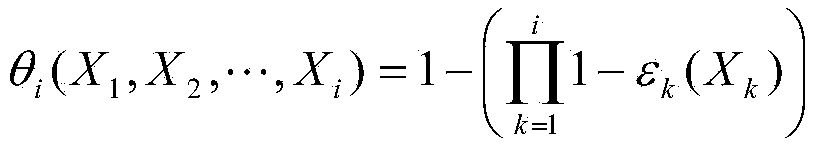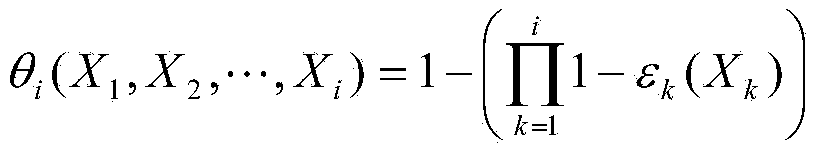Implicit user verification and privacy protection method based on multi-dimensional behavior characteristics
A privacy protection and user authentication technology, applied in the fields of implicit user authentication and privacy protection based on multi-dimensional behavioral characteristics, privacy user authentication and privacy protection, to achieve the effects of less attack, high security and low latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
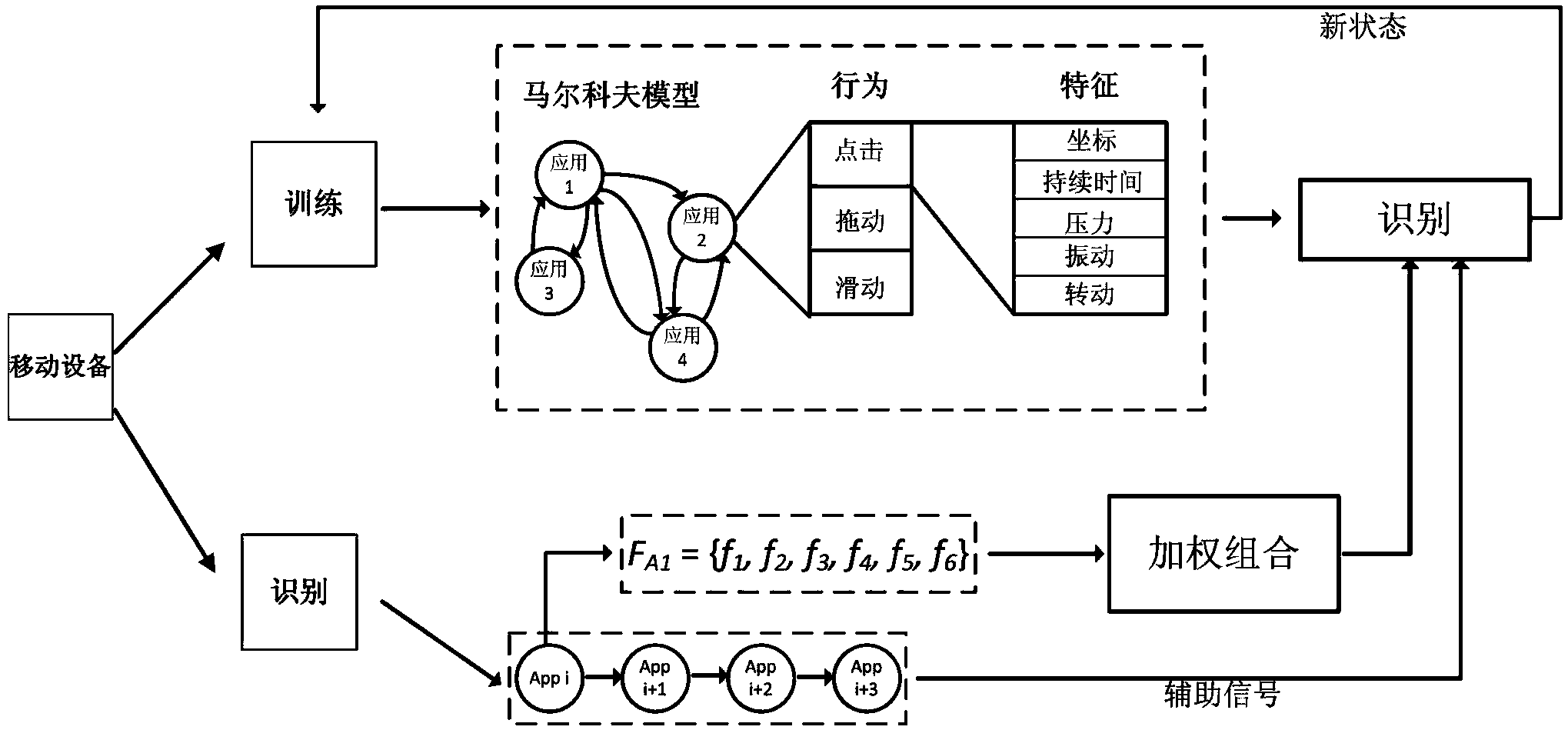
[0022] The present invention will be further described below in conjunction with specific drawings and embodiments.
[0023] Existing passwords are easy to be stolen or facial recognition methods are easy to be imitated, but the behavior patterns of different users using mobile devices, such as the applications they are used to and the location, force, and time of tapping the screen, are quite different and very different. It is difficult to be imitated, so the user's behavior pattern can be used as an invisible password for user authentication. For current touch-screen smart devices, such as mobile phones, when the user touches the screen of the mobile device, the device usually causes slight changes in position and posture. Since most of the current smart devices integrate motion sensors, these tiny responses to touch can be well reflected from the sensor data, and the responses of mobile phones usually have different characteristics during use by different users. In additi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com