Access control method of resources of Android system
A system resource and access control technology, applied in the field of access control for Android system resources, can solve problems such as complex implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
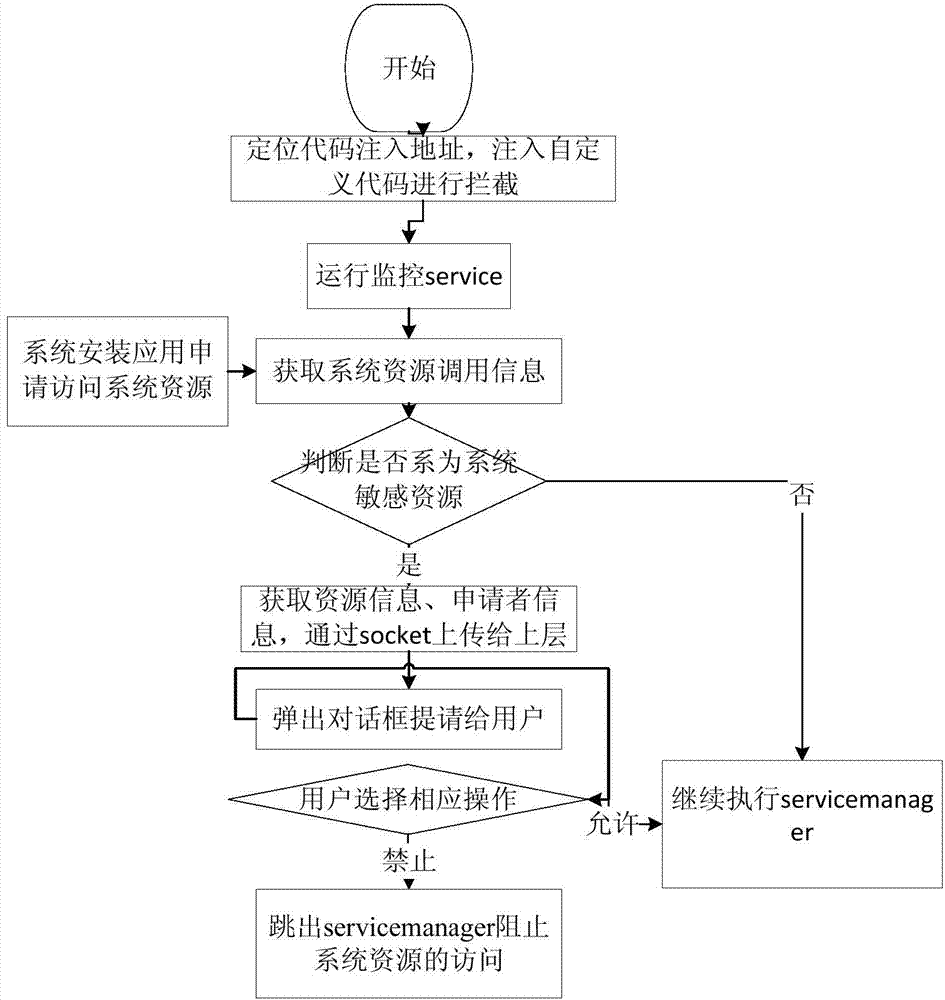
[0026] The present invention will be further described in detail in conjunction with the accompanying drawings and specific embodiments.
[0027] The present invention is an access control method oriented to Android system resources, through which the access control of all sensitive system resources shown in Table 1 is realized, and can be effectively intercepted, specifically comprising the following steps:
[0028] Step 1: Obtain the code injection address of ServiceManager: including the starting address addr1 and offset address addr2 of ServiceManager processing resource requests;
[0029] The present invention finds that ServiceManager is the entry point for processing system resource calls and access. When an application needs to apply for system resources (such as microphones, cameras, etc.), ServiceManager will be started first, and then ServiceManager will perform corresponding processing according to the request. By analyzing the ServiceManager source code, it is obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com