Method for encrypting format-preserved numeric type personally identifiable information
A technology for identifying information and encryption methods, which is applied in the field of encryption of numerical personal identification information, and can solve problems such as corrupted data formats and data that cannot be stored
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
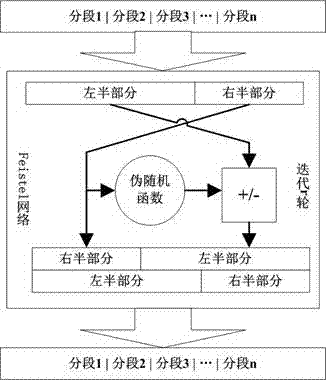
[0042] Numerical personal identification information includes ID card number, bank card number, etc. The present invention takes ID card number as an example to explain in detail the encryption method of the reserved format.
[0043] 1. Encryption algorithm
[0044] First, divide a legal 18-digit ID card number into six parts: I={I 1 , I 2 , I 3 , I 4 , I 5 , I 6 }, respectively represent the area code, birth year, birth month, date of birth, random number and check code. Among them, the length of each part is: |I 1 |=6, |I 2 |=4, |I 3 |=2, |I 4 |=2, |I 5 |=3, |I 6 |=1; the value range of each part is: I 1 ={0, …, 999999}, I 2 ={1900, …, 2050}, I 3 ={1, …, 12}, I 4 ={1, …, 31}, I 5 ={1, …, 999}, I 6 ={1… 9, ‘X’}; where I 6 The value of can be obtained by using the check code operation on the first five parts.
[0045] Use input = i 1 || i 2 || i 3 || i 4 || i 5 Represents a legal ID number, where: i 1 ∈I 1 , I 2 ∈I 2 , I 3 ∈I 3 , I 4 ∈I 4 , I 5 ∈I 5 . In order to ensure the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com