XEN cloud platform-based virtual machine block device isolation method
A virtual machine and cloud platform technology, applied in the field of information security, can solve problems such as user information leakage and serious cloud information security problems, and achieve the effect of improving security and realizing isolation protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
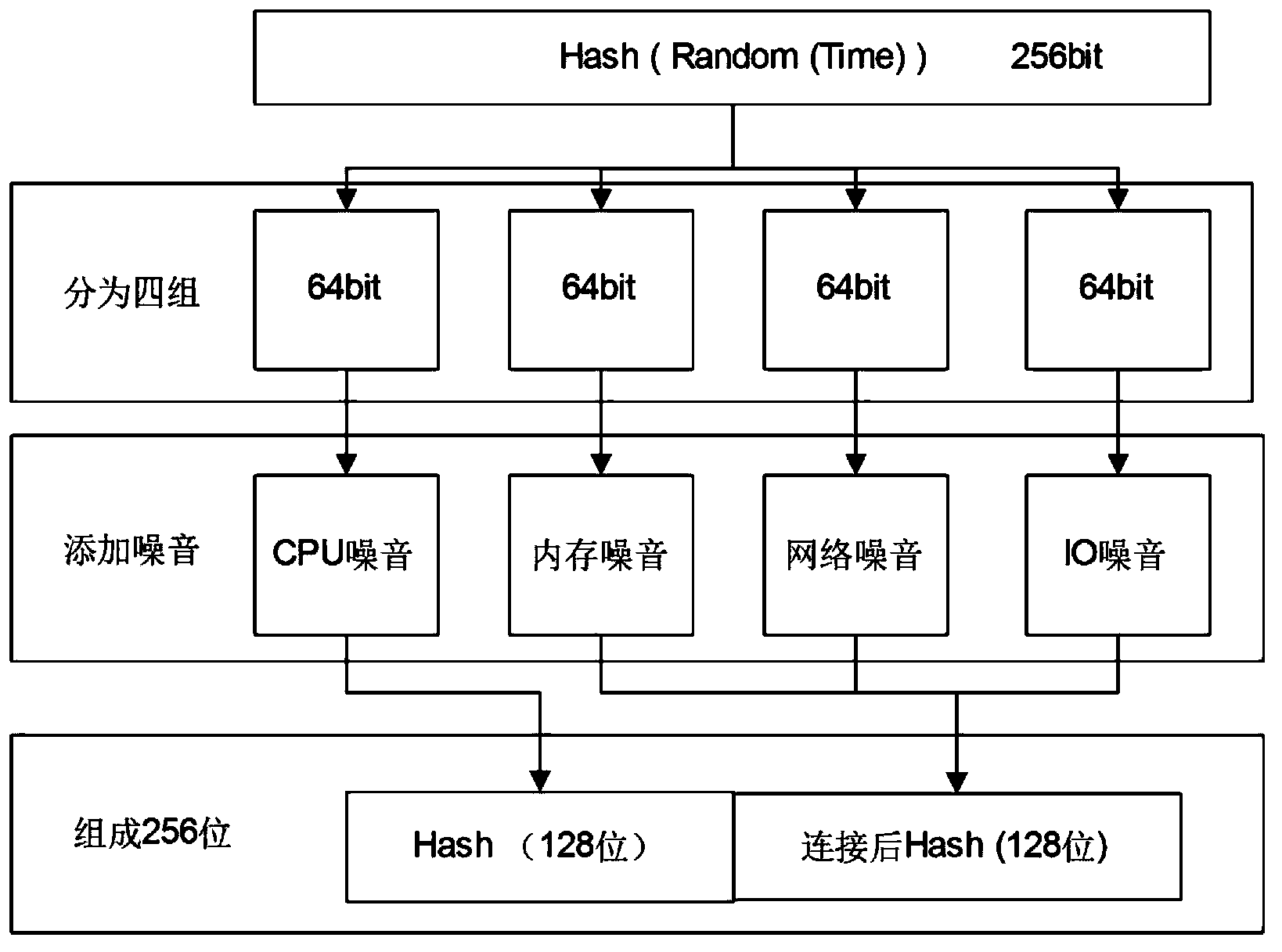
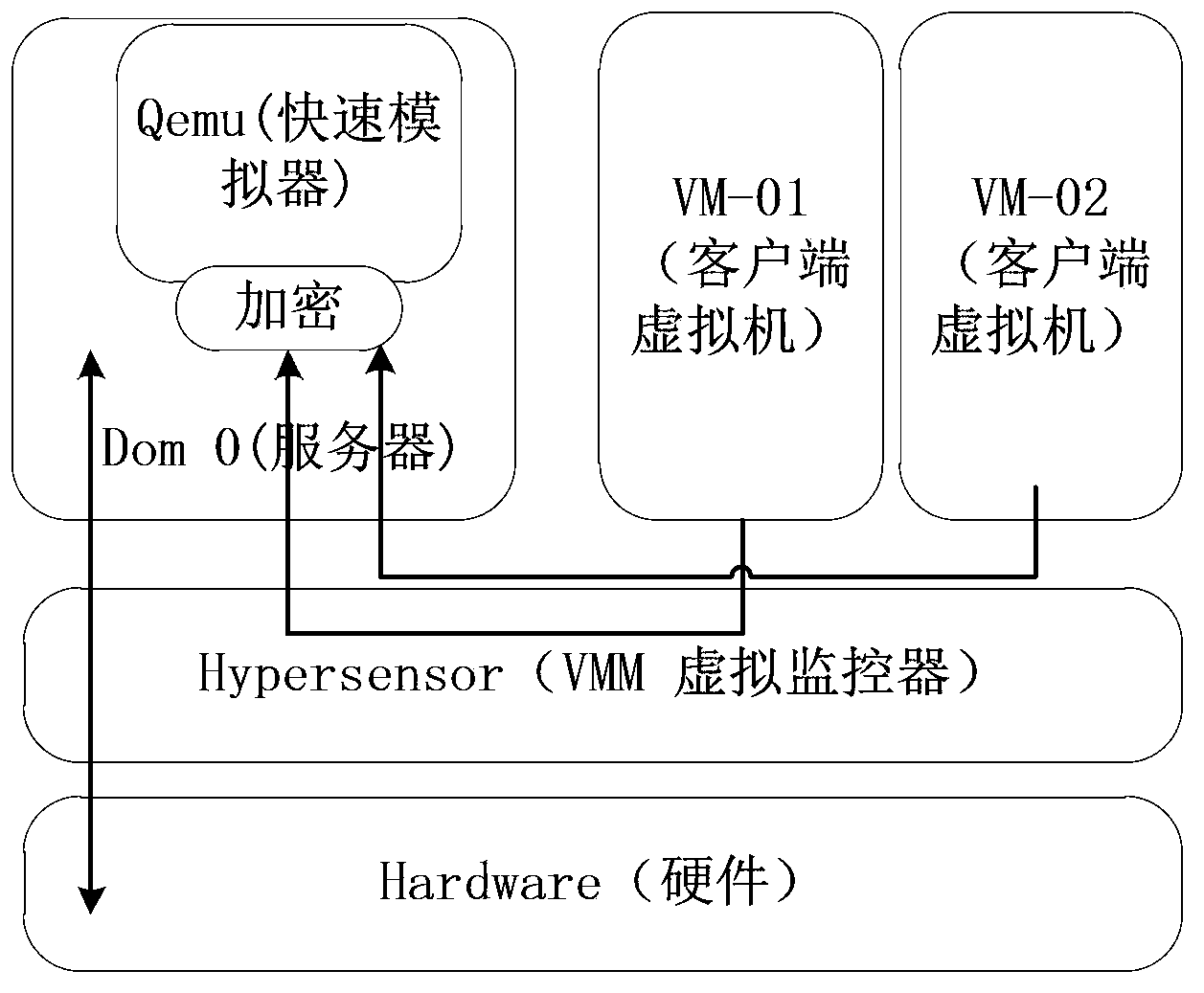
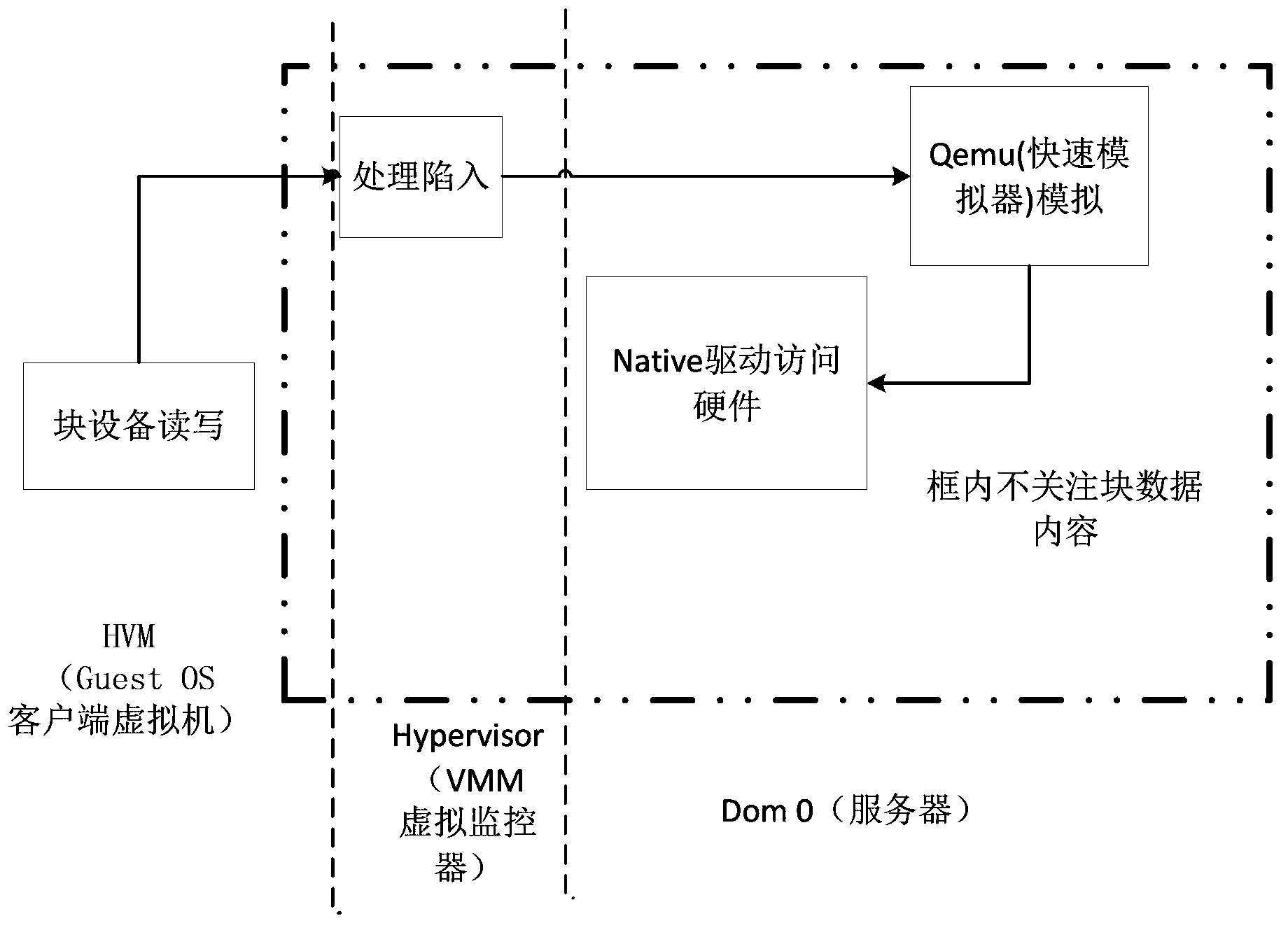
[0077] Specific embodiments of the present invention are as follows: (participate in figure 2 , image 3 with Figure 4 )
[0078] 1) When creating a new virtual machine, the key management system generates a key for this Dom U (client virtual machine), and establishes a mapping set UUID (Universally Unique Identifier) between the virtual machine and the corresponding key, and maps The table is stored in the local key database, and the generated protection key is placed on the remote server, which ensures that the key and the mapping table cannot be obtained at the same time, thereby improving the security performance of the key system.
[0079] 2) The client virtual machine Dom U and the remote server Dom0 are connected through a key: the key negotiation module sends a KC_HELLO packet to the remote server to request a secure connection; the remote server generates a large prime number ρ and Its original root integer r and the private key KA, after calculating the public...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com