Spyware Adaptive Induction and Detection Method Based on Computer Immunity
A detection method and computer technology, applied in the field of information security, can solve problems such as false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
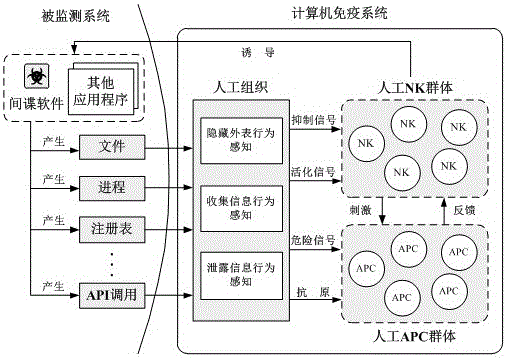
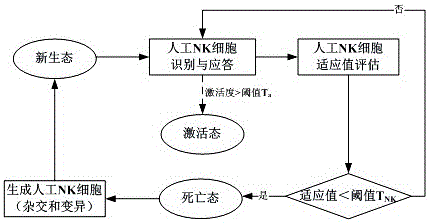
[0065] The technical method of the present invention will be described in detail below in conjunction with the accompanying drawings. The implementation process of the spyware adaptive induction and detection method and system based on computer immunity is mainly divided into five steps, and the specific implementation scheme of each step is as follows:
[0066] 1. System Behavior Perception
[0067] While spyware is low-key, certain behaviors are bound to be done in order to make a profit. The perception of these behaviors is the starting point for the computers immune system to detect insidious spyware. The inherent behavior of spyware falls into three main categories:
[0068] 1) Hide appearance behavior
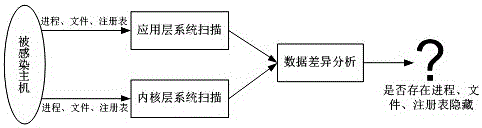
[0069] Spyware usually hides its own existence, which is mainly realized by hiding its own files, processes and related registry entries (used for the self-starting of spyware). Because normal applications rarely exhibit this behavior, when this behavior occurs, it ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com