Internet data distribution oriented identity authentication and data encryption method
A technology for data distribution and authentication, applied in the field of Internet data transmission, it can solve the problems of long time for data block encryption and decryption, and it is not suitable for controlled distribution of Internet data security, so as to achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
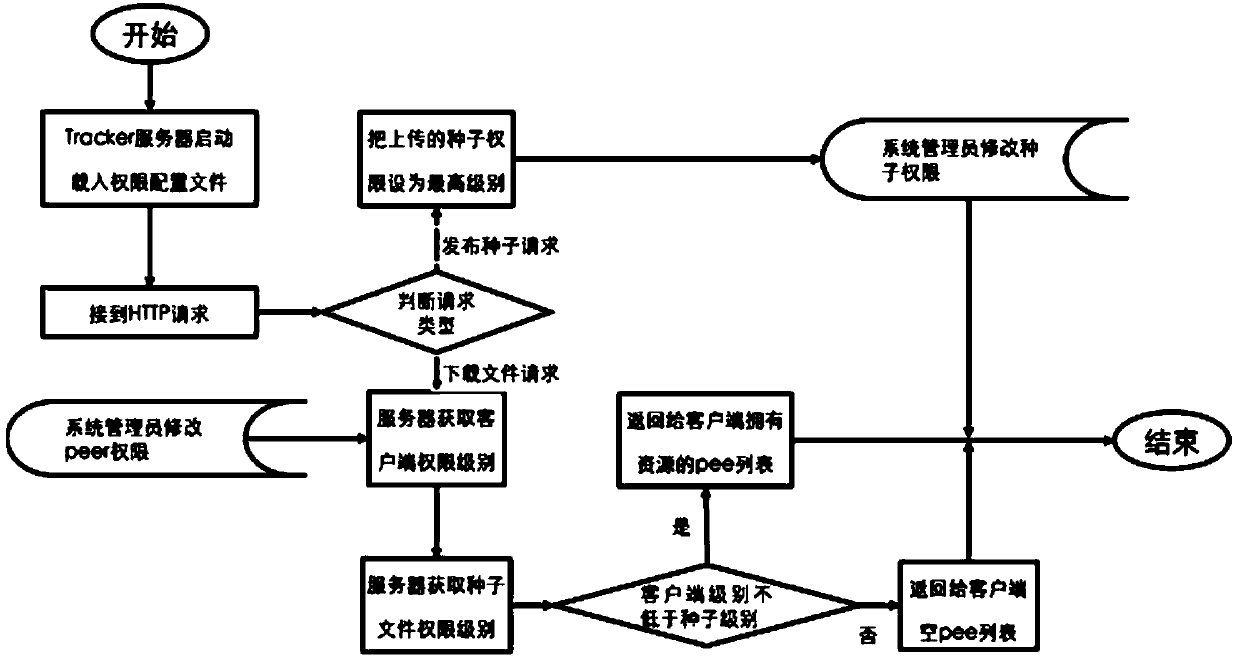
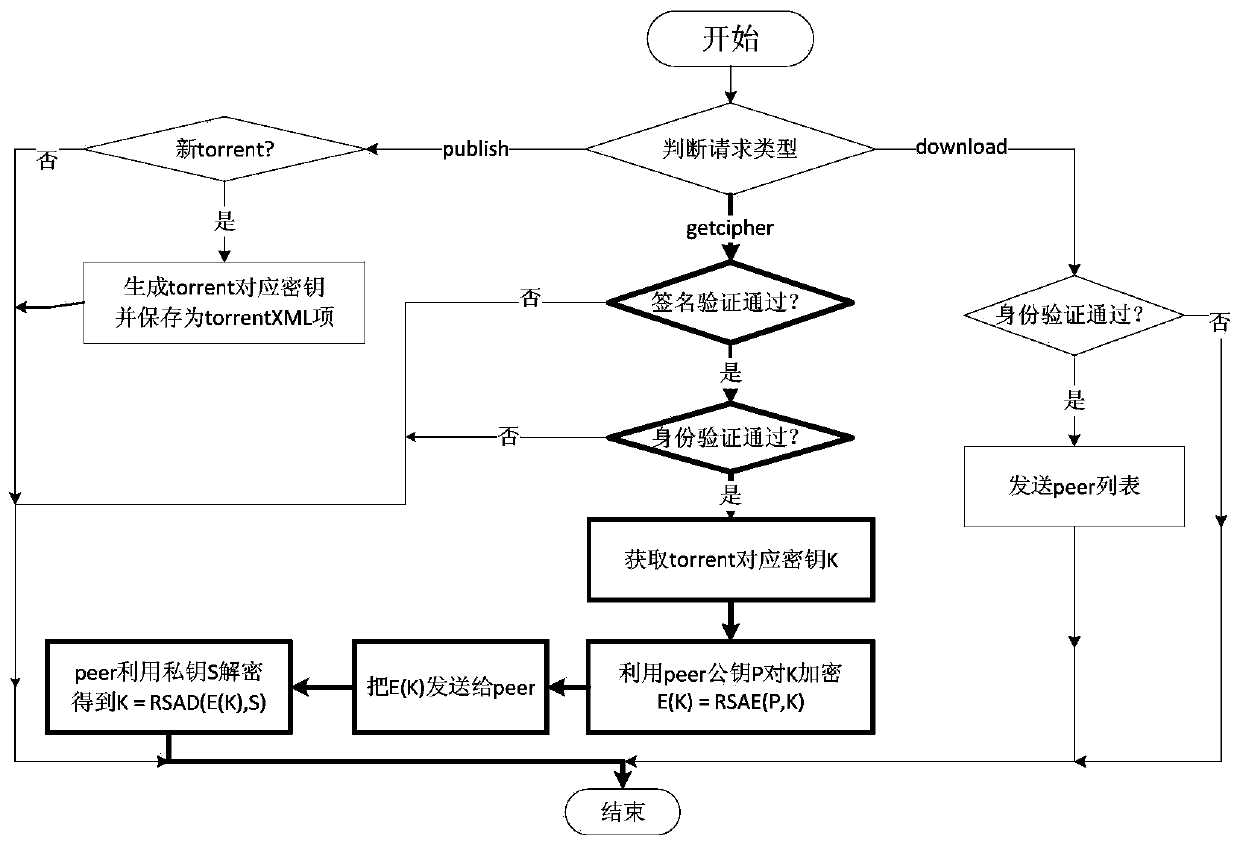
[0024] The method of the present invention mainly adopts the filtering mechanism of identity verification added in the BT protocol, and protects the data in the way of symmetrical encryption and point-to-point key distribution during data transmission, thereby realizing the Internet under