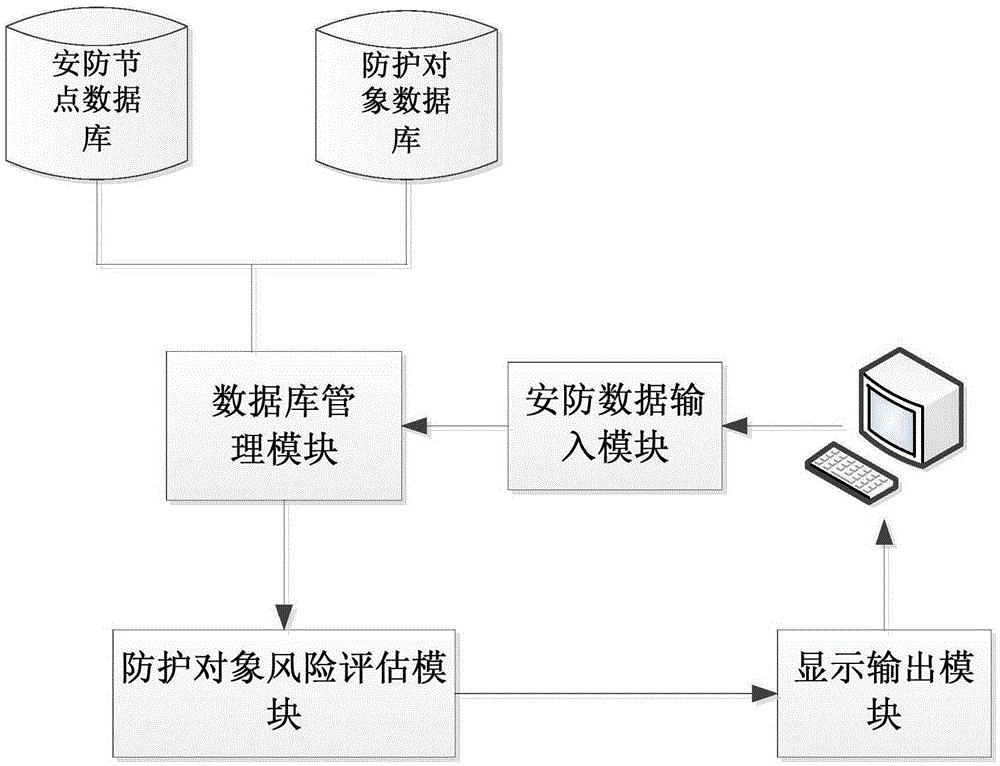
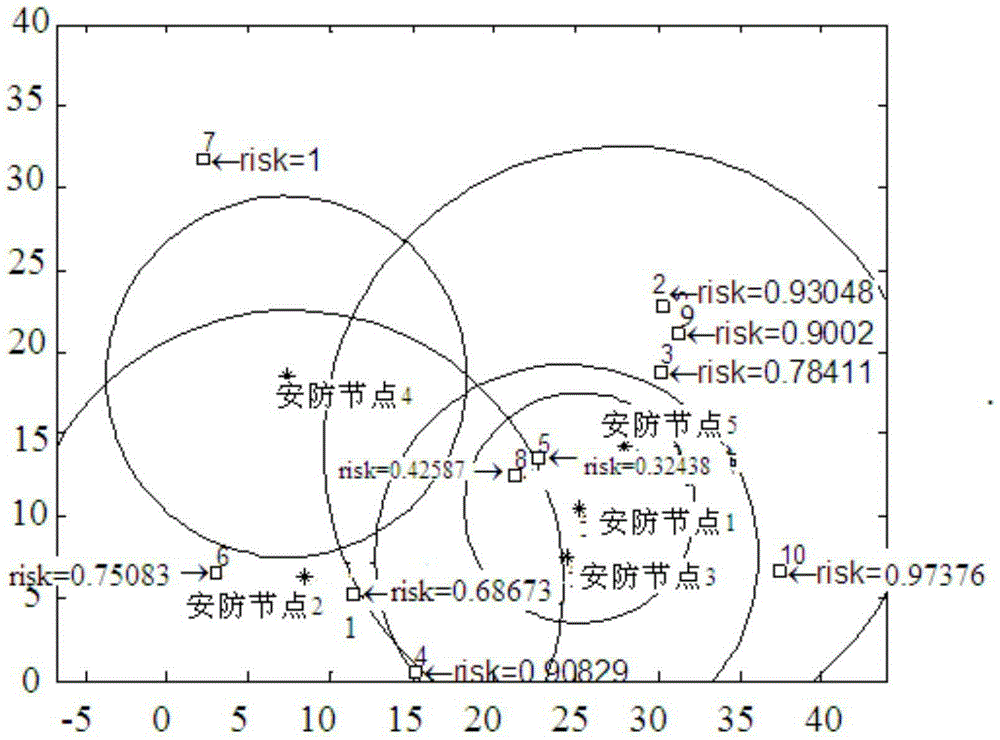
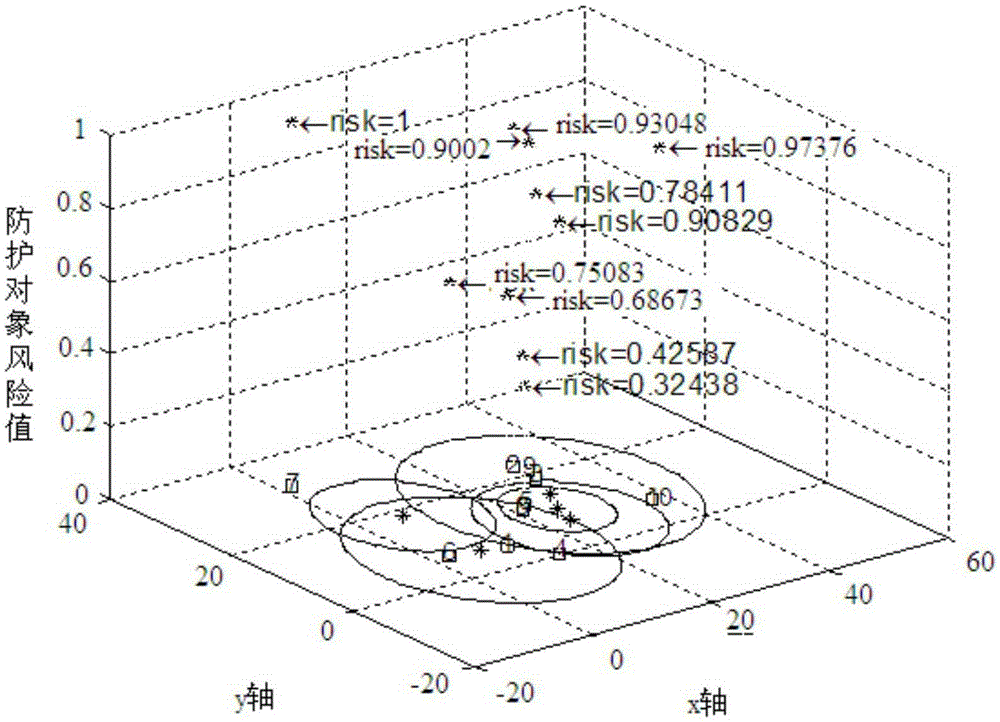
Risk assessment method and system for fixed protected objects in security protection network
A technology for security prevention and object protection, which is applied in the fields of instruments, computing, and electrical and digital data processing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The traditional methods for qualitative risk assessment of protected objects using management science methods are as follows:
[0034] For the security node s, its key protection performance index is A 1 ,A 2 ,A 3 ,...,A n , The index weight corresponding to the protection performance index is w 1 , w 2 , w 3 , · · · , w n ( ∀ w i A [ 0,1 ] i = 1,2 , · · · , n ) , And X i = 1 n w 1 = 1 , And establish a measurement interval representing the level of protection performance. Suppose the field experts score the various protection performance indicators as a 1 , a 2 , a 3 , · · · , a n ( ∀ a i A [ 0,1 ] i = 1,2 , · · · , n ) , Then build the following protection performance evaluation model:
[0035] P(s)=[w 1 ,w 2 ,w 3 ,...,W n ]×[a 1 ,a 2 ,a 3 ,...,A n ] T
[0036] According to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com