Terminal safety protection method and system
A technology for terminal security and secure contacts, which is applied in the field of terminal security protection methods and systems, and can solve the problems of cumbersome operation process, users forgetting passwords, forgetting security mailbox accounts and passwords, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0096] refer to figure 1 , which shows a schematic flowchart of Embodiment 1 of a terminal security protection method according to the present invention, which may specifically include:
[0097] Step 110, adding at least one first contact to the secure contact database for the target contact; wherein, the target contact corresponds to the target terminal;
[0098] In the embodiment of the present invention, a secure contact database may be preset in the target server in various manners, and the target contacts are in one-to-one correspondence with the secure contact database. In the embodiment of the present invention, both the first contact person and the target contact person can be mobile phone numbers.
[0099] In this embodiment of the present invention, the target terminal itself may also be the first terminal. Target contacts can be added to their own secure contact database.
[0100] Preferably, adding at least one first contact to the secure contact database for th...
Embodiment 2
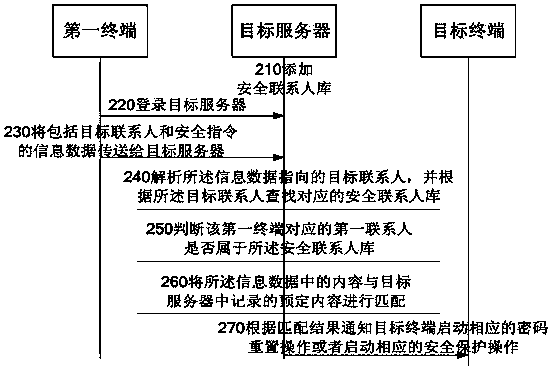
[0138] refer to figure 2 , which shows a schematic flowchart of Embodiment 2 of a terminal security protection method according to the present invention, which may specifically include:
[0139] Step 210, adding at least one first contact to the secure contact database for the target contact; wherein, the target contact corresponds to the target terminal;
[0140] This step is similar to step 110 and will not be described in detail here.
[0141] Step 220, the first terminal logs in to the website where the target server is located;
[0142] The first terminal logs in the website where the target server is located through wifi, or GPRS, or other methods.
[0143] Step 230, the first terminal transmits information data including target contacts and security instructions to the target server through the webpage of the website;
[0144] After the first terminal opens the webpage of the website, it can input the target contact in the webpage and select the operation to be perf...
Embodiment 3
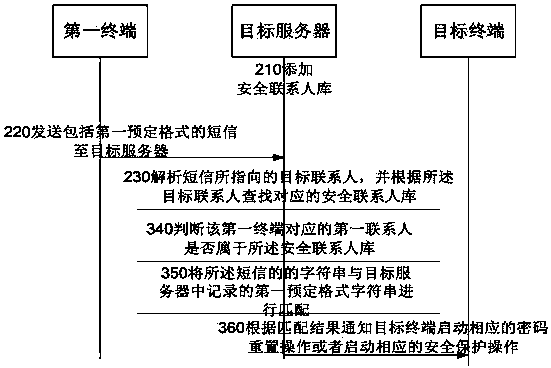
[0156] refer to image 3 , which shows a schematic flowchart of Embodiment 3 of a terminal security protection method according to the present invention, which may specifically include:
[0157] Step 310, adding at least one first contact to the secure contact database for the target contact; wherein, the target contact corresponds to the target terminal;
[0158] This step is similar to step 110 and will not be described in detail here.
[0159] Step 320, the first terminal sends a short message including a first predetermined format to the target server;
[0160] That is, the terminal can send a short message to the target server, wherein the short message needs to be edited according to the first predetermined format before the target server can perform subsequent processing.
[0161] In the embodiment of the present invention, it may be pre-agreed that character strings in the first predetermined format correspond to different operations. For example, "shanchu#verificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com