Safety operation device and method taking safety criteria as working process auditing standards
A workflow and safe operation technology, applied in the direction of digital data authentication, etc., can solve the problem that the human brain cannot remember security events
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below through specific embodiments.
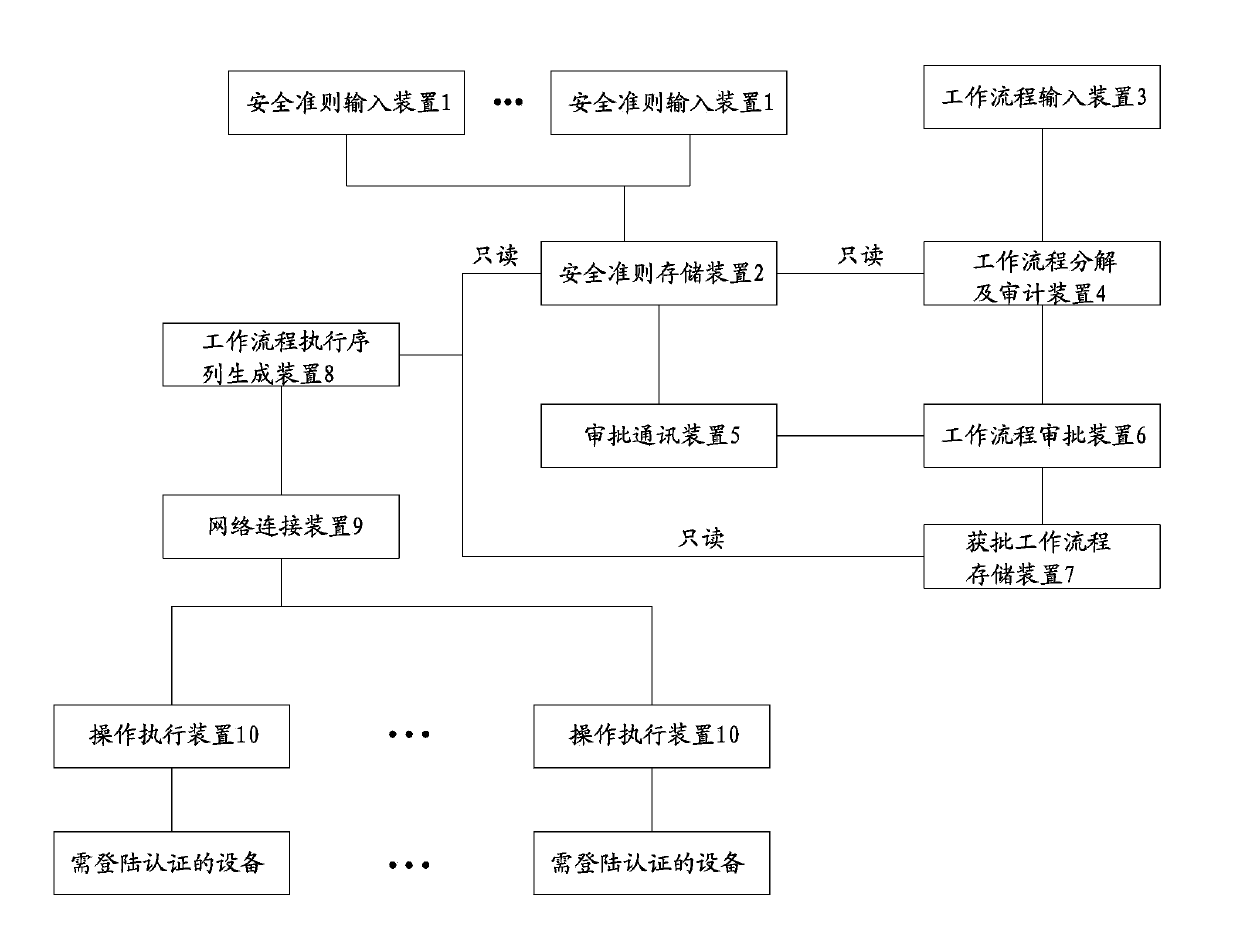
[0034] refer to figure 1 , a safety operation device with safety rules as the workflow audit standard, which is applied to equipment that needs to input login authentication information. The device is proposed by the operator to use the work process, and based on the safety rule, it automatically judges the compliance of these work processes , and then perform these operations on behalf of the operator. The operating right of this type of equipment is reviewed by the structured device described in the present invention and operated instead of the operator, which avoids the safety hazards caused by the illegal operation of the operator after obtaining the operating right or the fraudulent use of the operator after the authentication information is lost. event.
[0035] Specifically include the following:
[0036] The safety criterion input device 1 is used to input the safety criteri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com