A double-encrypted access control system based on mobile phone QR codes
An access control system and double encryption technology, applied in user identity/authority verification, instruments, time registers, etc., can solve the problem of insecurity and cost of access control system, and achieve the goal of increasing convenience, identifying safety and reliability, and improving security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings, but the content protected by the present invention is not limited to the following description.
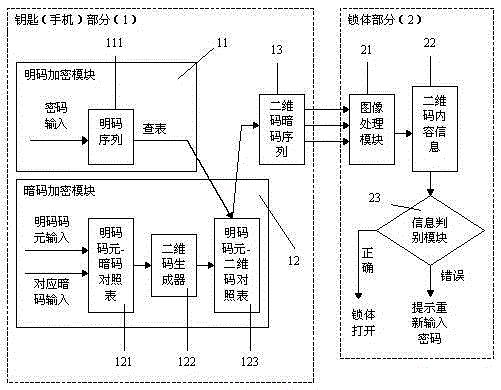
[0019] Such as figure 1 As shown, a double-encrypted access control system based on a mobile phone two-dimensional code, it includes a key part 1 and a lock body part 2, and the key part 1 includes a plain code encryption module 11, a secret code encryption module 12 and a two-dimensional code password sequence module 13. The lock body part 2 includes an image processing module 21 and an information discrimination module 23:
[0020] Plain code encryption module 11: the user manually inputs a password to obtain a plain code sequence 111;
[0021] Cipher encryption module 12: Obtain the plain code symbol-cipher code comparison table 121 by the plain code element input in turn and set the corresponding password, and then the password in the plain cod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com