Encryption device, encryption method and encryption program
一种加密装置、密码密钥的技术,应用在安全通信装置、编码/译码装置、多个键/算法的用法等方向,能够解决无法进行密码通信等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
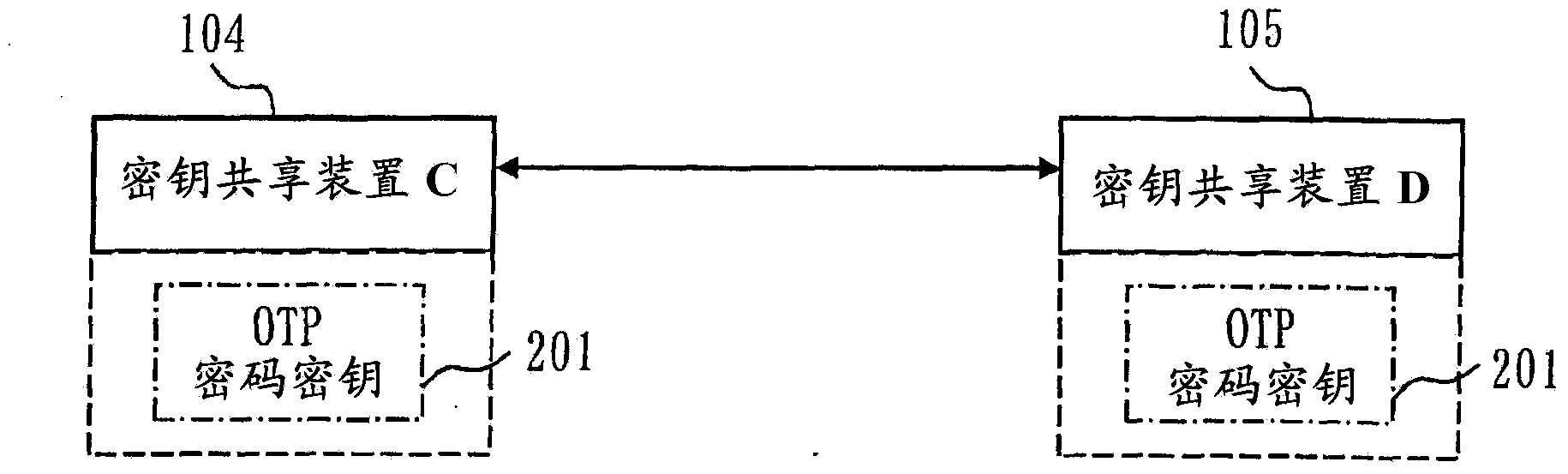
[0057] In Embodiment 1, a technique will be described in which, when the remaining amount (number of remaining bits) of an encryption key for one-time pad encryption (hereinafter referred to as an OTP encryption key) becomes smaller than a predetermined threshold value, the The encoding method of audio or the like is switched to a method (a method with a low bit rate) that reduces the amount of data when encoding audio or the like per unit time. Accordingly, the amount of OTP encryption keys consumed per unit time can be reduced, so the period until the OTP encryption keys are exhausted can be extended. Therefore, the OTP encryption communication can be continued for a longer period.
[0058] In addition, generally, when an encoding method with a higher bit rate is used, better sound quality or image quality is obtained, so when the OTP encryption key is sufficient, it is preferable to use an encoding method with a higher bit rate.
[0059] In Embodiment 1, the encoding metho...
