A Location and Path Concealment Protection Method Based on IPv6 Technology
A path information and destination technology, applied in the field of location and path concealment protection based on IPv6 technology, can solve the problems of increased computational complexity, difficulty in application, large storage space, etc., and achieve the effect of reducing time complexity and space complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
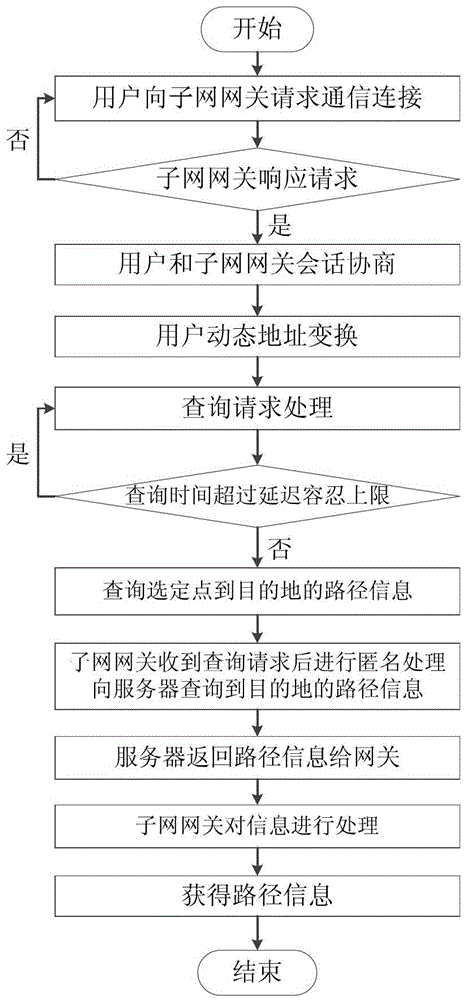
[0027] Below in conjunction with accompanying drawing, a kind of location based on IPv6 technology proposed by the present invention and path concealment protection method are described in detail:
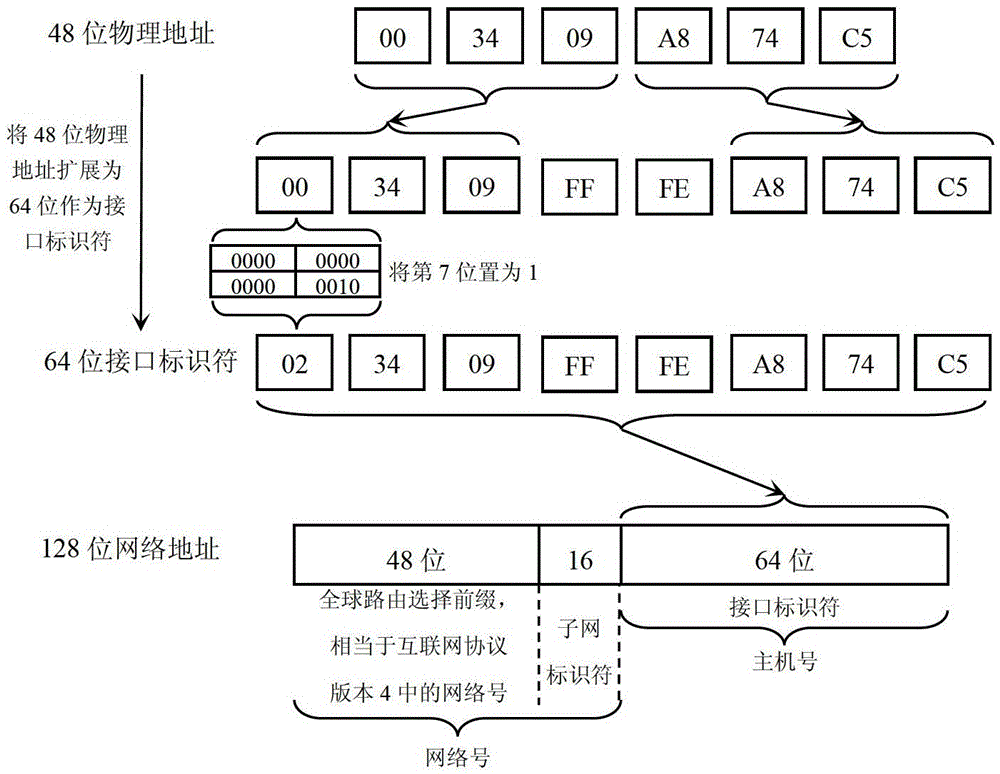
[0028] First, if figure 2 As shown, all sensor nodes in the present invention adopt IPv6 addressing, and the IPv6 address of equipment adopts EUI-64 format addressing. As shown in the figure, extend the MAC address of the node, add FFFE in the middle for a total of 16 bits, then set the seventh bit to 1, and convert it into a new 64-bit address as the interface identifier of the IPv6 address, that is, the host number , and then connect the host ID with the subnet address to obtain a 128-bit IPv6 address.
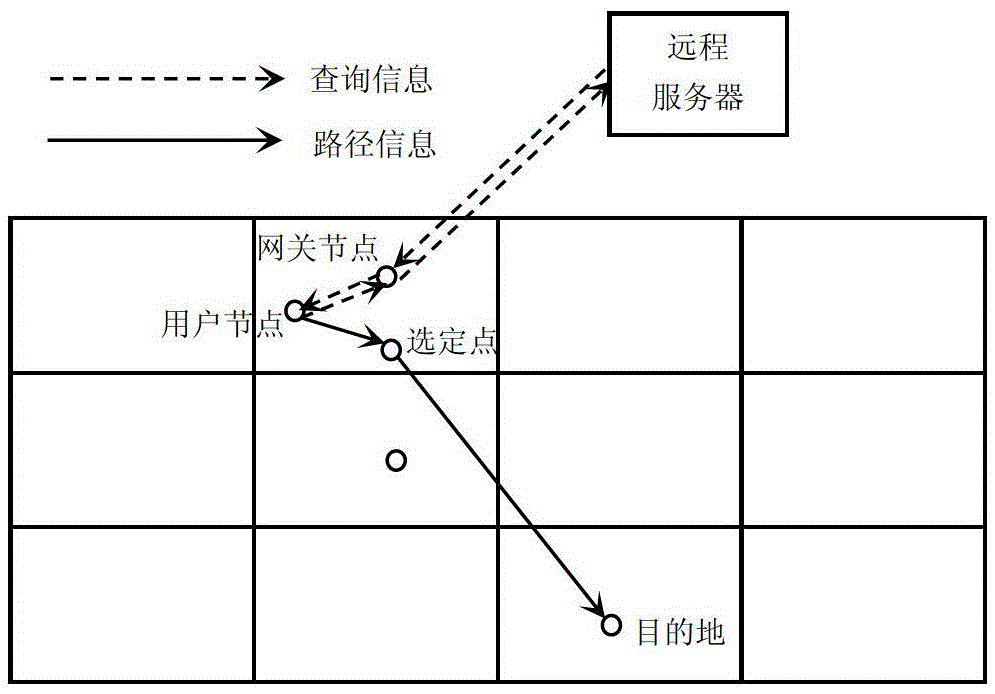
[0029] The problem solved by the invention is the privacy protection problem based on the location service, that is, the user queries the server for service information, and hopes that the server returns a path that meets the query requirement without disclosing the user's own ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com