Screen lock based data protection method and device
A technology of data protection and screen lock, applied in the data protection device based on screen lock, in the field of data protection based on screen lock, to achieve the effect of protecting security and preventing being cracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to further illustrate the technical means adopted by the present invention and the achieved effects, the technical solutions of the present invention will be clearly and completely described below in conjunction with the accompanying drawings and preferred embodiments.
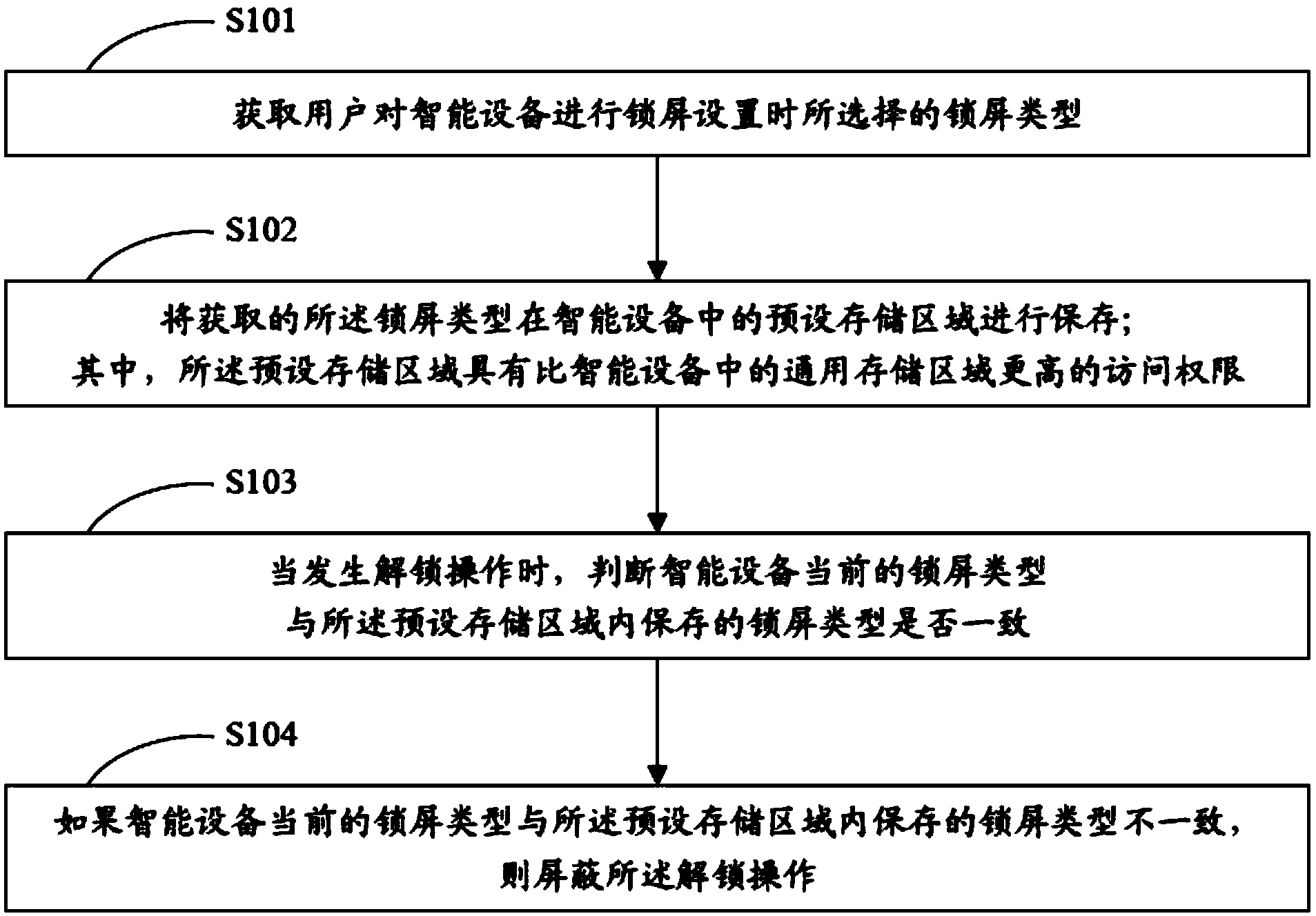
[0021] see figure 1 , is a schematic flow chart of the lock screen-based data protection method of the present invention.
[0022] The data protection method based on lock screen of the present invention comprises the following steps:
[0023] S101 acquires the lock screen type selected by the user when setting the lock screen of the smart device;
[0024] S102 Save the acquired lock screen type in a preset storage area in the smart device; wherein, the preset storage area has higher access authority than the general storage area in the smart device;
[0025] S103 When an unlocking operation occurs, determine whether the current lock screen type of the smart device is consistent with the lock...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com