Embodiment approach 2
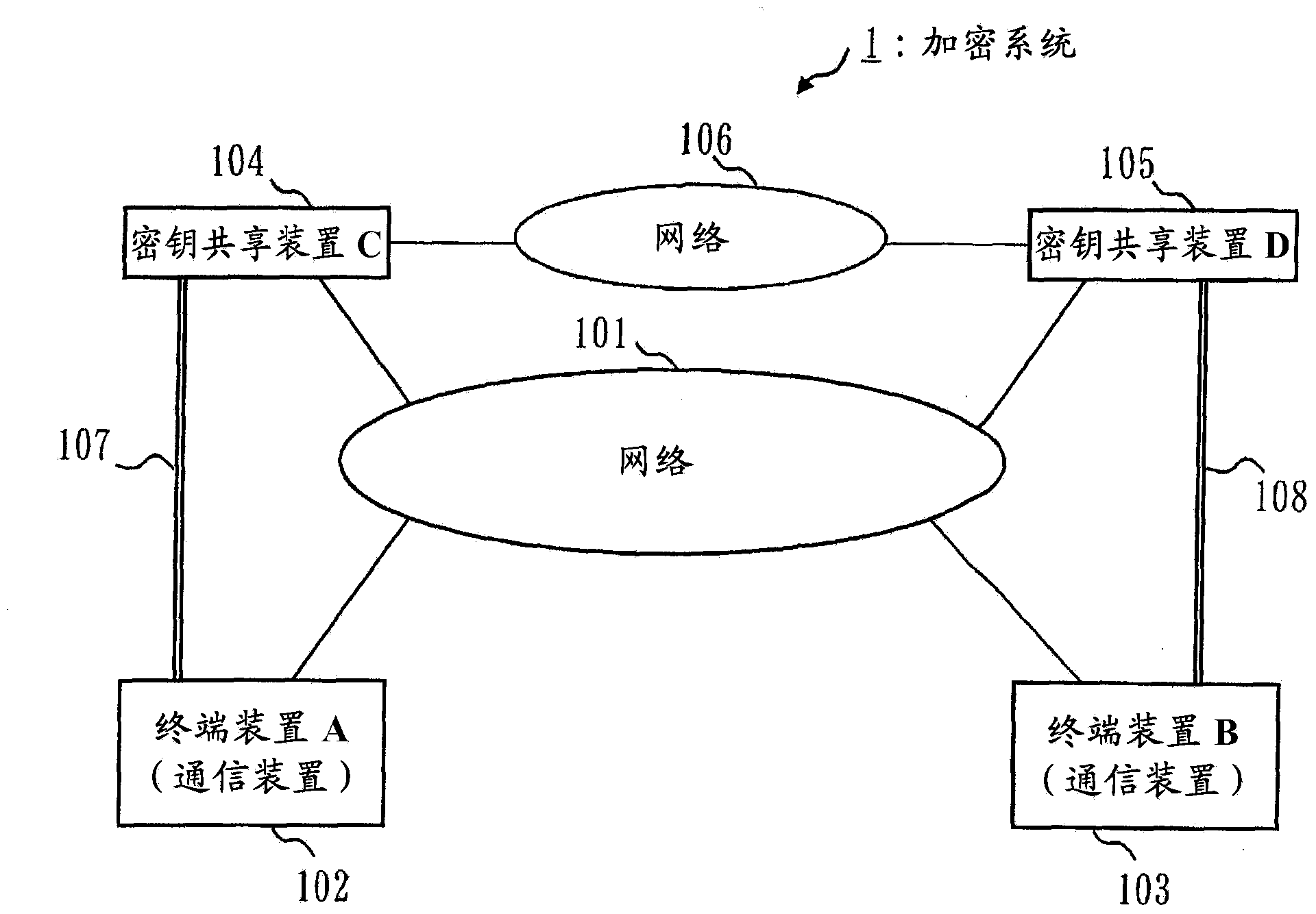
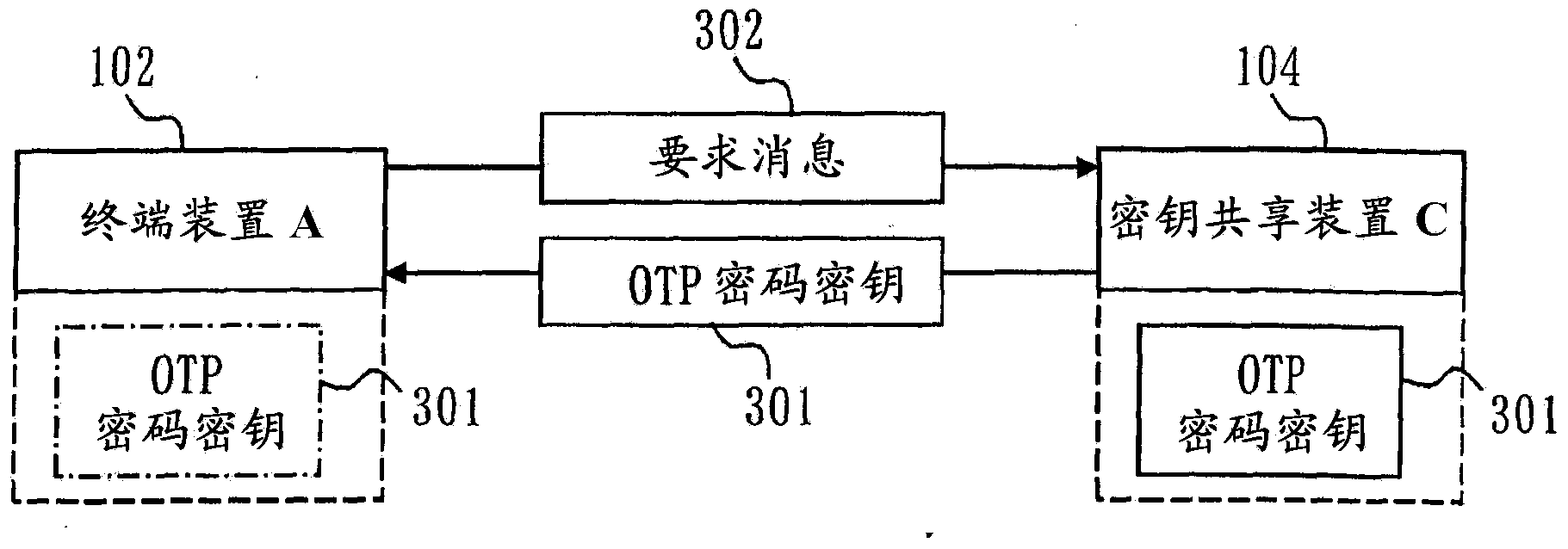
[0161] In Embodiment 1, the description has been made on the premise that the terminal device is connected to the key sharing device. However, for example, when the terminal device is a portable terminal such as a mobile phone, there may be a situation where the terminal device and the key sharing device are not connected. In this case, there may be a case where the timing for transferring the OTP encryption key from the key sharing device to the terminal device does not match between the terminal devices, and thus the amount of the encryption key held between the terminal devices differs. .
[0162] For example, it is assumed that the terminal device A102 acquires an OTP encryption key from the key sharing device C104 at a certain point of time. Thereafter, it is assumed that a new OTP encryption key is shared between the key sharing device C104 and the key sharing device D105. Furthermore, it is assumed that the terminal device B103 has acquired the OTP encryption key from...
Embodiment approach 3
[0205] In Embodiments 1 and 2, it is determined whether or not the remaining amount of the OTP encryption key held by the terminal device is equal to or greater than a predetermined threshold, and if it is equal to or greater than the threshold, an encoding method with a higher bit rate is used. In rare cases, a lower bit rate encoding method is used. However, for example, in the case of transmitting audio or video data which is more important than usual, a situation may arise where it is desired to prevent degradation of audio quality and image quality due to the use of a low bit rate encoding method. In this case, encoding should be performed with a higher bit rate. In addition, there may be a situation in which it does not matter if deterioration of sound quality or image quality occurs due to a coding method using a low bit rate. In this case, encoding should be performed at a lower bit rate to suppress consumption of OTP encryption keys.
[0206] Therefore, in Embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com