Safety communication method and system
A technology for secure communication and communication keys, which is applied to the usage of multiple keys/algorithms, user identity/authority verification, etc., and can solve problems such as difficulty in ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
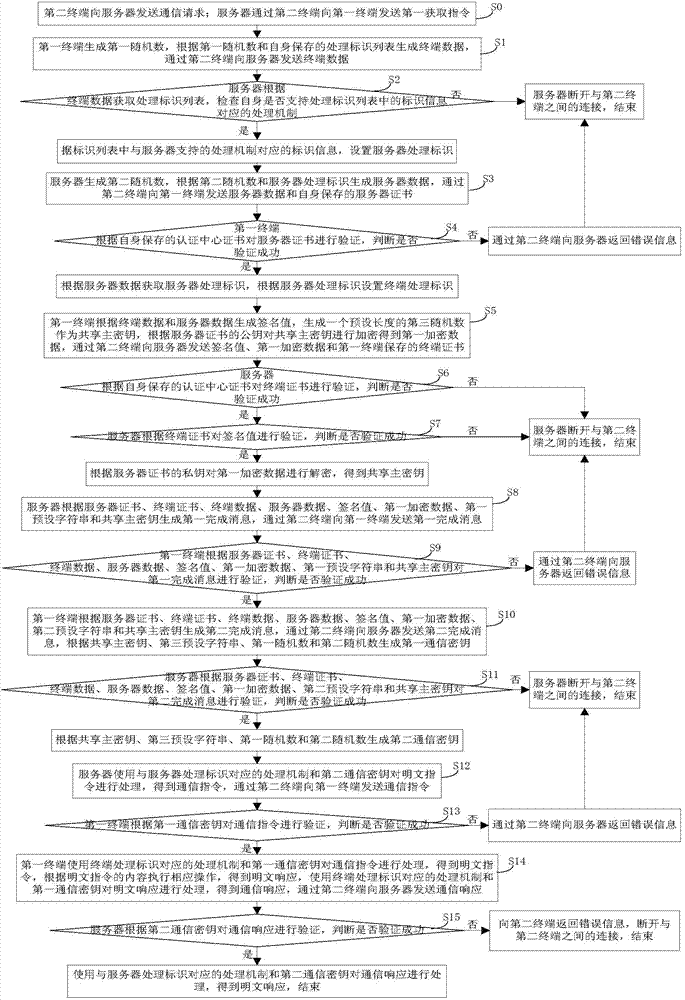
[0151] Embodiment 1 of the present invention provides a secure communication method, such as figure 1 shown, including:
[0152] Step S0: the second terminal sends a communication request to the server; the server sends the first acquisition instruction to the first terminal through the second terminal;
[0153] Specifically, the first acquisition instruction is an instruction to acquire terminal data;
[0154] Step S1: the first terminal generates a first random number, generates terminal data according to the first random number and the processing identification list stored by itself, and sends the terminal data to the server through the second terminal;
[0155] Step S2: The server obtains the processing identification list according to the terminal data, checks whether it supports the processing mechanism corresponding to the identification information in the processing identification list, and if so, sets the server processing identification according to the identificati...
Embodiment 2
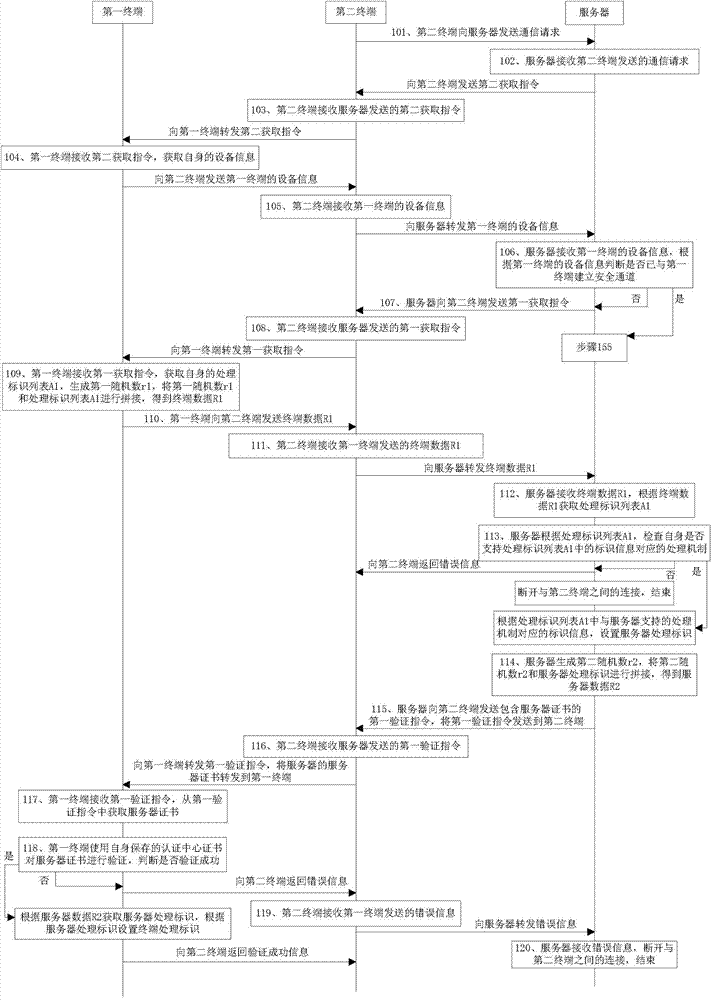
[0171] Embodiment 2 of the present invention provides a secure communication method, such as Figure 2 to Figure 4 shown, including:
[0172] When the second terminal receives the command to communicate with the server, the following steps are performed:
[0173] Step 101: the second terminal sends a communication request to the server;
