Power secondary system information security level protection online compliance detection method
A power secondary system, compliance detection technology, applied in the field of level protection, to achieve the effect of flexible expression, saving time and satisfying accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with specific examples.
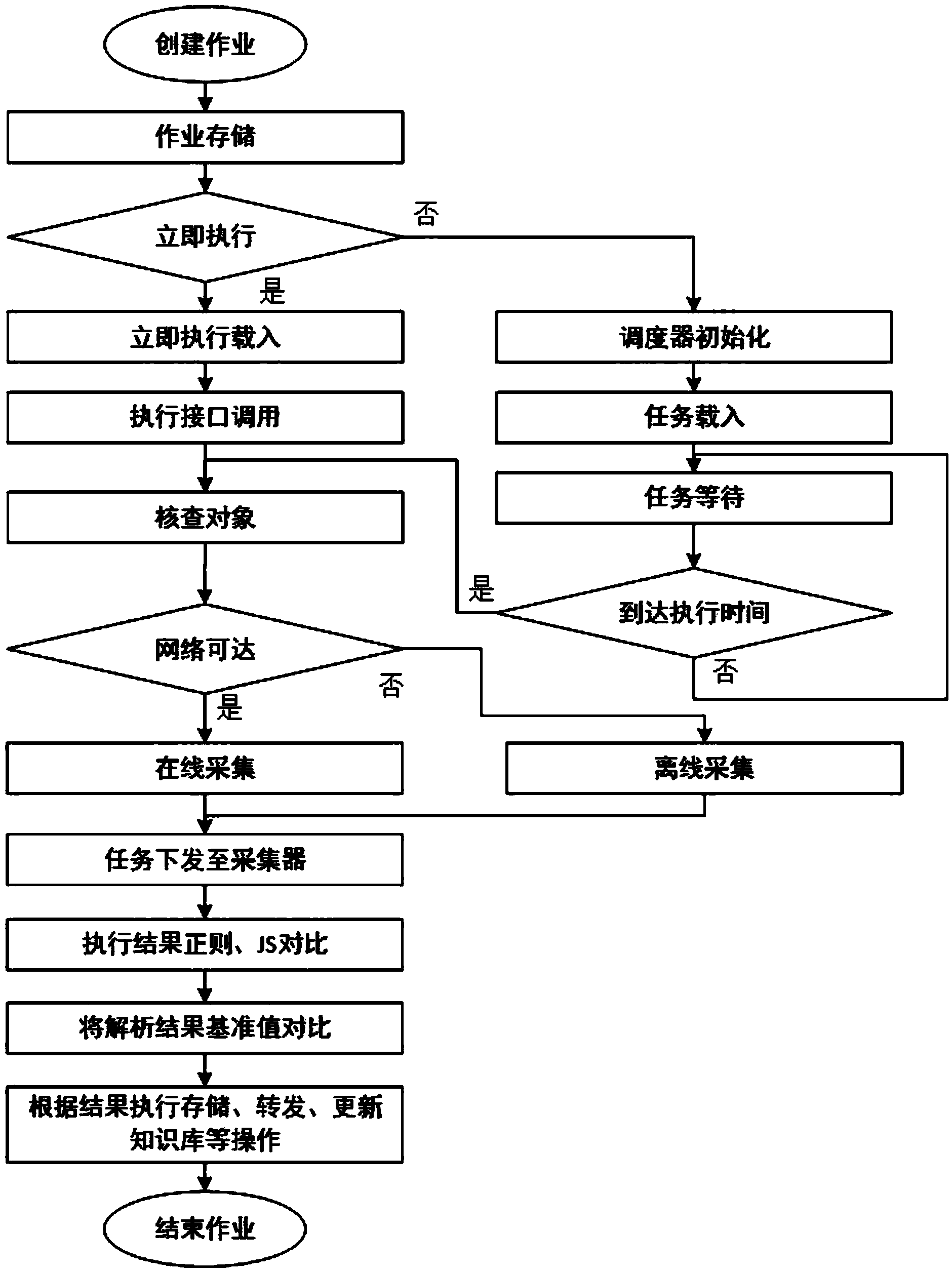
[0036] The online compliance detection method of the power secondary system information security level protection described in this embodiment is as follows: figure 1 As shown, the specific process is as follows:
