A user authentication and key agreement system and method for the internet of things
A technology of key agreement and user authentication, which is applied in the field of security authentication for communication between users and sensor nodes, can solve problems such as heavy calculation consumption, and achieve the effect of ensuring forward secrecy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
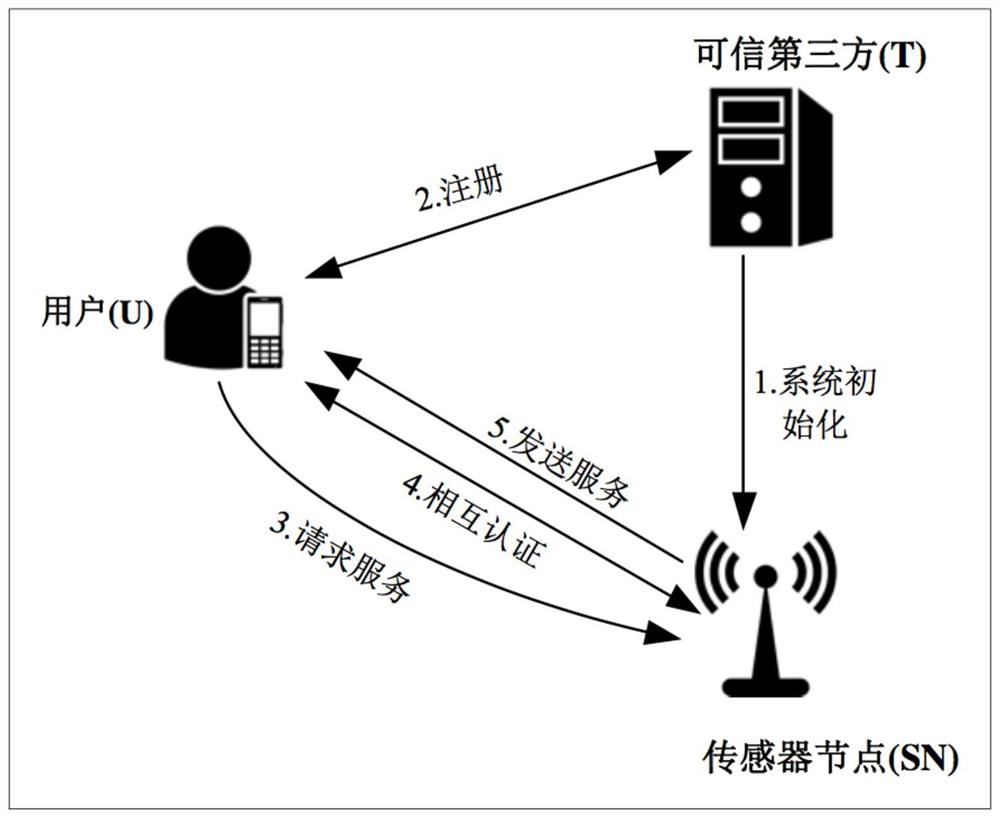
[0043] refer to Figure 1-Figure 3 , the specific embodiments of the present invention are as follows:
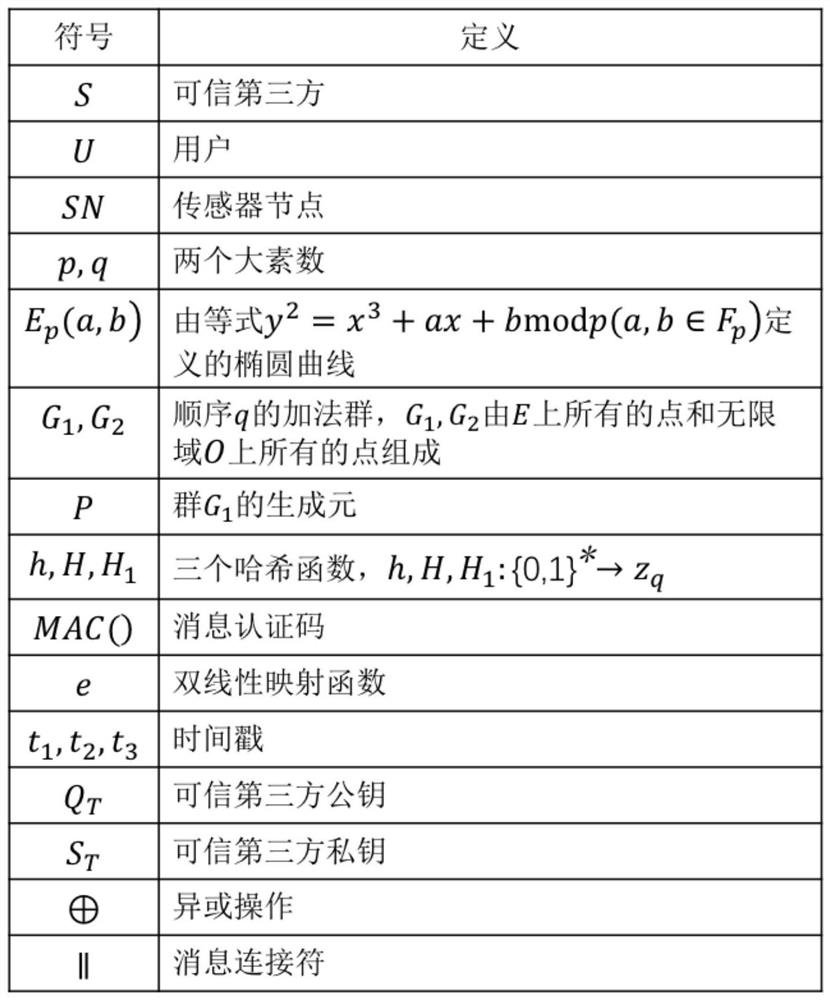
[0044] 1. In the most initial situation, each element under the IoT system is initialized. First, generate basic system parameters through a trusted third-party T gateway node, including selecting the group E on the elliptic curve p (a, b), (a, b represent two random numbers on the finite field, p, q are two large prime numbers on the elliptic curve), select three hash functions h, H, H 1 :h,H,H 1 →{0,1} * , choose the message authentication code MAC function and choose the bilinear pair e; choose the random number As the master key of the trusted third party, Represents a set of positive integers, and calculates the system public key Q T =s T P (P is the generator of the group); subsequently, the trusted third party T announces the public parameter set:
[0045] parameters={a,b,p,q,P,Q T ,h,H,H 1 ,MAC,e};
[0046] In addition, the sensor node SN chooses a rand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com