Abnormal event monitoring method and system based on radio frequency identification positioning
A radio frequency identification positioning and abnormal event technology, applied in computer parts, collaborative devices, instruments, etc., can solve problems such as inability to effectively monitor abnormal events, save time and resources, and reduce negative effects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
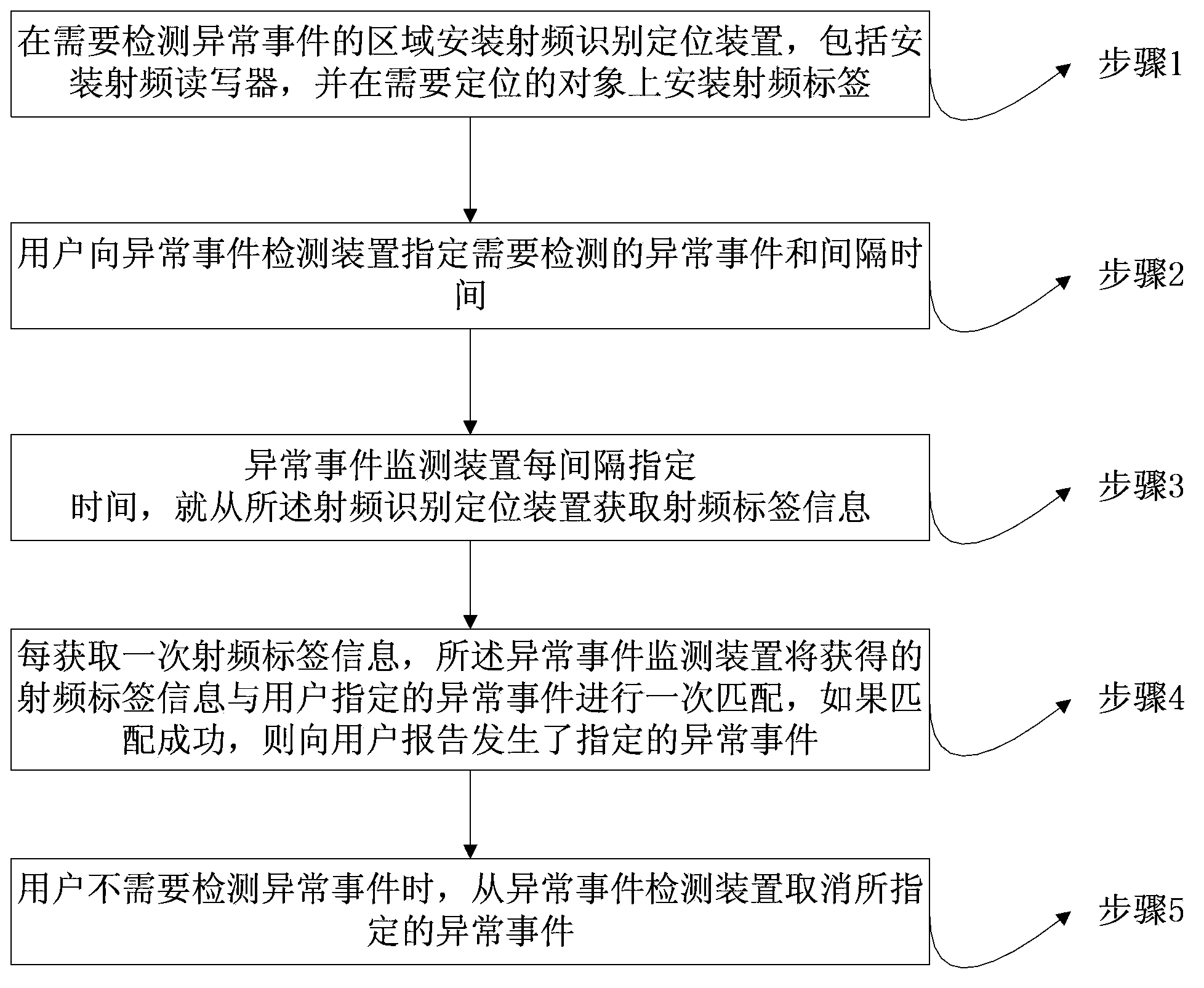
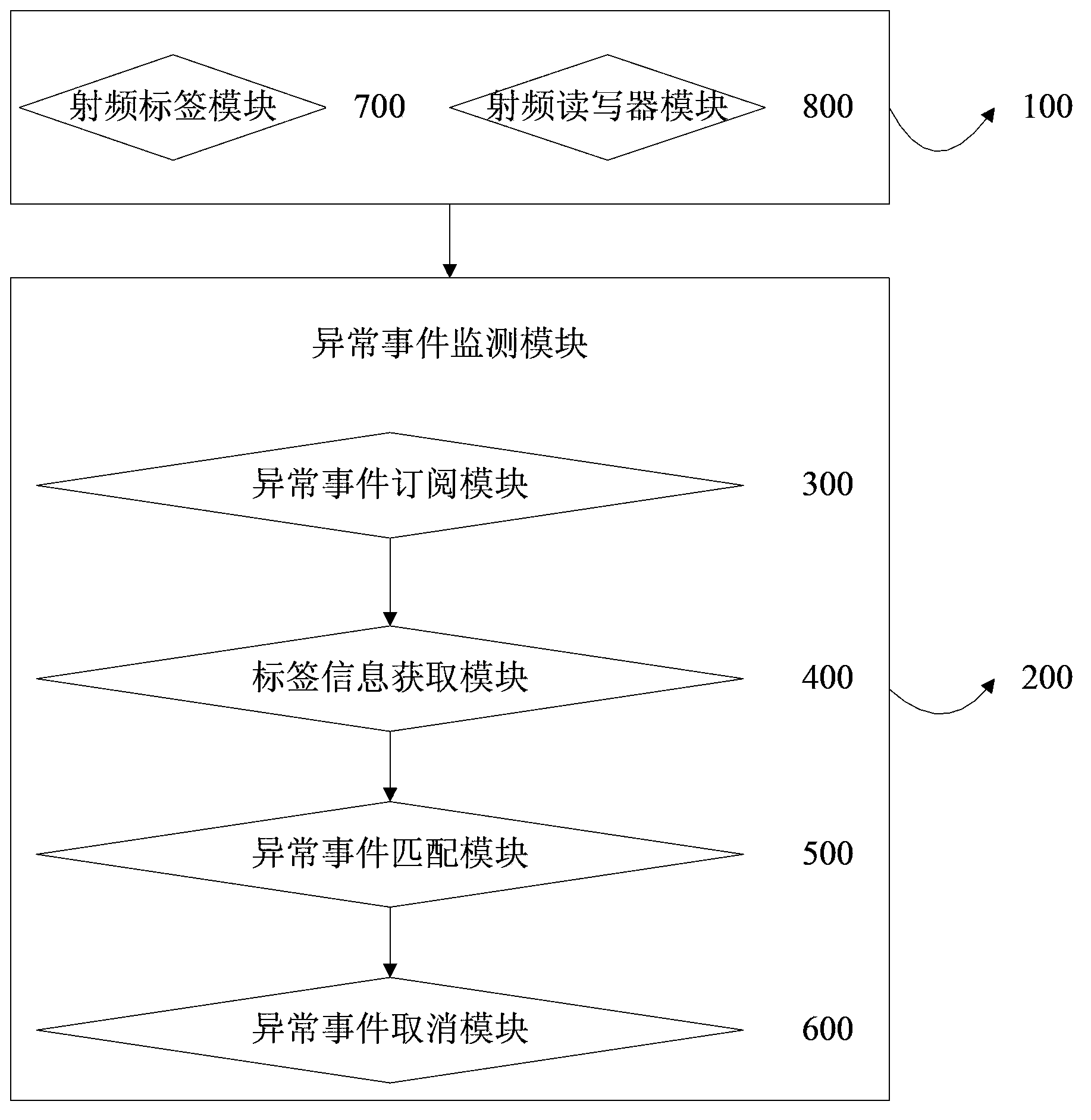
[0037] figure 1 It is a flow chart of the abnormal event monitoring method based on radio frequency identification positioning of the present invention. Such as figure 1 As shown, the method includes:
[0038] Step 1, install a radio frequency identification positioning device in the area where abnormal events need to be monitored, including installing a radio frequency reader, and installing a radio frequency tag on the object to be located;
[0039] Step 2, the user specifies the abnormal event and time interval to be monitored to the abnormal event monitoring device;
[0040] Step 3, the abnormal event monitoring device acquires radio frequency tag information from the radio frequency identification positioning device every specified time interval;
[0041] Step 4, each time the radio frequency tag information is obtained, the abnormal event monitoring device matches the obtained radio frequency tag information with the abnormal event specified by the user, and if the ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com