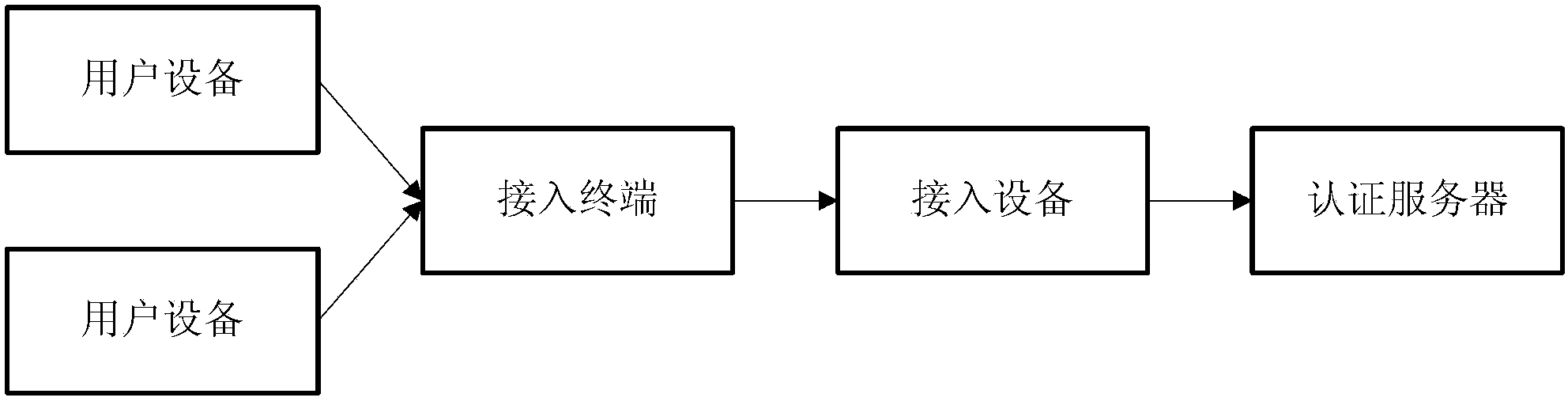
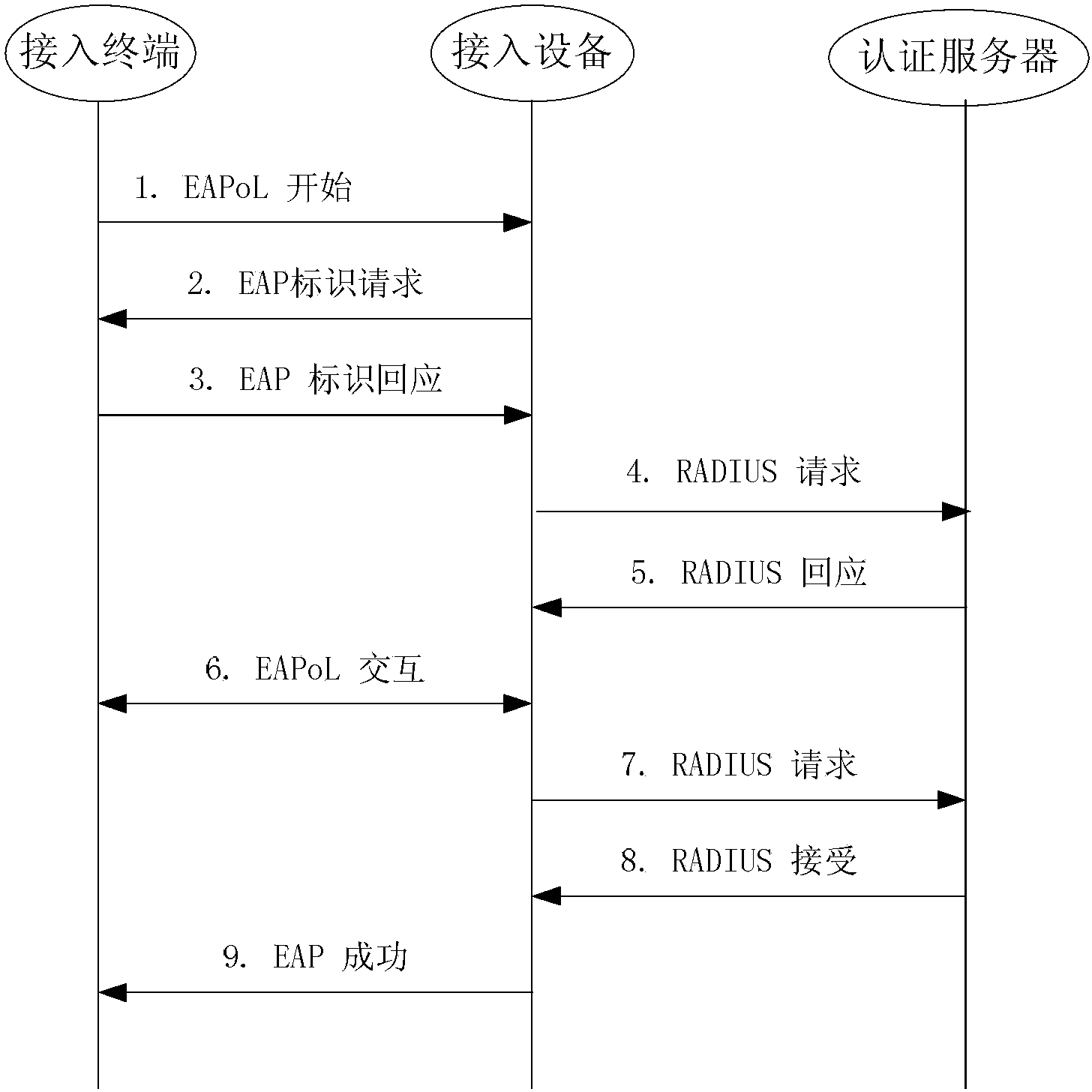
User service access processing method, access equipment and access terminal
A technology for access terminals and access devices, which is applied in transmission systems, electrical components, etc., and can solve problems such as the inability of processes to meet application requirements.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
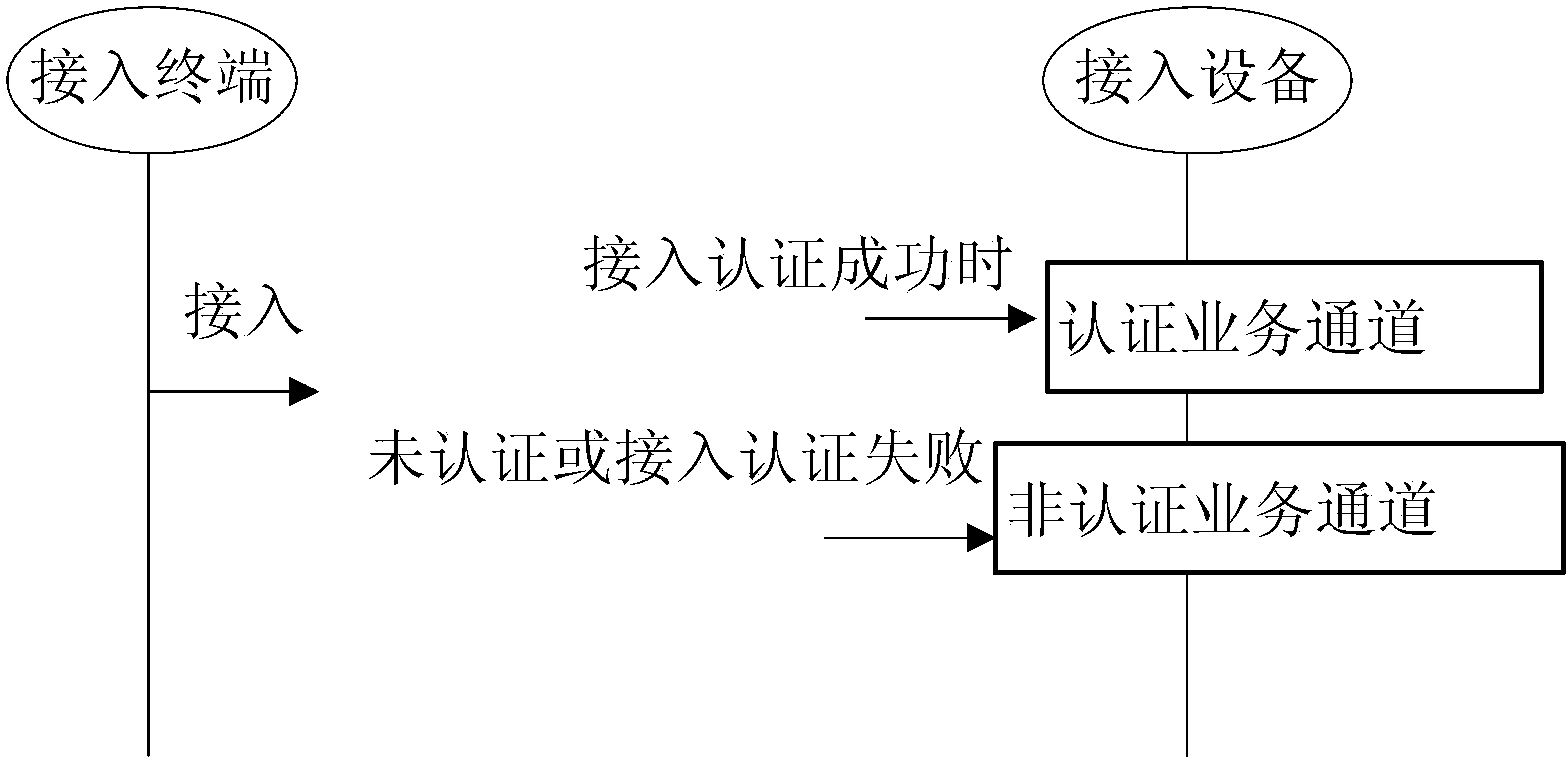
[0036] The access terminal configures the information of the non-authenticated service channel on the user-side port, and configures the information of the authenticated service channel on the user-side port when the authentication is successful, and maintains the configuration on the user-side port when it is not authenticated or the authentication fails. .
Embodiment 2
