Method and device for accessing shared resources
A technology for sharing resources and identification, applied in the field of data communication, can solve the problem of long time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0082] Embodiment one (such as image 3 shown):
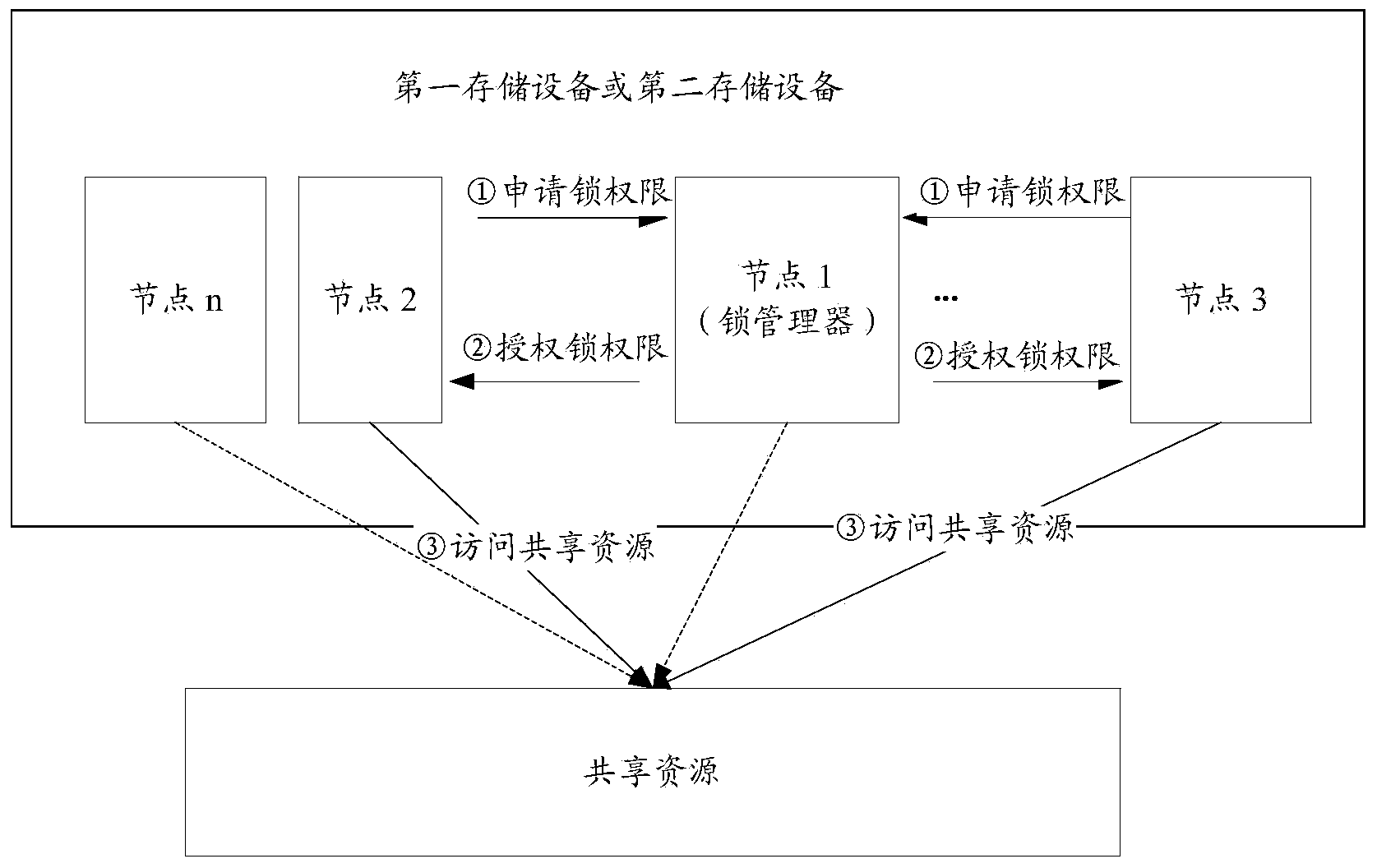
[0083] Step 300: Client 1 sends a lock permission request to access shared resource 1 to the first node where it is located;
[0084] Step 310: The first node judges whether the lock identifier corresponding to the shared resource 1 is stored in the first node and the lock identifier is not allocated, if so, execute step 350, otherwise, execute step 320;
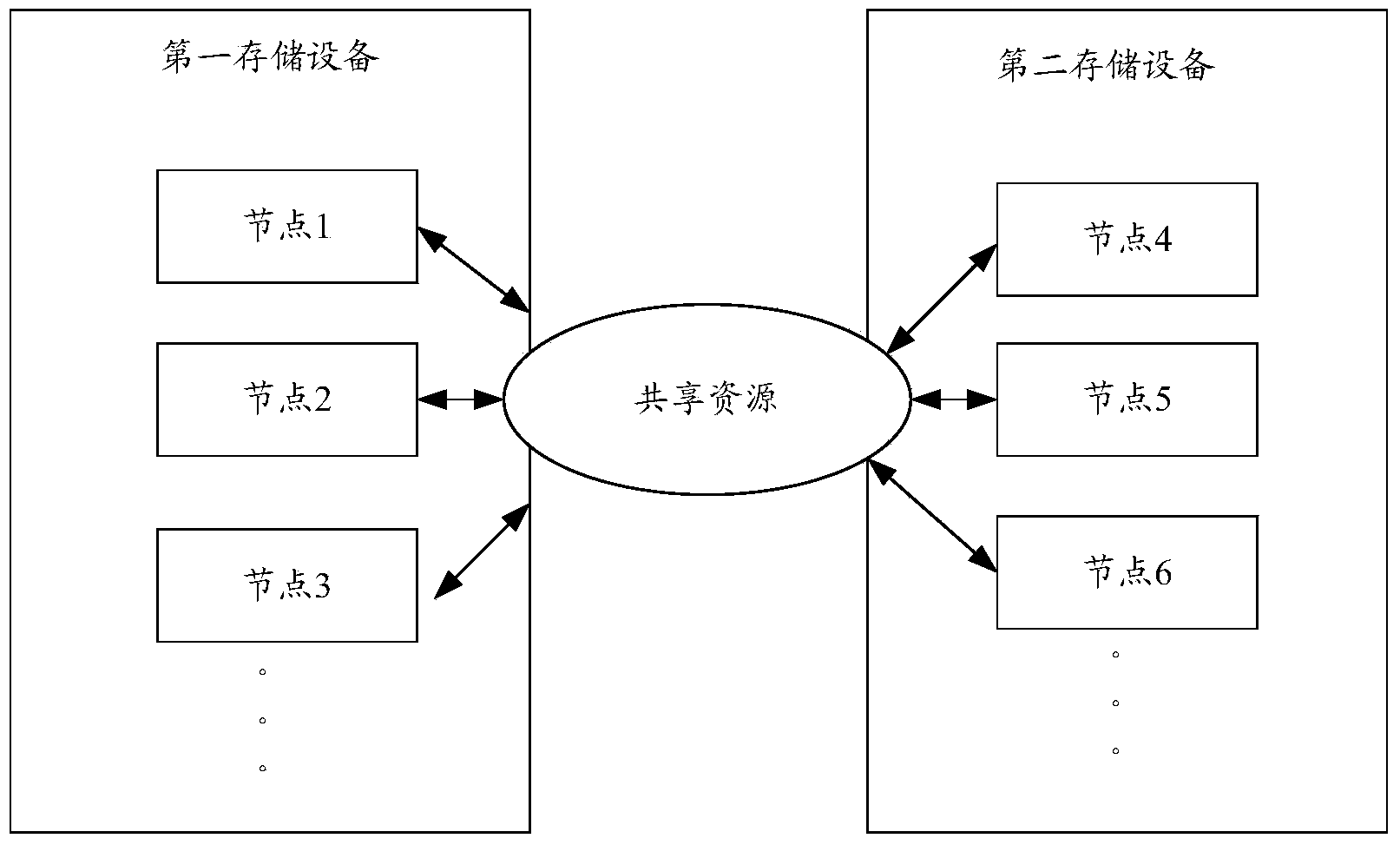
[0085] Step 320: the first node sends a lock permission request to access the shared resource 1 to the lock manager;
[0086] Wherein, the lock manager is located in the second storage device.
[0087] Step 330: The lock manager judges whether the lock identifier corresponding to the shared resource 1 is stored in the first node, and the lock identifier is not allocated; if so, execute step 340; otherwise, execute step 360;
[0088] Step 340: The lock manager sends the lock identifier corresponding to the shared resource 1 to the first node;
[0089] Step 350: the first n...
Embodiment 2
[0091] Embodiment two (such as Figure 4 shown):
[0092] Step 400: Client 1 sends a lock permission request to access shared resource 1 to the first node where it is located;
[0093] Step 410: The first node judges whether the lock ID corresponding to the shared resource 1 is stored in the first node and the lock ID has not been allocated. If so, execute step 480; otherwise, execute step 420;
[0094] Step 420: the first node sends a lock permission request to access the shared resource 1 to the second node;
[0095] In this step, the client 1 and the second node are located in the first storage device.
[0096] Step 430: The second node judges whether the lock identifier corresponding to the shared resource 1 is stored in the first node and the lock identifier is not allocated, if so, execute step 470, otherwise, execute step 440;
[0097] Step 440: the second node sends a lock permission request for accessing the shared resource 1 to the lock manager;
[0098] Wherein,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com