Device and method for detecting Trojan horse remote shell behavior
A detection device and behavior technology, applied in the field of communication, can solve the problems of inability to detect Trojan horse shell behavior and high false alarm rate of new Trojan horse detection, and achieve obvious efficiency advantages, fast detection speed, and reduction of computing pressure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
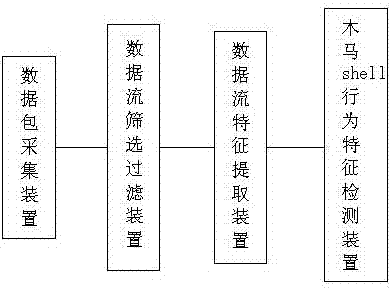
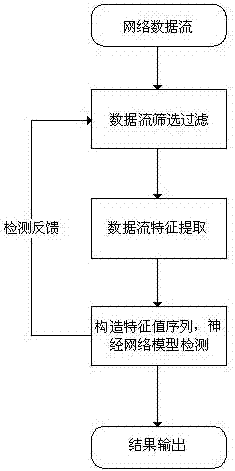
[0042] The key of the present invention is to extract the communication flow characteristics of the secret-stealing type Trojan horse remote shell behavior, then set up a neural network model with these communication characteristics, and use the learning algorithm, with the normal network data flow and the Trojan horse shell behavior communication flow data set. The network model is learned and trained, and the network parameters are adjusted and optimized.
[0043] Remote shell is a common function of most long-term latent / stealing Trojan horses. According to the implementation method of Trojan horse remote shell function and hackers' habit of using remote shell function, we selected the following three characteristics as the basis for traffic detection of Trojan horse shell behavior.
[0044] 1) The size ratio of data inflow packet load to outbound pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com