[0038] The access terminal configures the information of the authentication service channel on the user side port. When the access terminal is not authenticated or the access authentication fails, the access device forwards the data received from the authentication service channel through the non-authentication service channel. Specifically, the access device modifies the channel identifier of the data received from the authentication service channel to the identifier of the non-authentication service channel; when accessing through the user-side port and the authentication is successful, keep the Configuration.
[0039] The service channel in this method is the logical channel of virtual local area network or passive optical network or the virtual channel (VC) of digital subscriber line (DSL), and the logical channel of passive optical network is the general encapsulation of gigabit passive optical network (GPON) Port (GEM) or Ethernet Passive Optical Network (EPON) Logical L...
specific Embodiment 1
[0052] The access device is configured with N-1 authenticated service channels VLAN2 to VLAN N+1 and one non-authenticated service channel VLAN 1. The access device notifies the configuration information of each channel to the service channel of the access terminal.
[0053] The access terminal configures the non-authentication service channel VLAN 1 to N user-side port 1 to user-side port N.
[0054]If the access terminal is not authenticated or the authentication fails during the access process, the access terminal maintains the non-authentication service channel VLAN 1 configured on user-side port 1 to user-side port N. The access device maintains the configuration of the original service channel, and performs user data access through the non-authenticated service channel VLAN 1.
[0055] If the access terminal is successfully authenticated during the access process, the access terminal deletes the non-authentication service channel VLAN 1 configured on user-side port 1 to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com