Safety identification method, between android application programs, based on user right
An Android application, identification method technology, applied in the direction of user identity/authority verification, digital data authentication, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
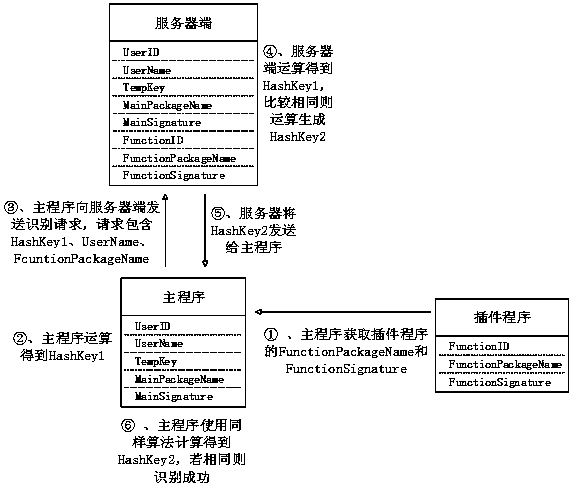
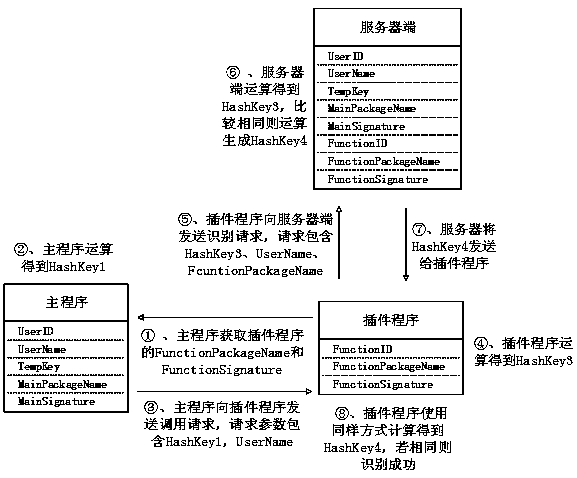
[0060] 1. When a user logs in in the main program, the main program performs character calculations on the user name and user password to obtain a string UserID containing user identification information, and the server also retains the UserID. After the user successfully logs in, the server will assign a time-sensitive verification code TempKey to the user. The TempKey is randomly generated and stored in the server for a short period of time (such as half an hour). After the timeout, the TempKey will become invalid. The server side also saves the package name and signature information of the main program and all plug-in programs, as well as the FunctionID used for identification of the plug-in programs.
[0061] A security identification method between Android application programs based on user rights in the present invention is based on three subjects in the Android system, the three subjects, one is the server side, and the other is the Android application program as the mai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com