management agency M1, an inspection agency D2, an identification agency O3, and a user device 4; the management agency M, the inspection agency D, and the identification agency O pass data transmission The bus is connected to each other, the user equipment is connected to each other through data lines or the network, and the management organization M, the inspection organization D and the identification organization O are respectively connected to the user equipment through the network.
[0117] Management agency M: used to distribute public key / private key pairs of inspection agencies, identification agencies, and public keys for generating groups, and generate user U i Authorization certificate on group signing key.
[0118] Inspection a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com