A method for secure booting of embedded systems
An embedded system and secure boot technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of inability to achieve system update and mirror update, increase hardware overhead, and heavy equipment burden, so as to ensure secure boot. Integrity, reduce the difficulty of development, and ensure the credibility and integrity of the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
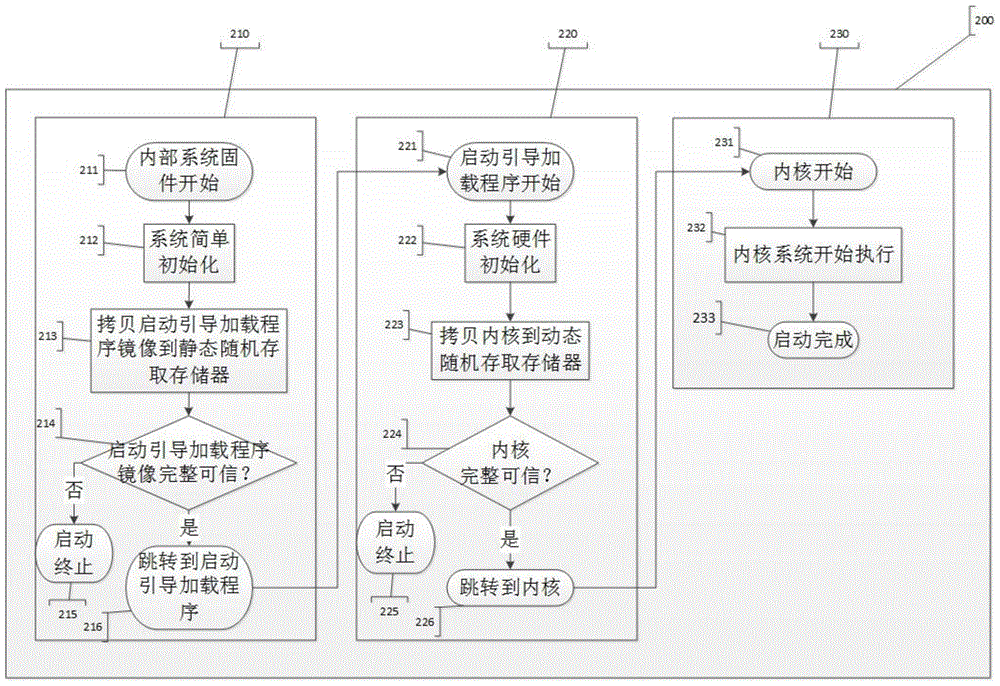
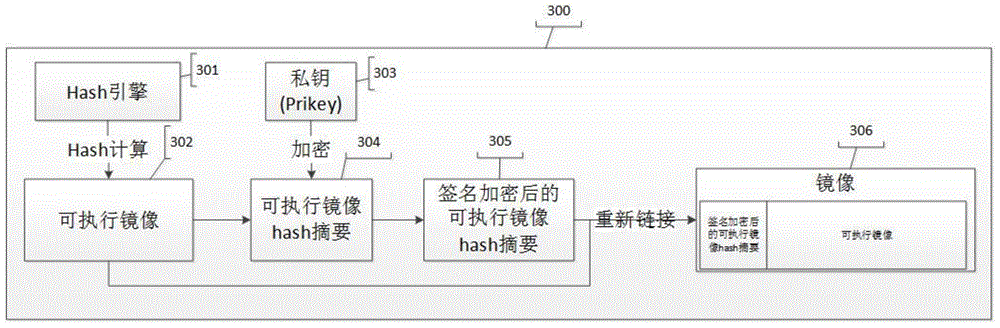
[0037] Next, combine the figure 1 , attached figure 2 , attached image 3 and attached Figure 4 The main realization principles, specific implementation methods and corresponding beneficial effects that can be achieved of the technical solution of the application of the present invention are described in detail.
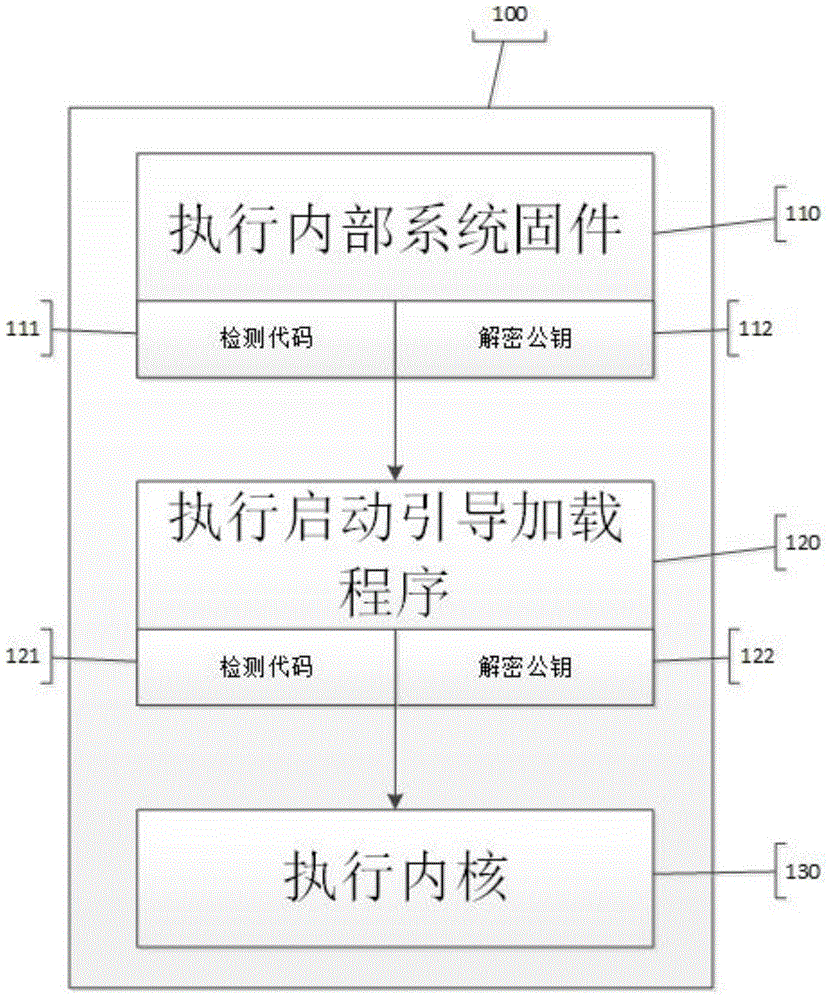
[0038] Reference attached figure 1 , is a diagram of a secure boot process used in the implementation case of this application.
[0039] Mark 111: the detection code in the internal system firmware, the detection code is mainly to detect the credibility and integrity of the bootloader image;
[0040] Identification 112: The decryption public key in the internal system firmware. The decryption public key is the public key paired with the private key used to encrypt the image header information of the bootloader during the image making process. It can only unlock the next stage of startup. Signature information in the header of the bootloader image.
[0041] Ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com