A method for safe use of mobile phone QR codes based on information hiding
A technology of information hiding and two-dimensional code, which is applied in the recording carrier used by the machine, security device, wireless communication, etc., can solve the problems of information leakage, personal information leakage, and infringement of other people's rights and interests, and achieve clear division of labor, strong practicality and The effect of operability and structure system is simple and clear
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
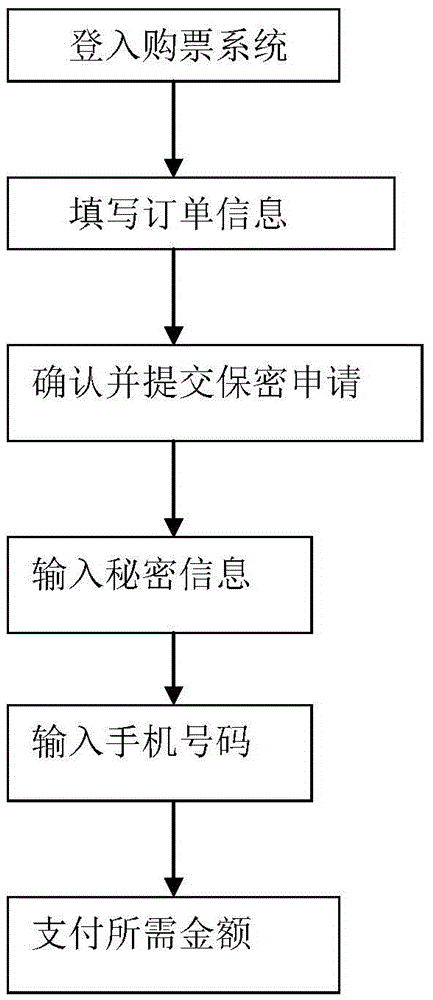
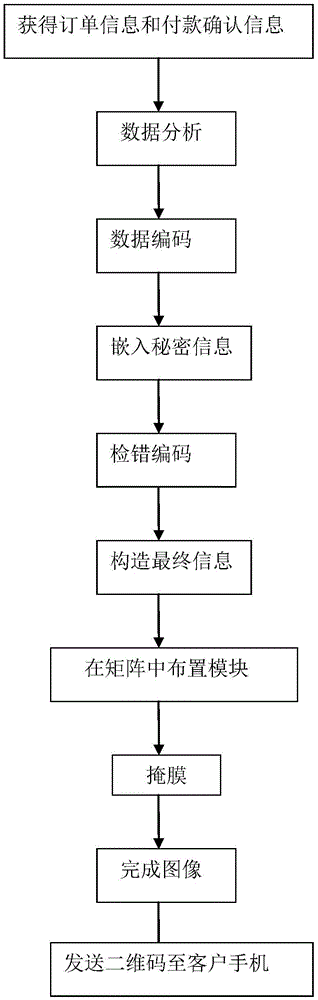
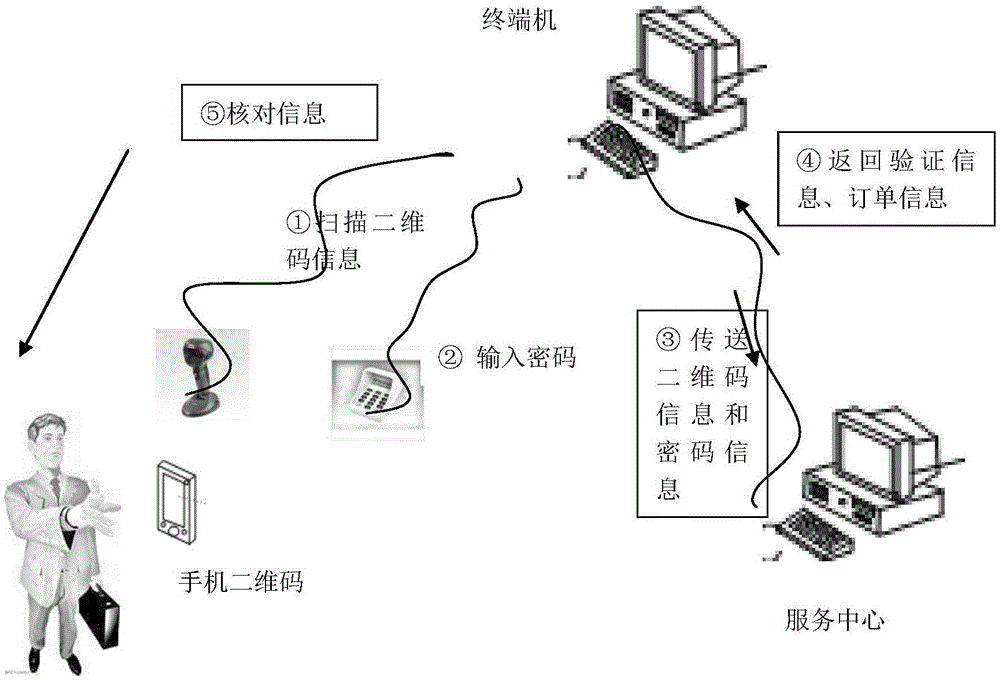
[0047] Here, the above-mentioned two-dimensional code safe use scheme is applied to daily life. Since there are many types of two-dimensional codes in reality, the present invention selects a representative QRCode code for detailed description. A is an ordinary user who needs to travel recently and has booked a plane ticket online. B is an employee of an airline. After receiving A's order, B returns a QR code to A as a voucher. C is an airport staff member who verifies the QR code held by A.
[0048] The specific implementation steps will be described in this case based on the above-mentioned method flow:
[0049] Step 1) A needs to book a ticket on the website of an airline company. The airline uses a mobile phone QR code to provide the flight certificate to the user. For safety reasons, A is required to enter secret information for the QR code certificate. Protect. Therefore, A provides personal name and ID number while adding personal secret information. To simplify the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com