Android malicious software detecting platform oriented to mobile internet
A mobile Internet and malware technology, applied in the field of Android malware detection platform, can solve problems such as economic loss and user privacy leakage, and achieve the effect of improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Specific embodiments of the present invention will be described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention. It should be noted that in the following description, when detailed descriptions of known functions and designs may dilute the main content of the present invention, these descriptions will be omitted here.
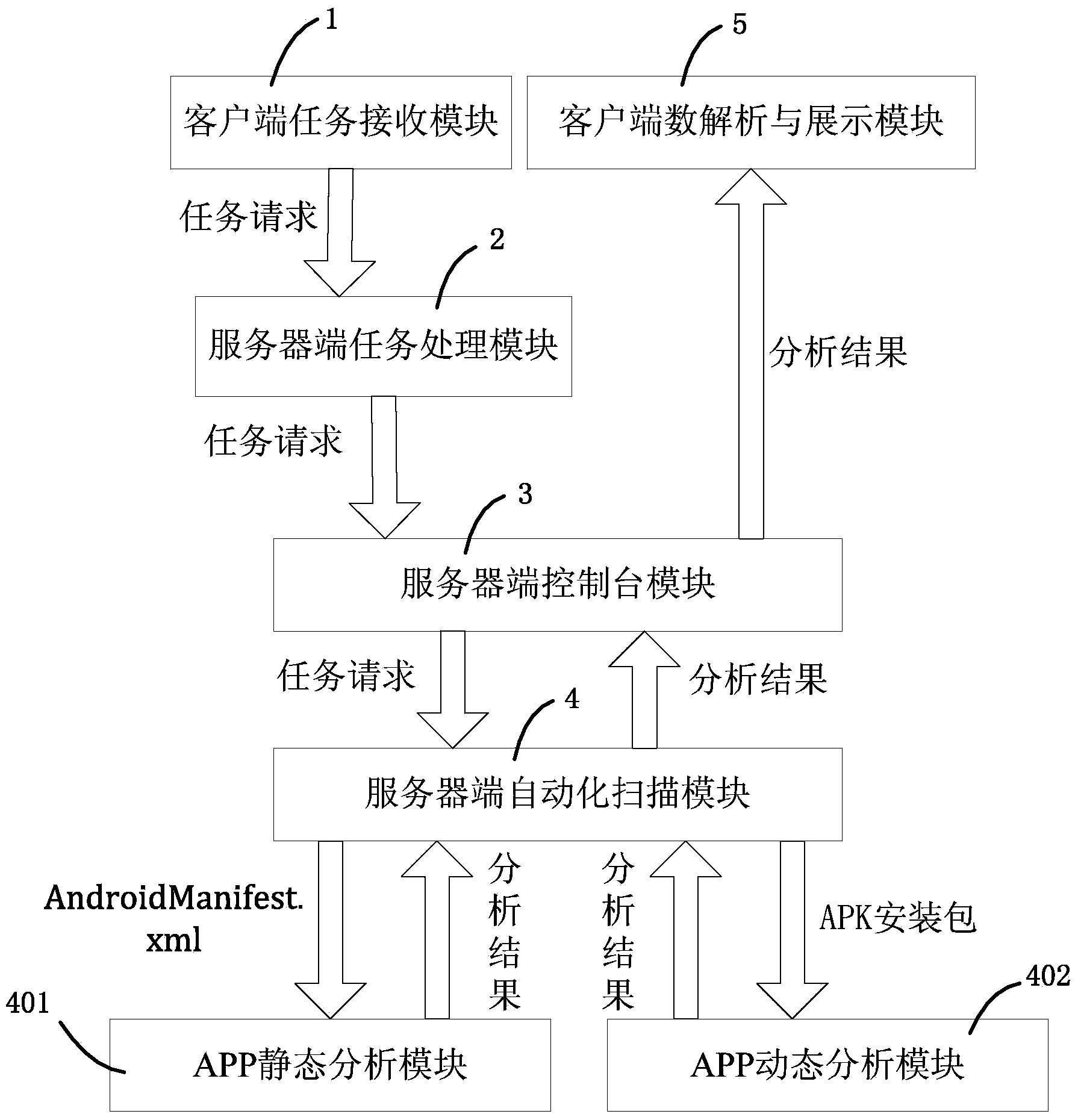
[0026] figure 1 It is a functional block diagram of a specific embodiment of the mobile Internet-oriented Android malicious software detection platform of the present invention.
