Security isolation management and control system
A technology of safety isolation and management and control system, applied in the field of safety isolation management and control system, it can solve problems such as hidden dangers of equipment failure, influence of existing network, inability of emergency communication network application scenarios and business needs to meet requirements, etc., and achieve the effect of satisfying users without feeling.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the technical solutions in the embodiments of the present invention are clearly and completely described below in conjunction with the drawings in the embodiments of the present invention:
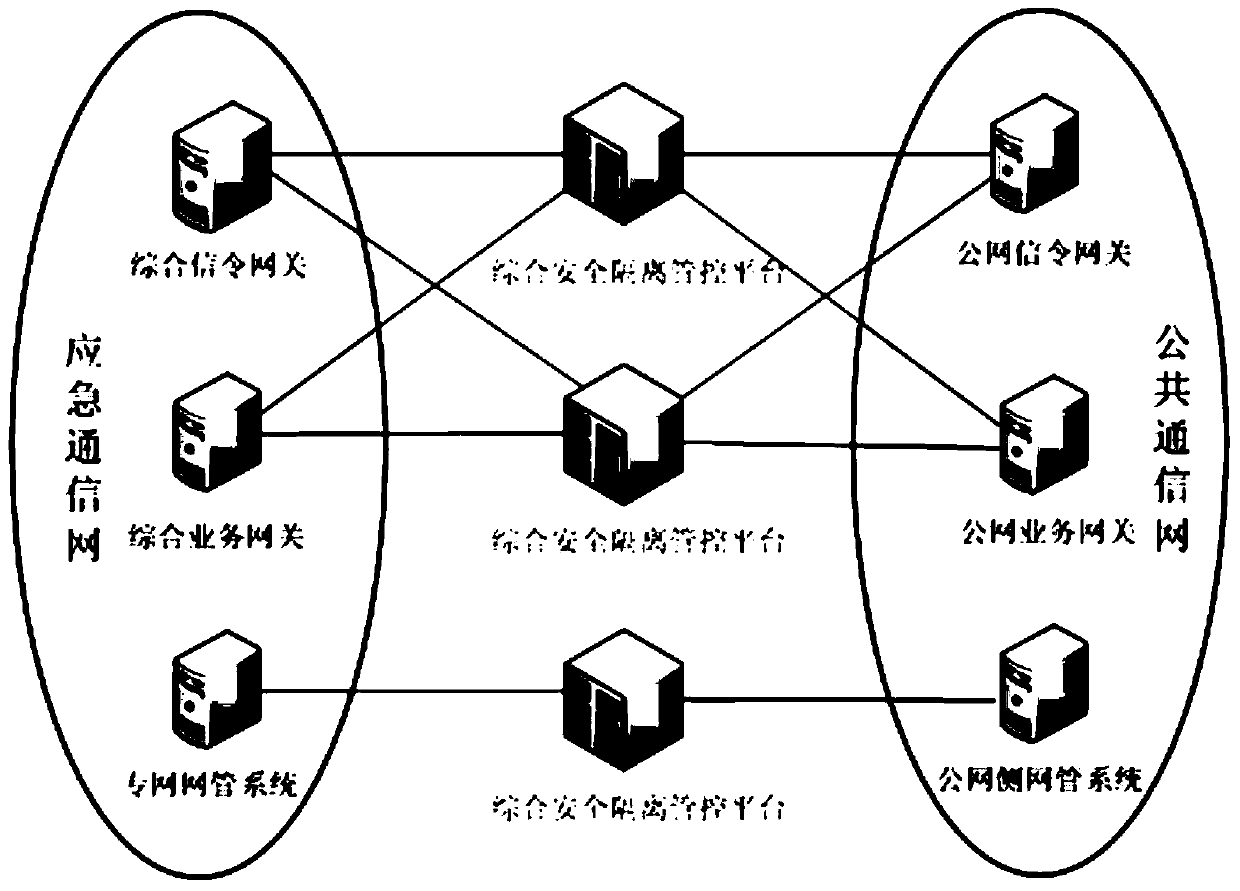
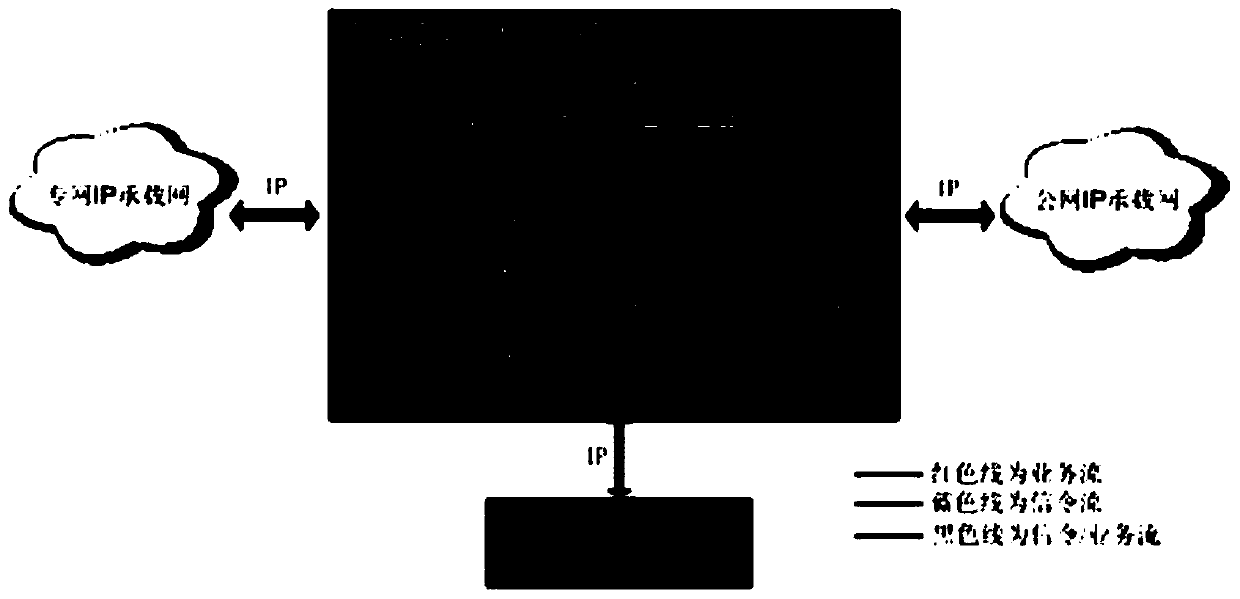
