Novel secret key separated signing method and system
A key and signer technology, applied in the field of information security, can solve problems such as difficult to guarantee system security, lack of key isolation, and insecure key isolation system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
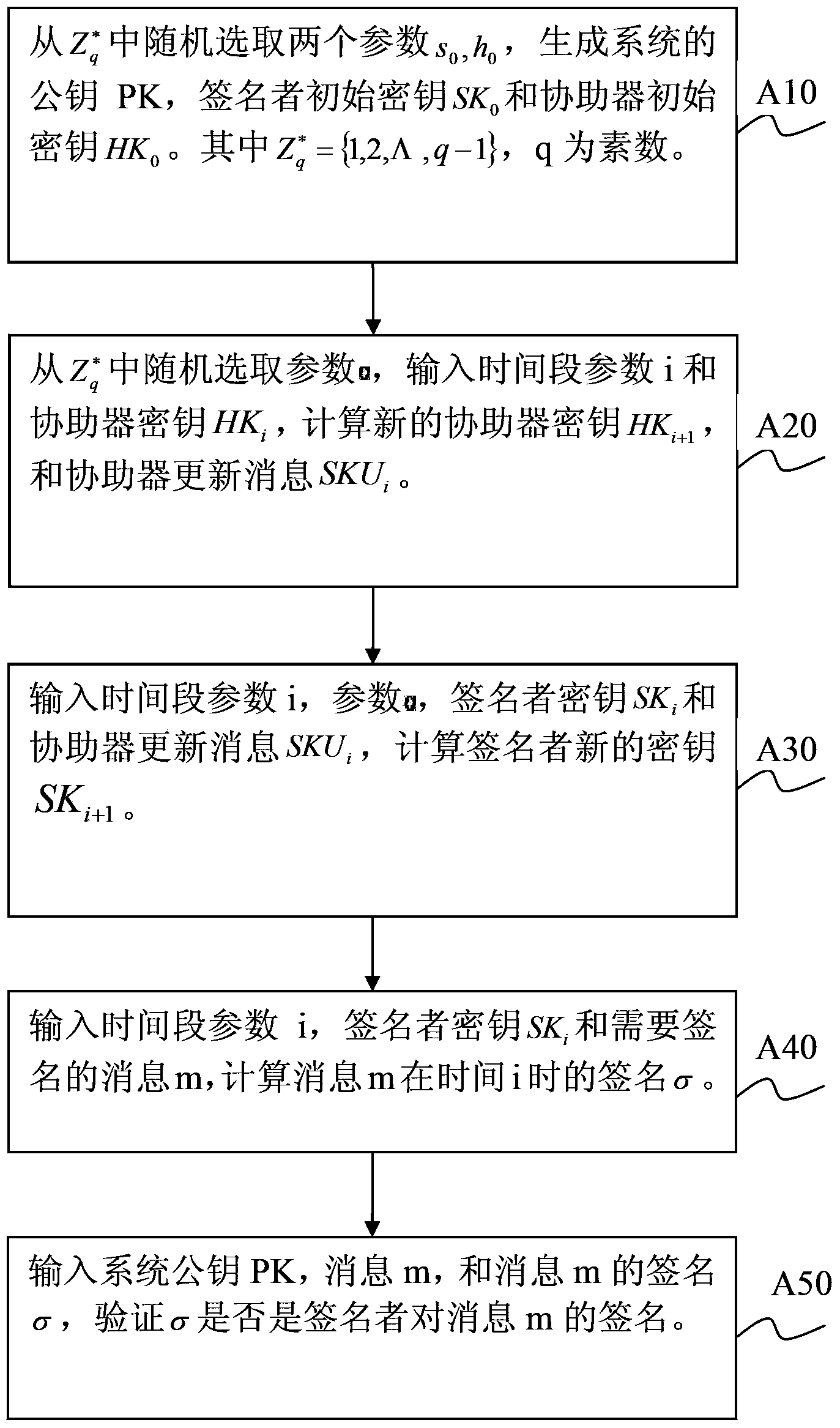
[0071] The key isolation signature method and system with assistant key self-renewal capability provided by the present invention are based on the following mathematical theory:
[0072] 1. Bilinear pairing
[0073] Let G 1 is a multiplicative group of order q, G 2 is another multiplicative group of order q, if the mapping satisfy the following properties:
[0074] 1) Bilinear: For ∀ P , Q ∈ G 1 , Satisfy e ^ ( P a , Q b ) = e ^ ( P , Q ) ab .
[0075] 2) Non-degenerate: there exists P,Q∈G such that
[0076] 3) Computability: Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com