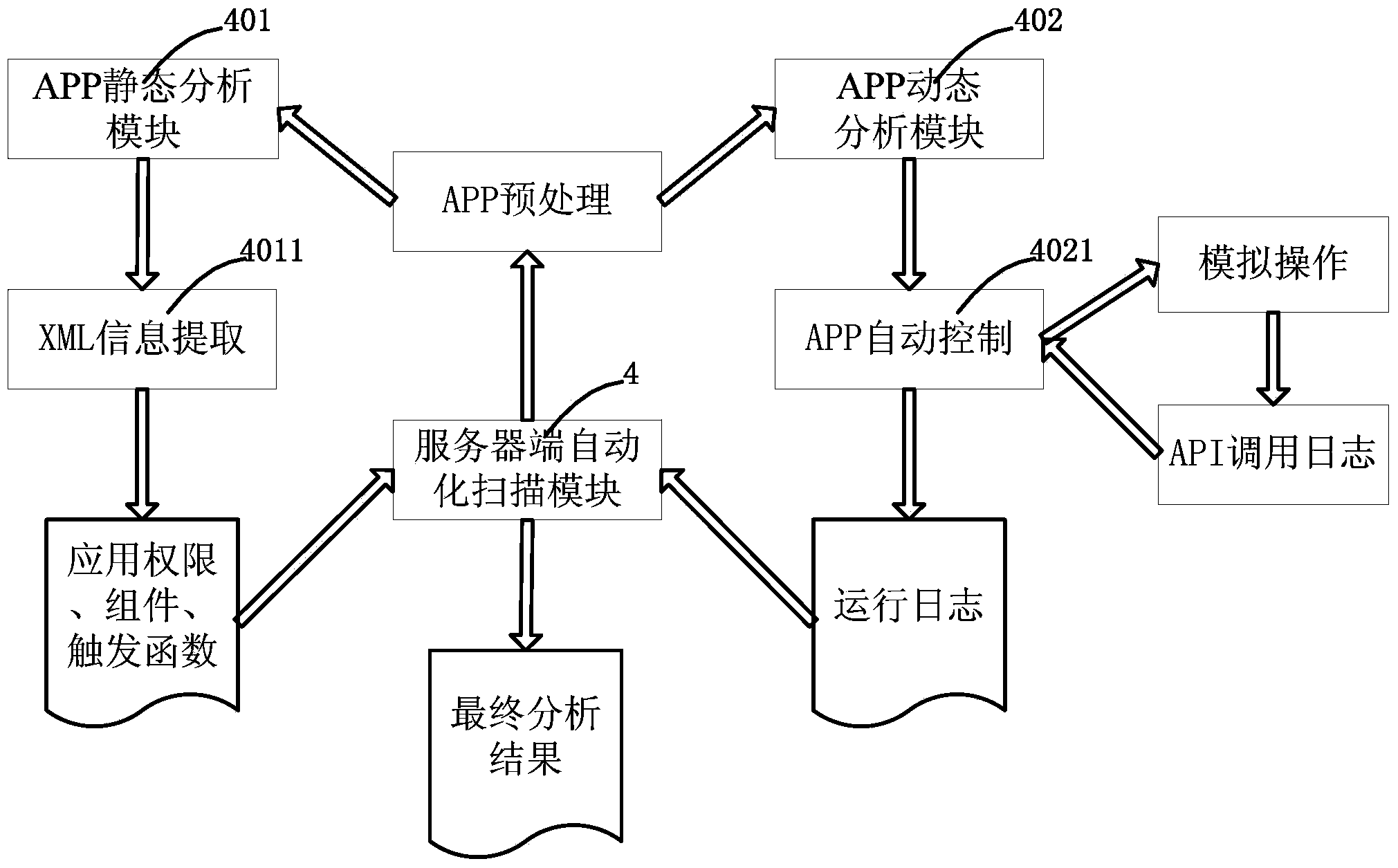
[0027] In this example, if figure 1 As shown, the mobile Internet-oriented Android malware detection platform of the present invention includes a client task receiving module 1, a server-side task processing module 2, a server-side console module 3, a server-side automatic scanning module 4, and a client-side result analysis and display module 5. The server-side automatic scanning module 4 furth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com