[0046] Such as Figure 1-Figure 12 Shown: below in conjunction with accompanying drawing, the present invention is described in detail: the comprehensive security isolation management and control platform of the present invention is divided into front-end equipment and back-end equipment according to physical entities, and its system composition and configuration are as follows: figure 2 .
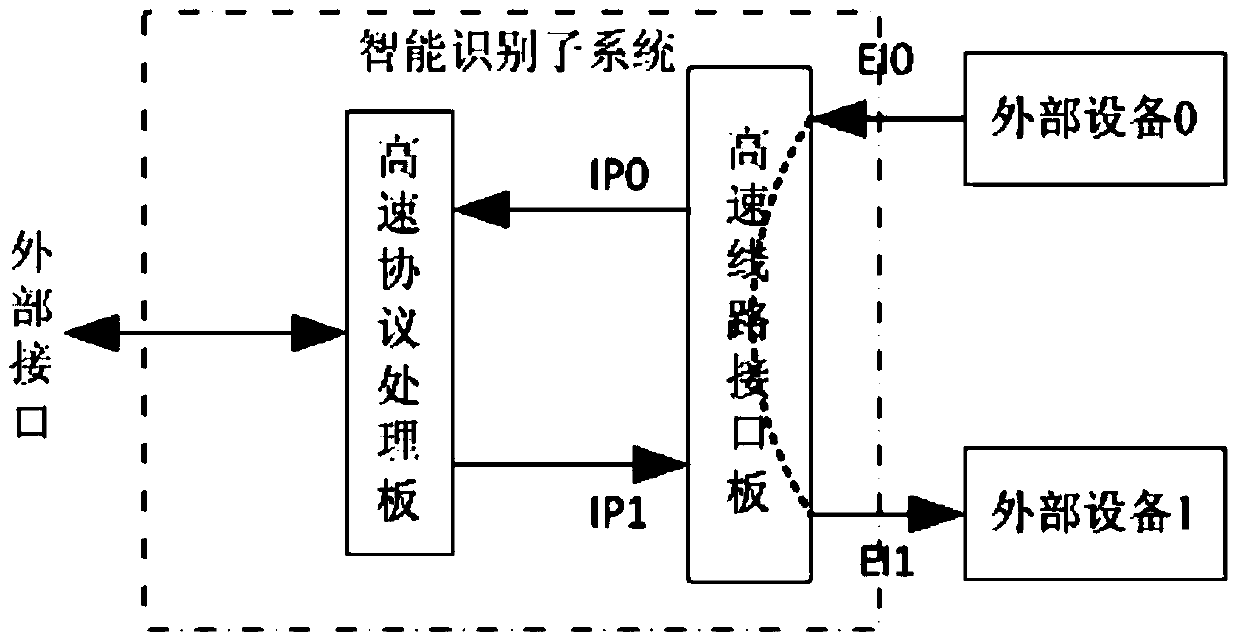
[0047] The front-end equipment is an independent hardware equipment, including the management and control operation subsystem and the intelligent identification subsystem. The front-end equipment is deployed in series on the private network link to perform line-speed identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com