Method for effectively transferring label ownership in RFID system
An effective transfer and ownership technology, which is applied in the field of information security, can solve the problems of complete label transfer, failure to realize ownership transfer, etc., and achieve the effect of protecting user privacy, reducing work costs, and not easy to leak
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
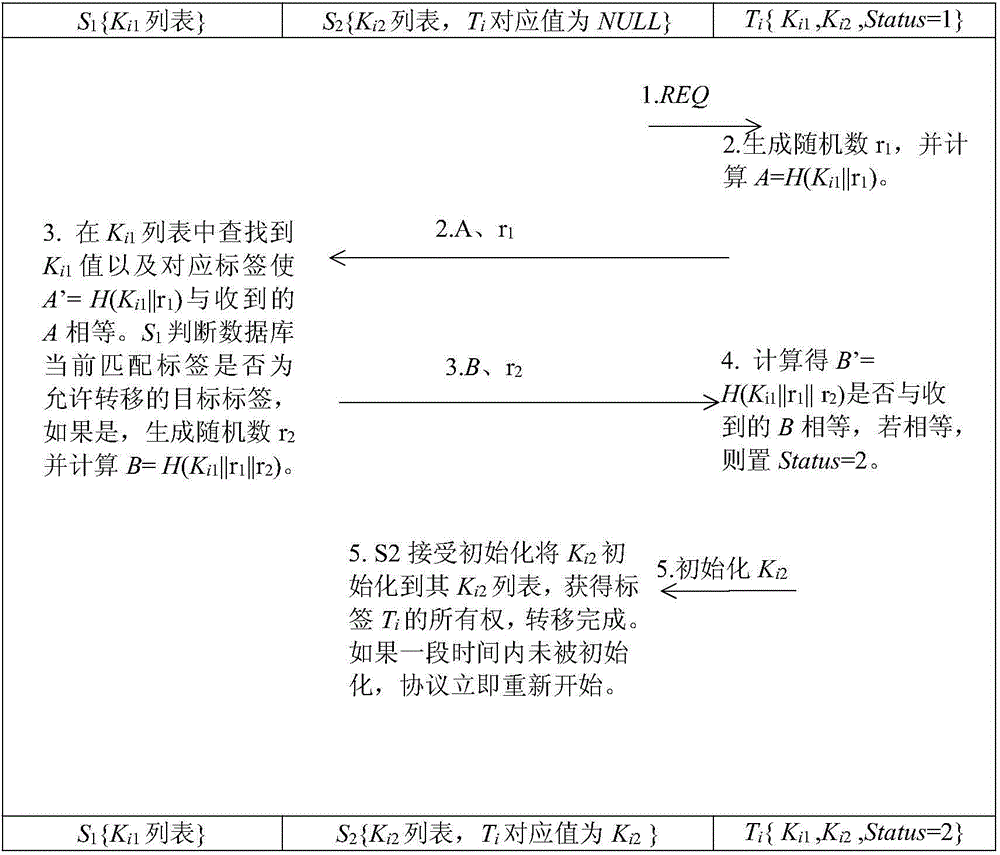
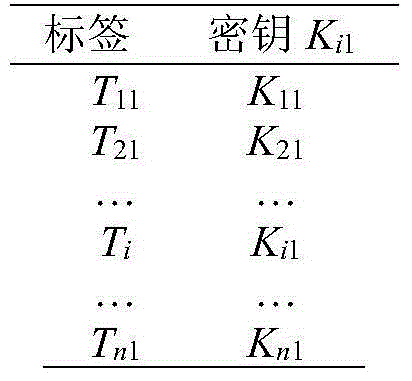
[0023] The present invention uses Status to identify who the current owner of the tag is, adopts a challenge response mechanism, and realizes the ownership transfer process by sending messages between the tag and the old and new owners, and designs a safe, simple and efficient RFID tag ownership transfer protocol. The complete protocol includes the process of making a transfer request, authenticating the identity of the tag, approving the transfer request, authenticating the identity of the original owner, and initializing the new owner. where S 1The list of keys stored in is shown in Table 1.
[0024] Table 1: S 1 List of keys stored in
[0025]
[0026] S before transfer 2 The key list stored in is shown in Table 2.
[0027] Table 2: S before transfer 2 List of keys stored in
[0028]
[0029] T i The communication data stored in is shown in Table 3.
[0030] Table 3: T i Communication data stored in
[0031]
[0032] Combined with the flow chart below (at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com