[0037] 1) Create a job and check whether the job needs to be executed immediately. If it needs to be executed immediately, directly call the execution interface, otherwise initialize the scheduler and wait for the task;
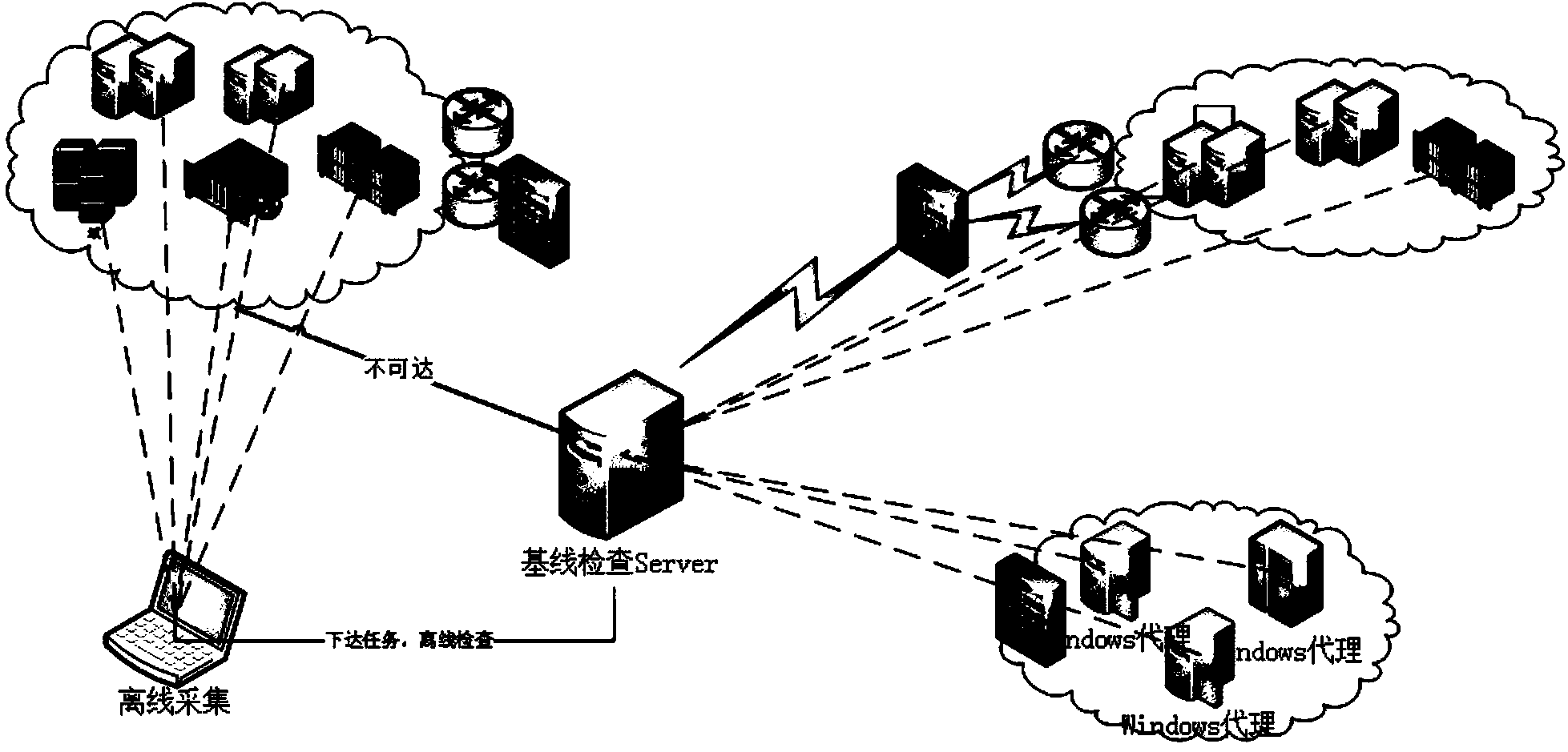
[0038] 2) After the job execution time is reached, check the number of objects and the number of collectors, and judge whether the target device is reachable in the network. If the device is connected to the network, use online collection, otherwise call offline collection;
[0039] 3) After the collection method is selected, the task is sent to the collector, and the collector obtains the target device information to realize the configuration bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com