[0174] Step 102: The server receives the communication request sent by the second terminal, and sends a second acquisition instruction to the second terminal;
[0175] Specifically, the second acquisition instruction is an instruction to acquire the device information of the first terminal;
[0176] Step 103: the second terminal receives the second acquisition instruction sent by the server, and forwards the second acquisition instruction to the first terminal;
[0177] Step 104: the first terminal receives the second acquisition instruction, acquires its own device information, and sends the first terminal's device information to the seco...
Embodiment 3
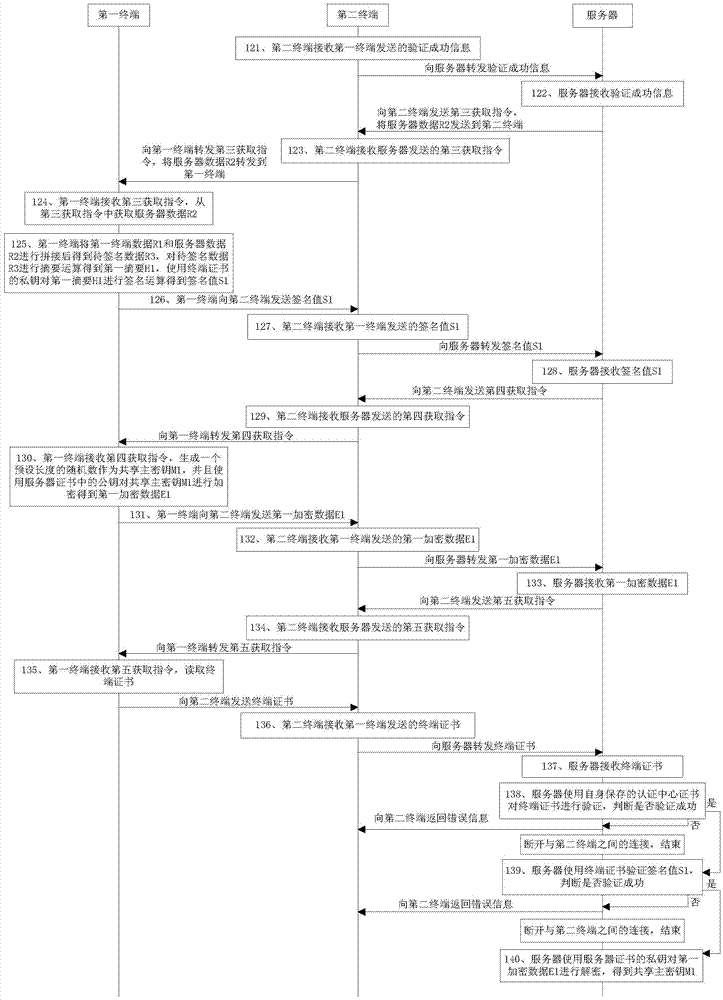
[0343] Embodiment 3 of the present invention provides a secure communication method, such as Figure 5 shown, including:
[0344] Step 201: When the first terminal receives the second acquisition instruction, acquire its own device information, and send the first terminal's device information to the server through the second terminal;
[0345] Specifically, the second acquisition instruction is sent by the server to the second terminal, and the second terminal forwards it to the first terminal; the second acquisition instruction is an instruction to acquire the device information of the first terminal;
[0346] Step 202: When the first terminal receives the first acquisition instruction, obtain its own processing identification list A1, and generate a first random number r1, and splicing the first random number r1 and the processing identification list A1 to obtain terminal data R1;
[0347] Specifically, the first acquisition instruction is sent by the server to the second t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com