the condition of security control. The purpose of efficient data distribution is to enable the controlled and safe transmission of data in the private network.
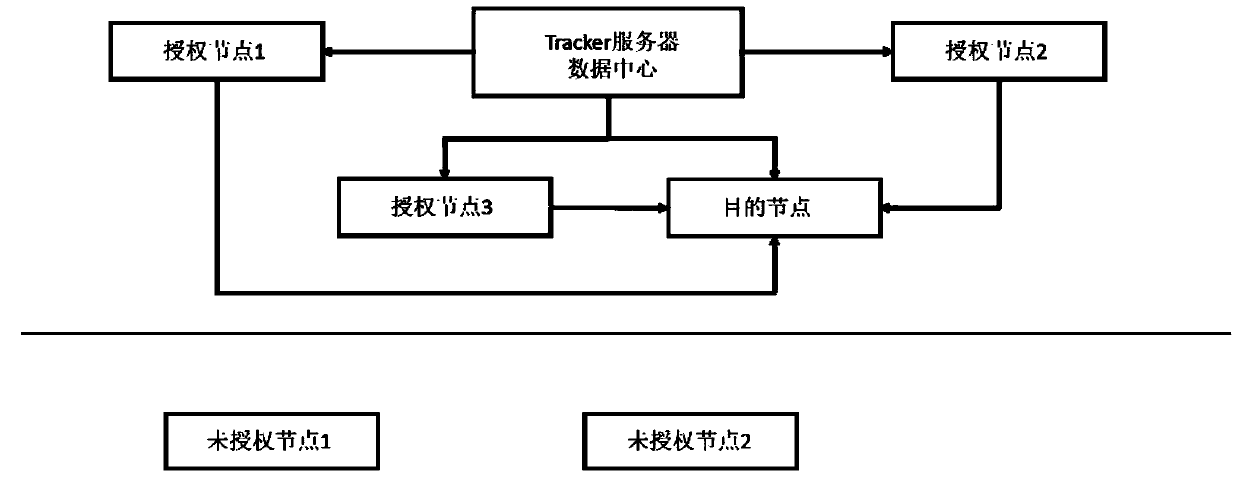
[0025] Such as figure 1 As shown, the composition of data distribution nodes in the BitTorrent environment mainly includes Tracker servers, data centers, and other client nodes (authorized nodes, destination nodes, or unauthorized nodes) in the network, where Tracker servers and data centers may or may not be located in the same place . The Tracker server is mainly responsible for the control and distribution of node information and file information, node verification and authorization, and saves the decryption key given by the data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com