Method for encrypting spatial network
An encryption method and space network technology, applied in the field of space network encryption, can solve the problems of security discount and high use cost, and achieve the effects of enhancing security, convenient operation and reducing use cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
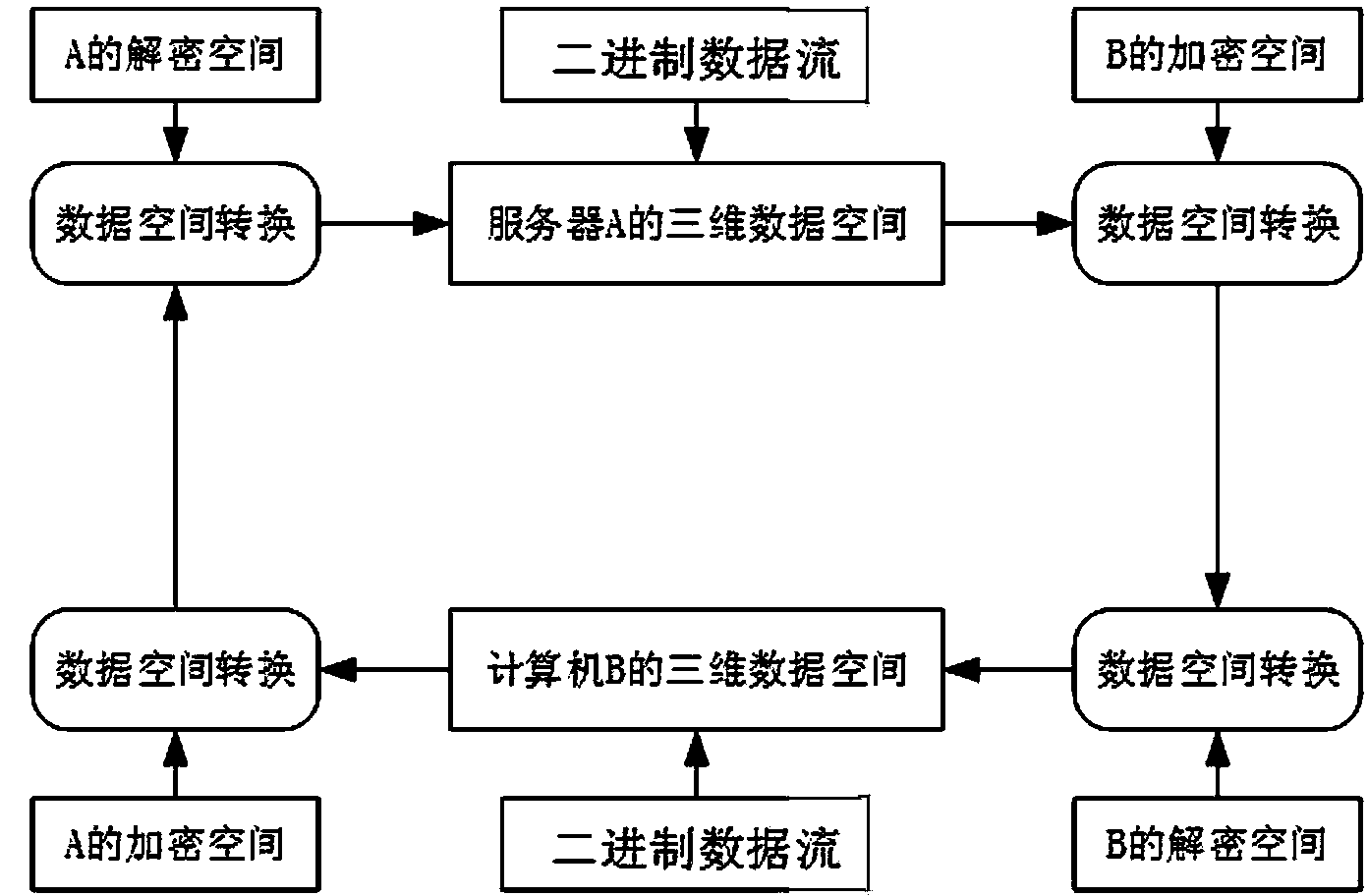
[0037] The specific steps for setting this encryption method are as follows:
[0038] Step 1: Computer B sends a session request to server A;
[0039] Step 2: Server A receives the request by listening to the port message, agrees to the session and creates a session connection;
[0040] Step 3: Server A calls the CreateSpaceEncoding function to create an independent encrypted space for computer B, and loads the preset encrypted space parameters of computer B through the SpaceEncoding function, encrypts the version information and timestamp of the space key currently used by server A, and then The encrypted message is returned to computer B together;
[0041] Step 4: Computer B obtains the return message from server A, calls the CreateSpaceDecoding function to create the decryption space of computer B, then calls the SpaceDecoding function to load the communication ciphertext and the preset decryption space parameters of computer B, and initializes the decryption spa...
Embodiment 2
[0063] The specific steps for setting this encryption method are as follows:
[0064] Step 1: Computer B sends a session request to server A;
[0065] Step 2: Server A receives the request by listening to the port message, agrees to the session and creates a session connection;
[0066] Step 3: Server A calls the CreateSpaceEncoding function to create an independent encrypted space for computer B, and loads the preset encrypted space parameters of computer B through the SpaceEncoding function, encrypts the version information and timestamp of the space key currently used by server A, and then The encrypted message is returned to computer B together;
[0067] Step 4: Computer B obtains the return message from server A, calls the CreateSpaceDecoding function to create the decryption space of computer B, then calls the SpaceDecoding function to load the communication ciphertext and the preset decryption space parameters of computer B, and initializes the decryption spa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com