Identity authentication method and system
A technology of identity authentication and contact information, applied in the field of information security, can solve problems such as users cannot log in in time, and it is difficult to retrieve user names or passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
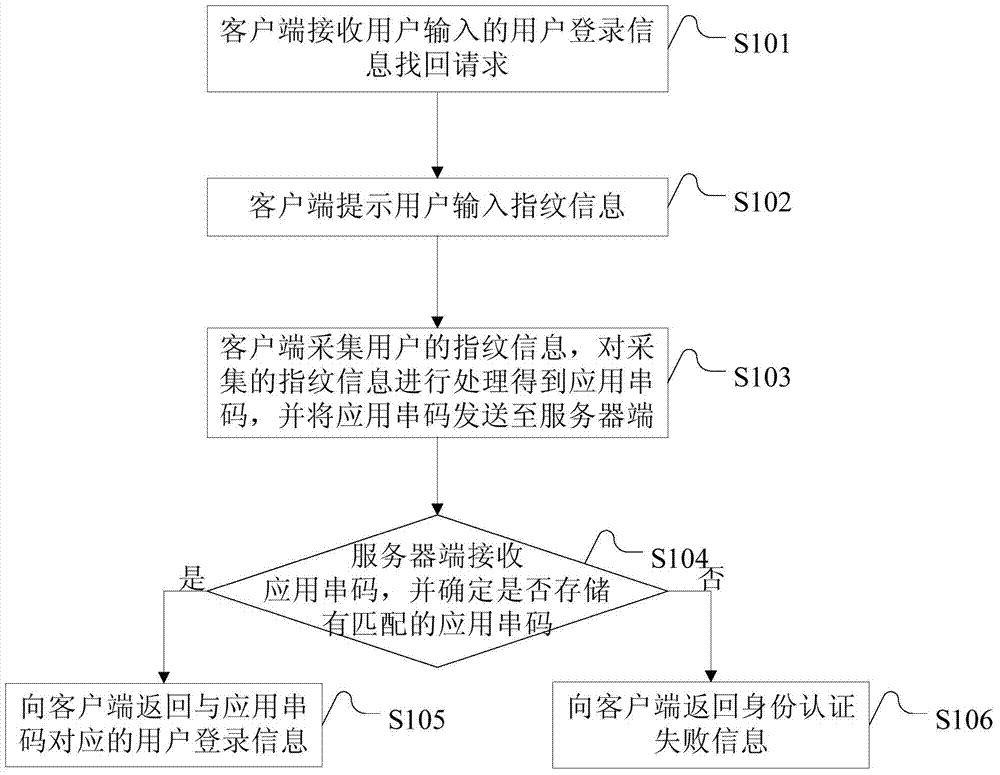
[0023] Such as figure 1 As shown, it is a schematic flowchart of Embodiment 1 of the identity authentication method provided by the present invention, which specifically includes the following steps:
[0024] S101. The client receives a user login information retrieval request input by the user;
[0025] S102. The client prompts the user to input fingerprint information;
[0026] S103. The client collects the fingerprint information of the user, and sends the application serial code to the server;
[0027] S104. The server receives the application serial code, and determines whether there is a matching application serial code; if yes, execute step S105; if not, execute step S106.
[0028] S105. The server returns the user login information corresponding to the application serial code to the client;
[0029] S106. The server returns identity authentication failure information to the client.
[0030] Those skilled in the art can understand that the above-mentioned user login...
Embodiment 2
[0033] Such as figure 2 As shown, it is a schematic flow diagram of Embodiment 2 of the identity authentication method provided by the present invention. The method steps described in this embodiment are to perform user registration before the steps performed in Embodiment 1 above, and specifically include the following steps:
[0034] S201. When the user registers, the client receives the user registration information input by the user, collects the user's fingerprint information, and processes the collected fingerprint information to obtain an application serial code, and the user registration information includes the user login information;
[0035] S202. The client binds the user registration information and the application serial code, and sends the bound user registration information and the application serial code to the server for storage.
[0036] In addition, the above-mentioned user registration information may include not only user login information, but also cont...
Embodiment 3
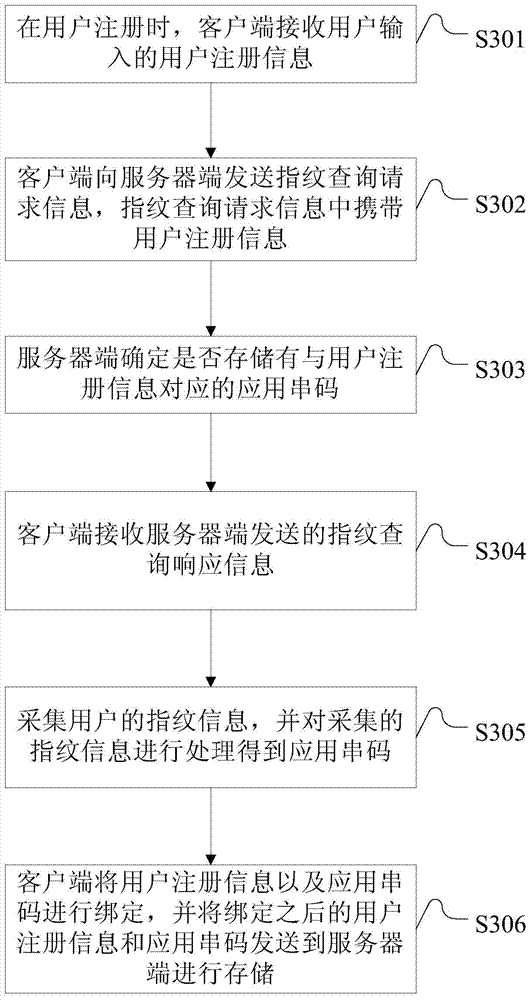
[0039] Such as image 3 As shown, it is a schematic flowchart of the third embodiment of the identity authentication method provided by the present invention. The method steps described in this embodiment are based on the above-mentioned embodiment two. When the user registers, the client receives the user registration information input by the user Afterwards, before collecting the user's fingerprint information, a step of judging whether the user has collected fingerprint information is added, which specifically includes the following steps:
[0040] S301. When the user registers, the client receives user registration information input by the user;
[0041] Wherein, the user registration information includes user name, password, and may also include contact information for receiving retrieved user login information such as email address, mobile phone number, MSN number, QQ number, WeChat account number, and Weibo account number.
[0042] S302. The client sends fingerprint qu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com